All resources, such as applications, data and services, are protected and are inaccessible without going through the iboss Zero Trust SASE
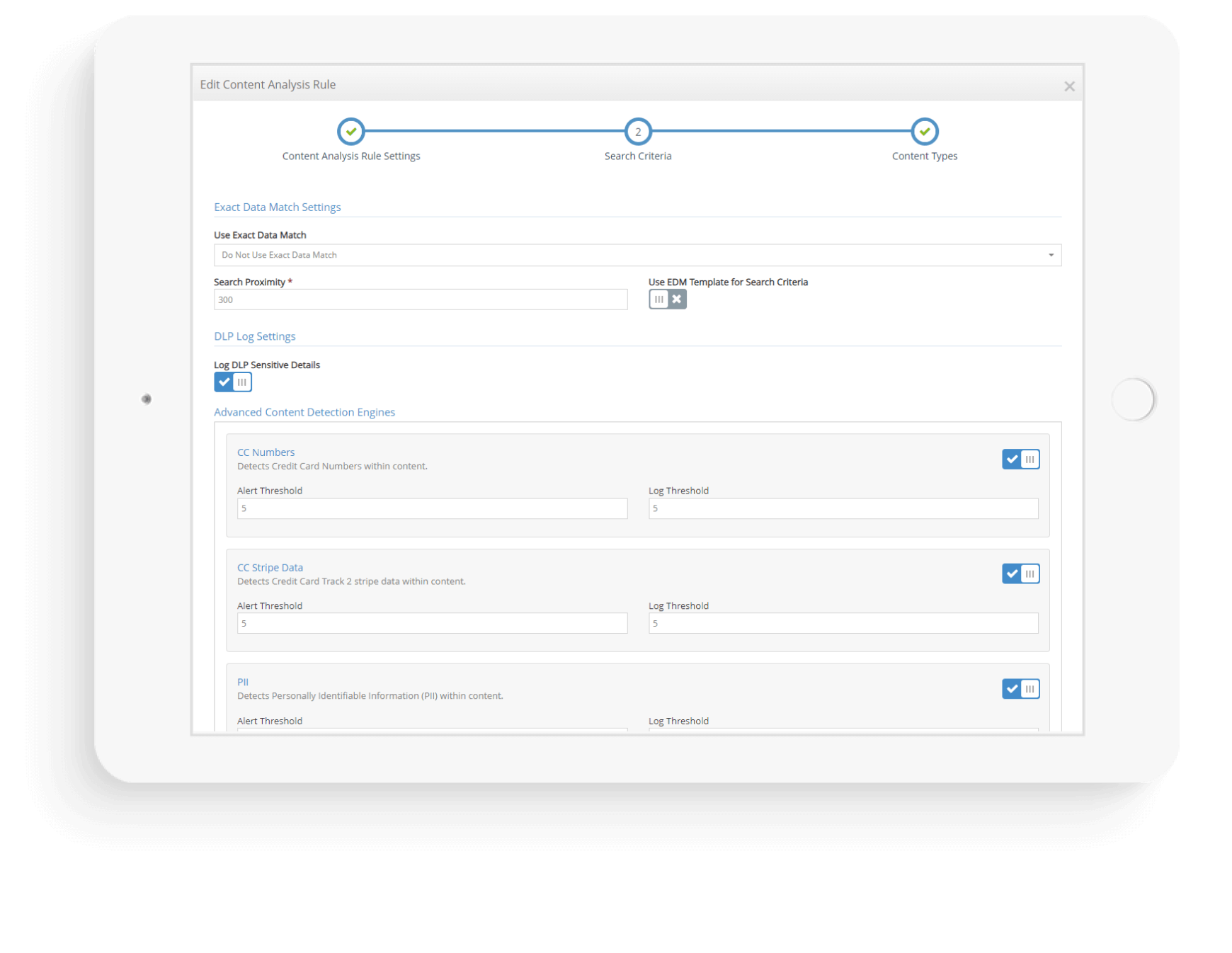
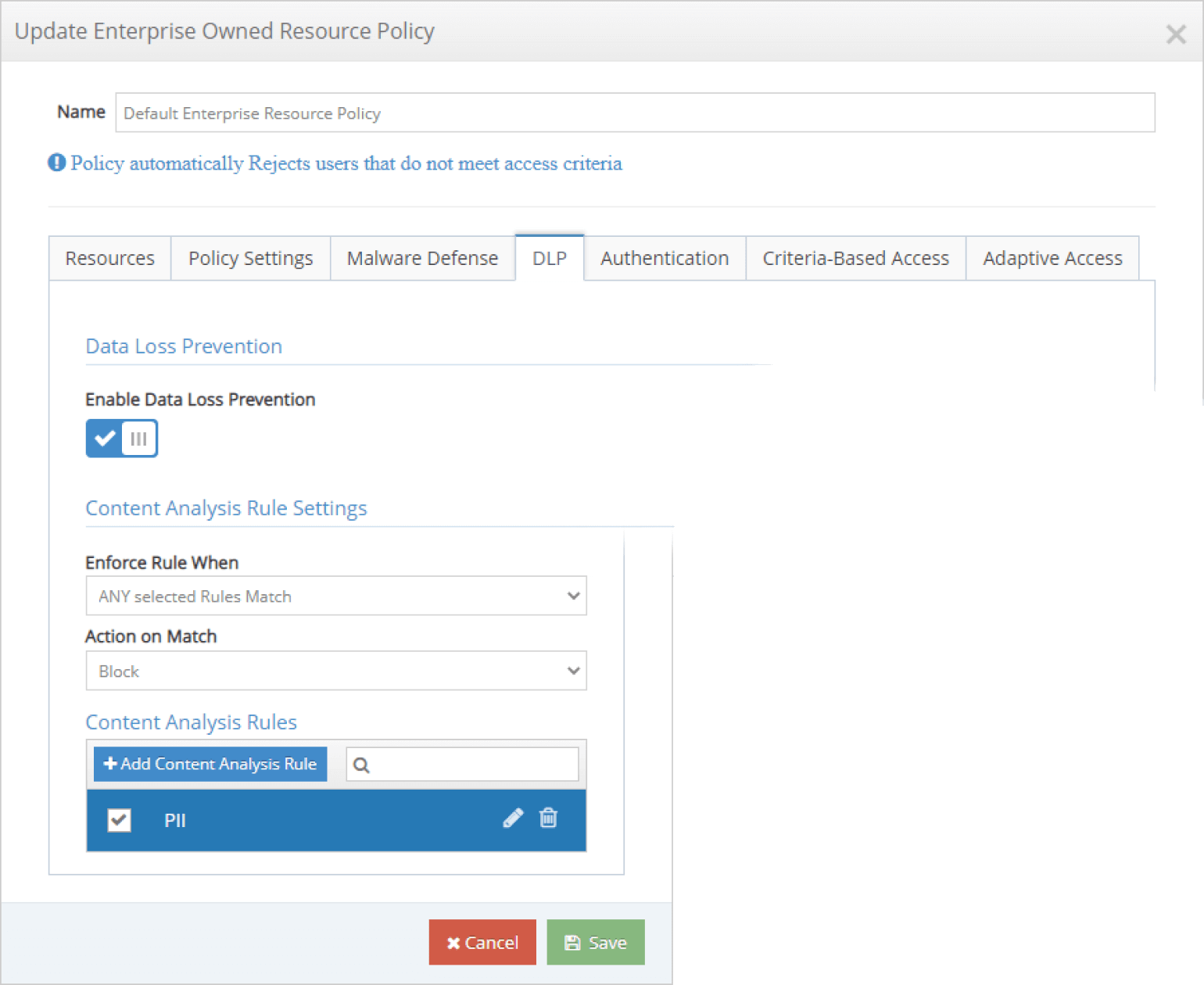
The iboss Zero Trust Secure Access Service Edge has full content inspection capabilities for data loss prevention, including the ability to scrape spreadsheets, analyze Microsoft Word documents and inspect deep into web page content data. As information is exchanged between users, sensitive resources and the public cloud, the iboss Zero Trust Secure Access Service Edge is analyzing the transfers with full context to prevent data loss. Data Loss Prevention capabilities also include Exact Data Match, or EDM, to find exact records within content. With the ability of the iboss Zero Trust Secure Access Service Edge to be close to the user and close to the resource, data loss prevention can be accomplished regardless of where the user works or the resource resides.
