Blog for
General
popular topics:
network security cloud security SASE reporting Cloud Adoption zero-trust backhaul secure Internet GDPR compliance virtual desktop infrastructure (VDI) internet access speed cloud connector agent Ransomware network perimeter Zero Trust Network Access packet capture on-prem web proxy appliances plan Redirect YouTube Security Information and Event Management (SIEM) Microsoft Cloud App Security (MCAS) Switching to iboss MDM CASB SD-WAN REvil Kayesa executive order cyber hygiene subscription objects primitives rules conditions risk dashboard cloud connected inventory count Restricted Mode Allow List override block pages country block file uploads iOS iPad Safari Google Classroom Chromebook ChromeOS keyword filter Android Always-on VPN Lockdown mode Wessex Water Rapid deployment cloud-based web security security layers migration to the cloud SIEM Data security Remote device security Cloud Access Security Broker block Dropbox block OneDrive block box.com block Google Drive Reports logs event viewer timeframe callout scheduling reports dashboard IPSec GRE dedicated IP WCCP Tunneling log tuning Block YouTube HD Microsoft Azure Secured Virtual Hubs Microsoft Virtual Hubs VirtualHubs Internet Security Azure Secured Virtual Hubs iboss platform version FireEye Cloud PAC script Apple TLS Apple SSL Knowledgebase Knowledge base GeoZone 9.8.27 malware cloud-hosted ISO standards throttle video UI GUI user interface UX Next Generation User Interface Faster page loads Instant Search Autosuggestion admin console next-gen cloud admin console EA Sports Data Breach Colonial Pipeline JBS Healthcare HIMSS Microsoft 365 Microsoft partnership reverse proxy API CASB Remote Browser Isolation RBI Cybersecurity Awareness Month cybersecurity awareness Be Cyber Smart FedRAMP ATARC Cybersecurity civil cyber fraud vulnerabilities DLP Data Loss Prevention Cloud App Isolation Exact Data Match Defenders Network Behavior crisis management NIST ZTNA Containerization Apache Log4j Log4Shell Threat Landscape Cyber Threats hackers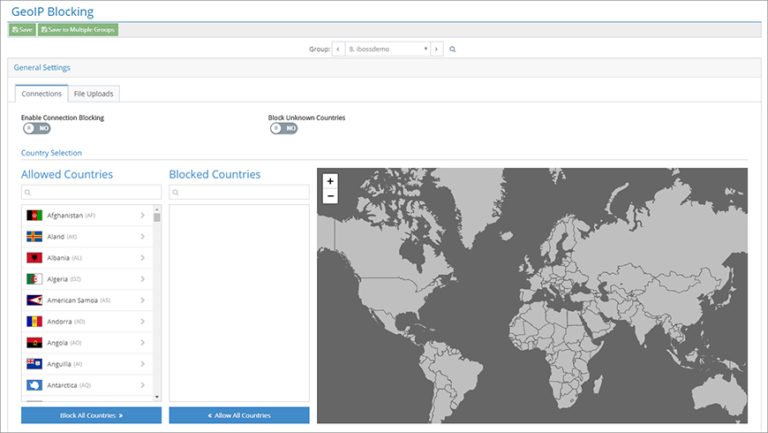
May 24, 2019
Block Network Connections or File Uploads to Specific Countries
The Internet may be global, but do your users need to access every single country in the...
country
block
file uploads
May 16, 2019
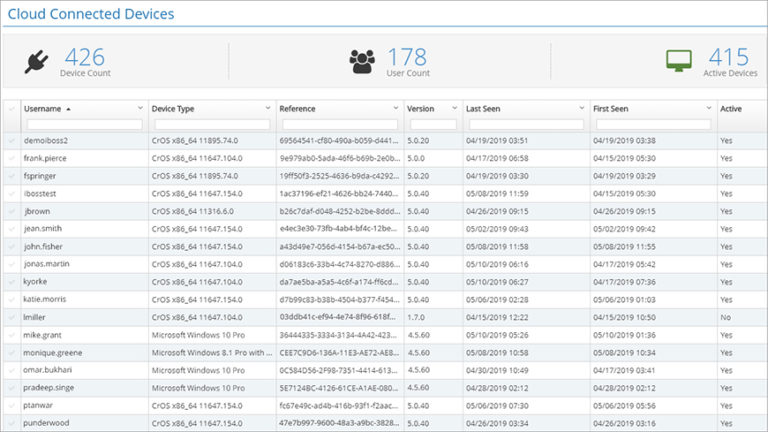
Inventory Your Cloud Connected Devices and Revoke Their Internet Access
How do you maintain an inventory of your cloud connected devices when your organization spans multiple states...