Inspect deep inside content for sensitive information and personal data
The iboss Zero Trust Secure Access Service Edge inspects full content, including content on documents, spreadsheets, web pages and SaaS applications. With access to the full content when data is transferred between users and applications, the ability to apply data loss prevention rules that are capable of searching for personal data and sensitive information is possible. The iboss platform inspects data as it moves between applications, devices and users and enforces policies that ensure data only resides where it is compliant and secure.
The data loss prevention algorithms run natively within the iboss cloud platform and are optimized for performance. They are applied to the full content during data transfers to ensure full context is available when searching for matches. With the iboss Zero Trust Secure Access Service Edge, users are able to connect directly to business-critical applications while data loss prevention policies are enforced in the cloud.
The data loss prevention engine has built-in algorithms for information such as:
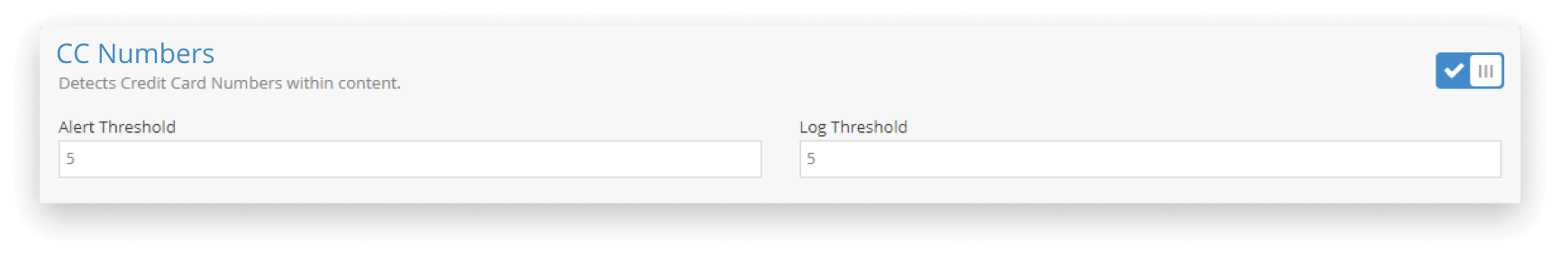
- Credit Card Numbers
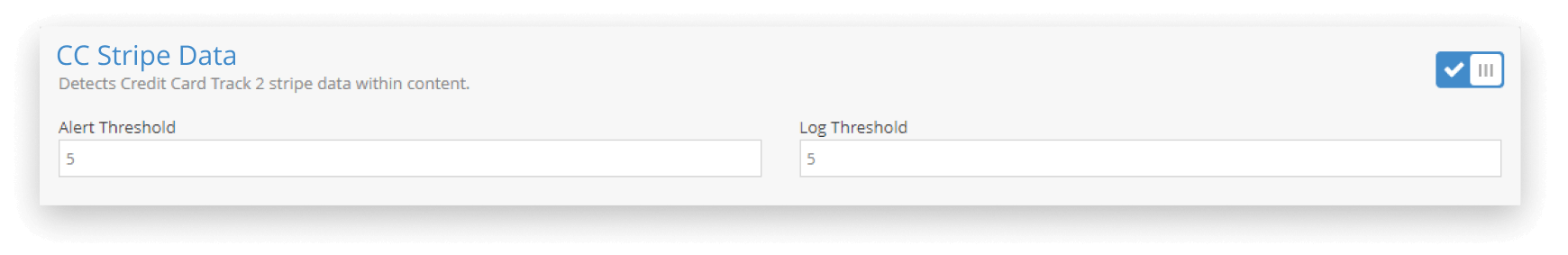
- Credit Card Stripe Data
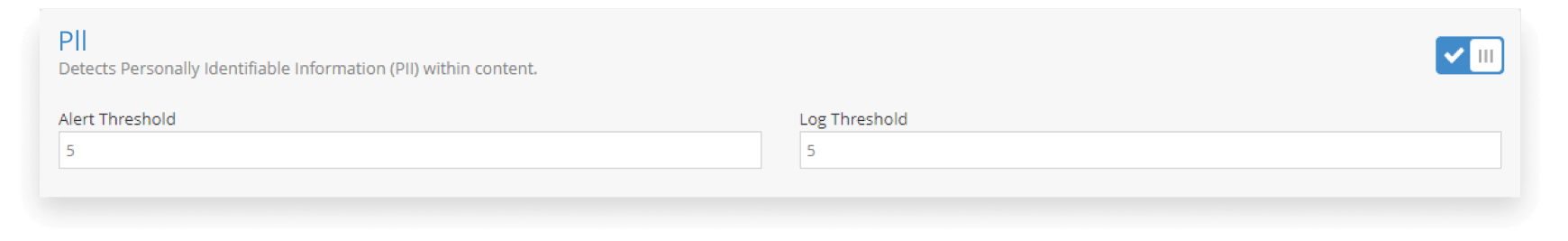