count
inventory
cloud connected
May 16, 2019
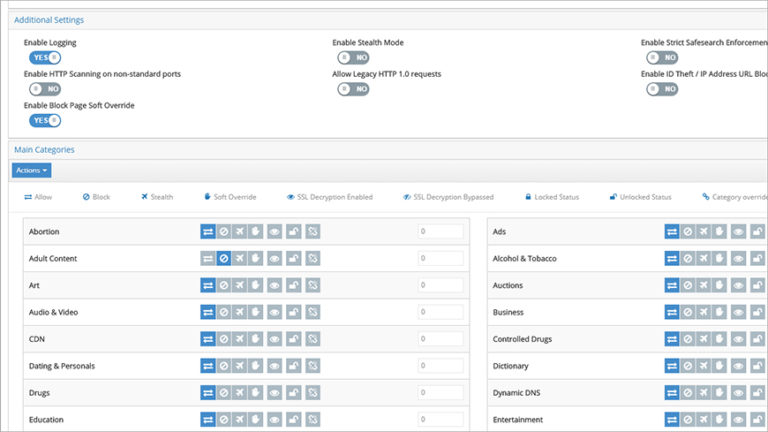
Empower Trusted Users to Override Website Blocks
How do you empower trusted network users to override website blocks independently?
Consider these scenarios:
A user unexpectedly...
override
block pages
May 13, 2019
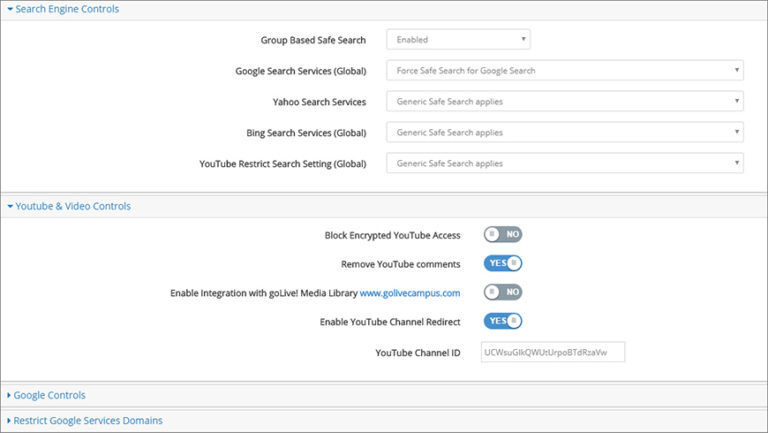
Remove YouTube Comments, Route Users to Your YouTube Channel, and Bypass Restrictions for Individual Videos
Do these YouTube experiences look familiar?
You visit YouTube to locate a specific video, only to be...
Allow List
Restricted Mode
YouTube
Redirect
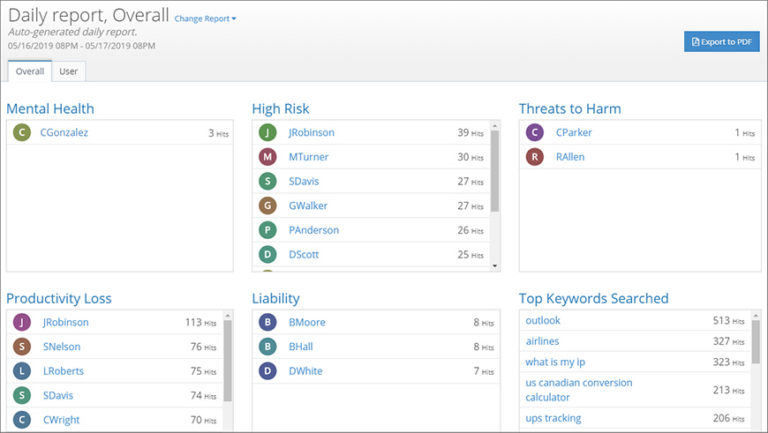
May 9, 2019
How to Identify High-Risk User Activity and Instantly Generate a Detailed Report
Do these stories look familiar?
You receive an urgent request for a report that details the recent...
risk dashboard
reporting
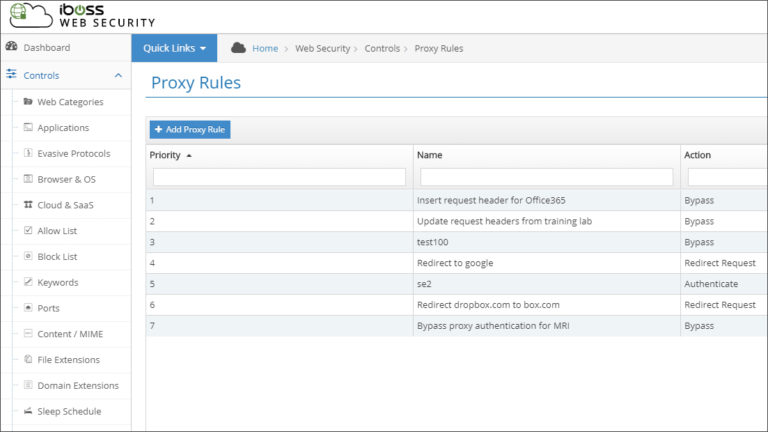
May 9, 2019
Redirect or Modify User Network Traffic Automatically by Creating Custom Rules
No two networks are exactly alike. This means that you must occasionally find workarounds for challenges and...
conditions
rules
primitives
objects
Redirect