- Personal data such as phone numbers and email addresses

Data Loss Prevention policies can be applied to users, groups and resources
The dynamic policy engine within the iboss Zero Trust Secure Access Service Edge allows data loss prevention policies to be applied effectively when needed. Data loss prevention policies can be linked to specific sensitive resources, to specific users or to specific groups of users. Different data loss prevention policies can also be applied depending on the protection or compliance scenario. Group membership is tied directly to Azure AD, Okta, Ping or any other identity provider that supports SAML so that data loss prevention policies can be created easily and effectively.
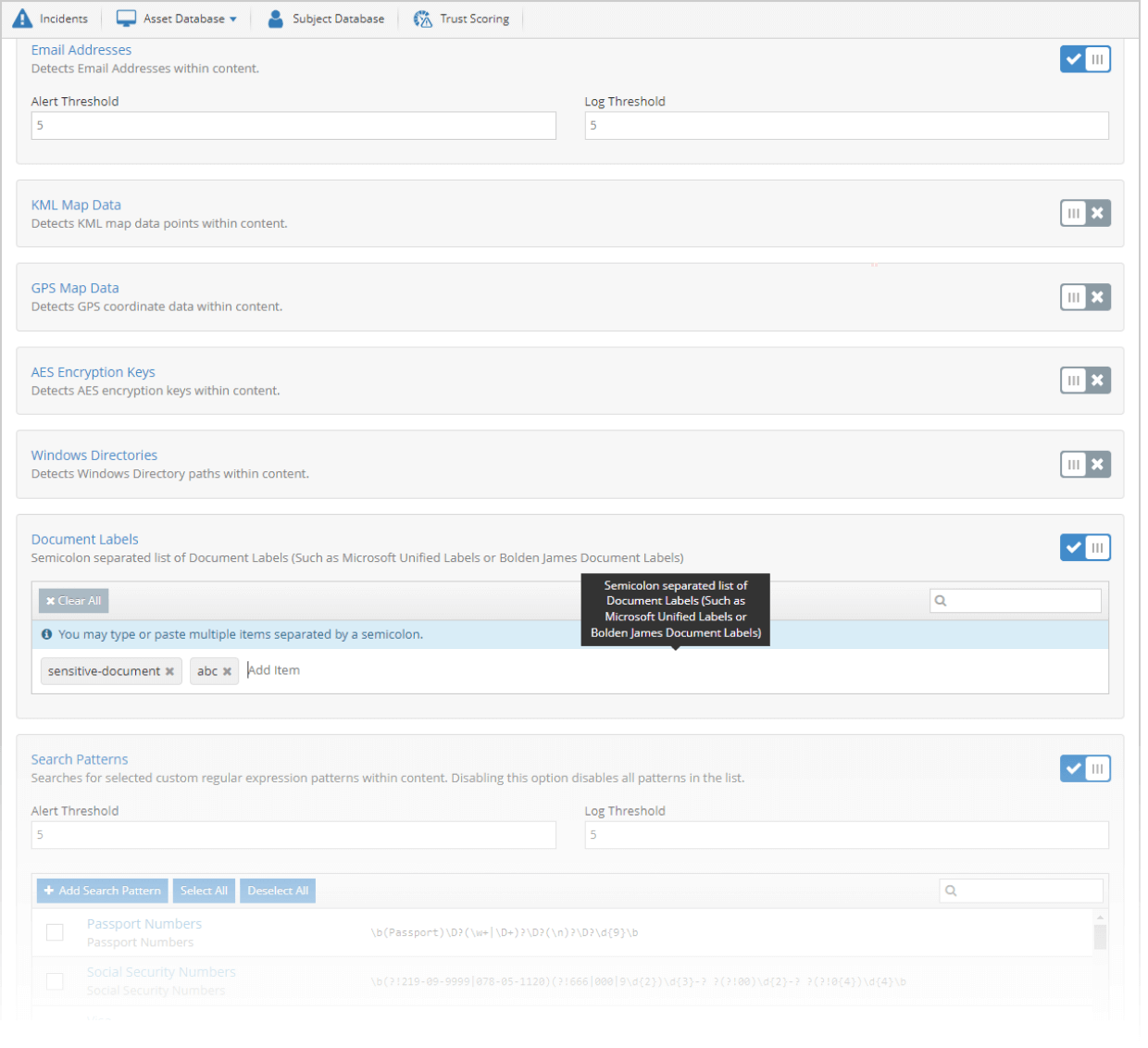
Reads document labels to apply data loss prevention rules, including labels from Microsoft Information Protection
Reads document labels to apply data loss prevention rules, including labels from Microsoft Information Protection
The iboss Zero Trust Secure Access Service Edge is capable of extracting and reading document labels to apply data loss prevention rules depending on the type of labeled content that is being transferred. The content analysis engine can inspect labels from Microsoft Information Protection (MIP) or other document labeling systems such as Fortra’s Classifier Suite (formerly Boldon James). When a specific label is encountered for sensitive data that is being transferred to a non-compliant location, the iboss can prevent the transfer eliminating the risk. Different data loss prevention rules can be created to match various document labels and take different actions depending on the situation being addressed.

Supports regular expressions for custom match patterns
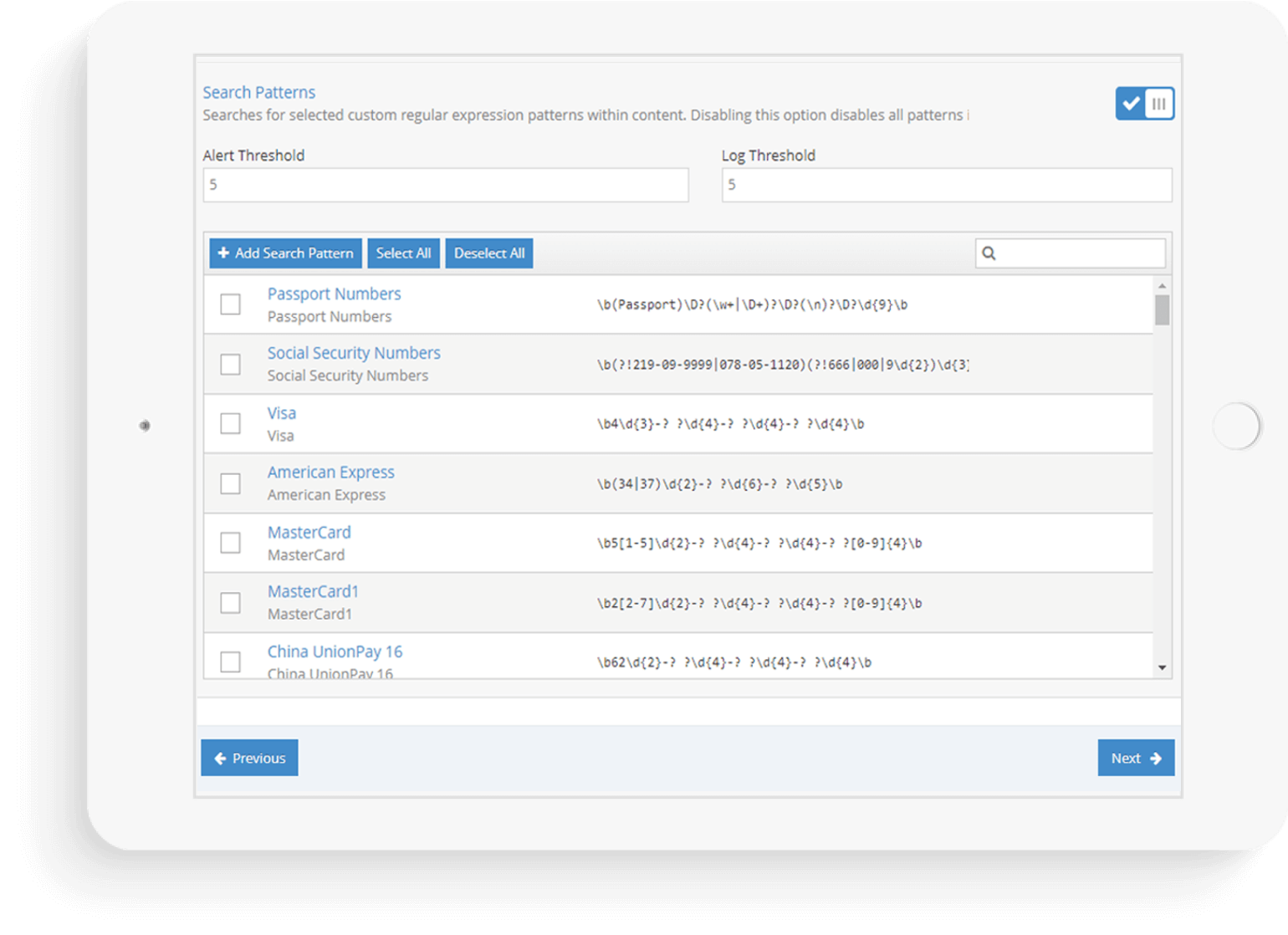
Supports regular expressions for custom match patterns
The iboss Zero Trust Secure Access Service Edge supports the use of regular expressions so that any type of content can be matched in cases that custom patterns are necessary. These search patterns will be applied to document text, including document formats such as Microsoft Word and Microsoft Excel. Regular expressions will apply to content within encrypted HTTPS connections when decryption of content is enabled within the iboss platform.
Exact Data Match capable of handling extremely large data sets
Exact Data Match capable of handling extremely large data sets
The iboss Zero Trust Secure Access Service Edge also supports Exact Data Match, or EDM, so that specific words or phrases can be matched within content. This is a powerful solution for organizations that have specific database records, such as patient information or credit card numbers, and want to ensure those specific records to not leak resulting in data loss. The iboss Exact Data Match capability can handle hundreds of millions of records and is designed for scale and data security.
Offline data indexing is possible with the iboss indexing tool which will hash the sensitive records prior to being leveraged for Exact Data Match within the iboss platform. The indexing tool ensures that data is not plain text readable and is protected from brute force attacks. The indexer can process the data set offline and also upload the pre-indexed data automatically. It’s designed to run on any platform, including Linux and Windows, and can be included with bash script processing to eliminate human interaction with the indexed data.
Multiple Exact Data Match templates can be used as well with each template containing any number of columns with varying data types. There is no limit to the number of columns that can be configured and unlike Zscaler, the iboss Exact Data Match engine does not count each column as a row when considering maximum number of records. The iboss platform can do any number of columns and hundreds of millions of rows to support vast Exact Data Match data sets.
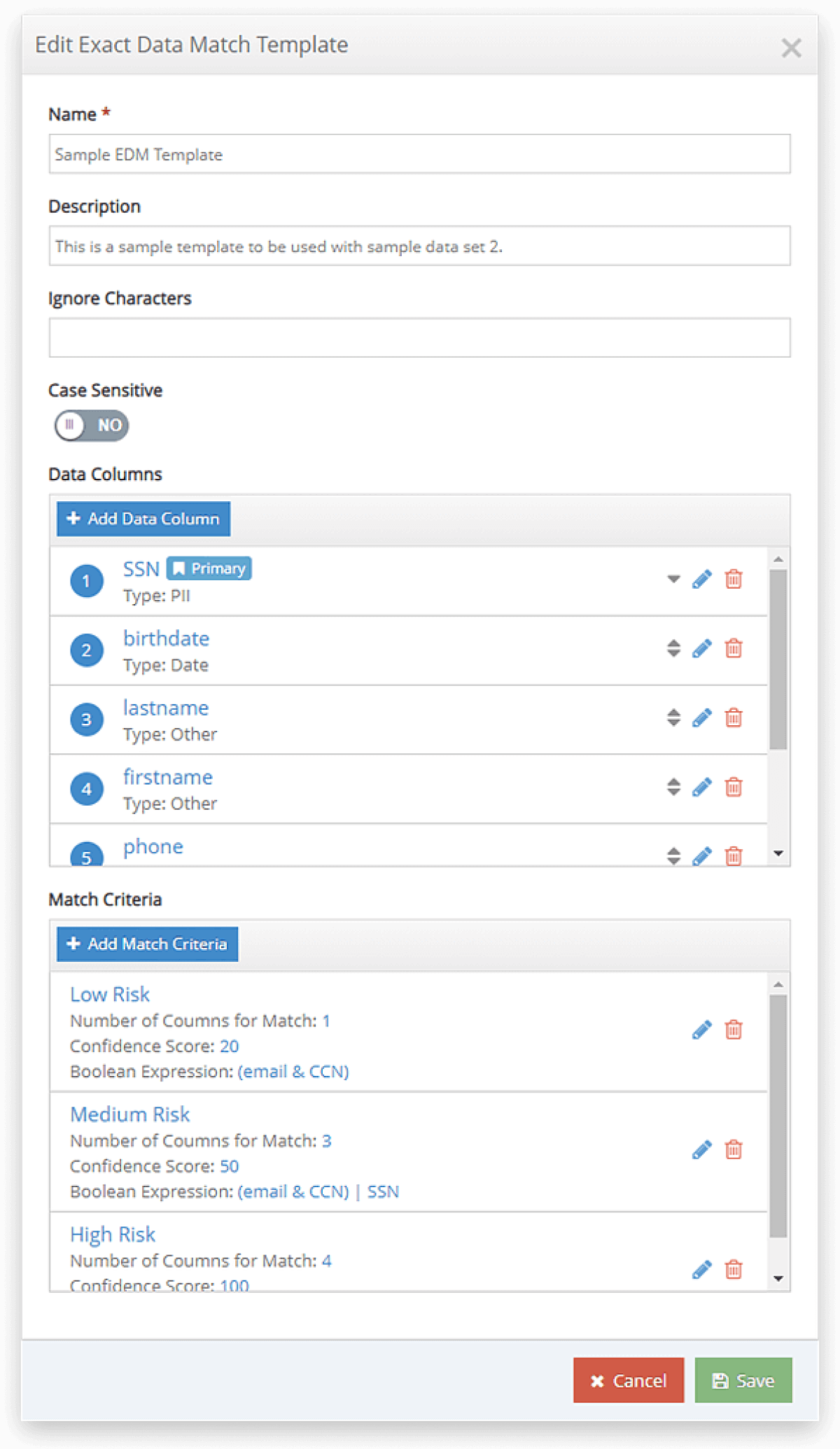
Exact Data Match also supports match criteria with boolean expressions so that a match is considered only when the boolean expression is met which derived from the multiple columns being matched. Complex boolean expressions are supported and multiple match criteria are supported as well. When a match criteria is met, a confidence score can be assigned to get more context in the likelihood of a breach.
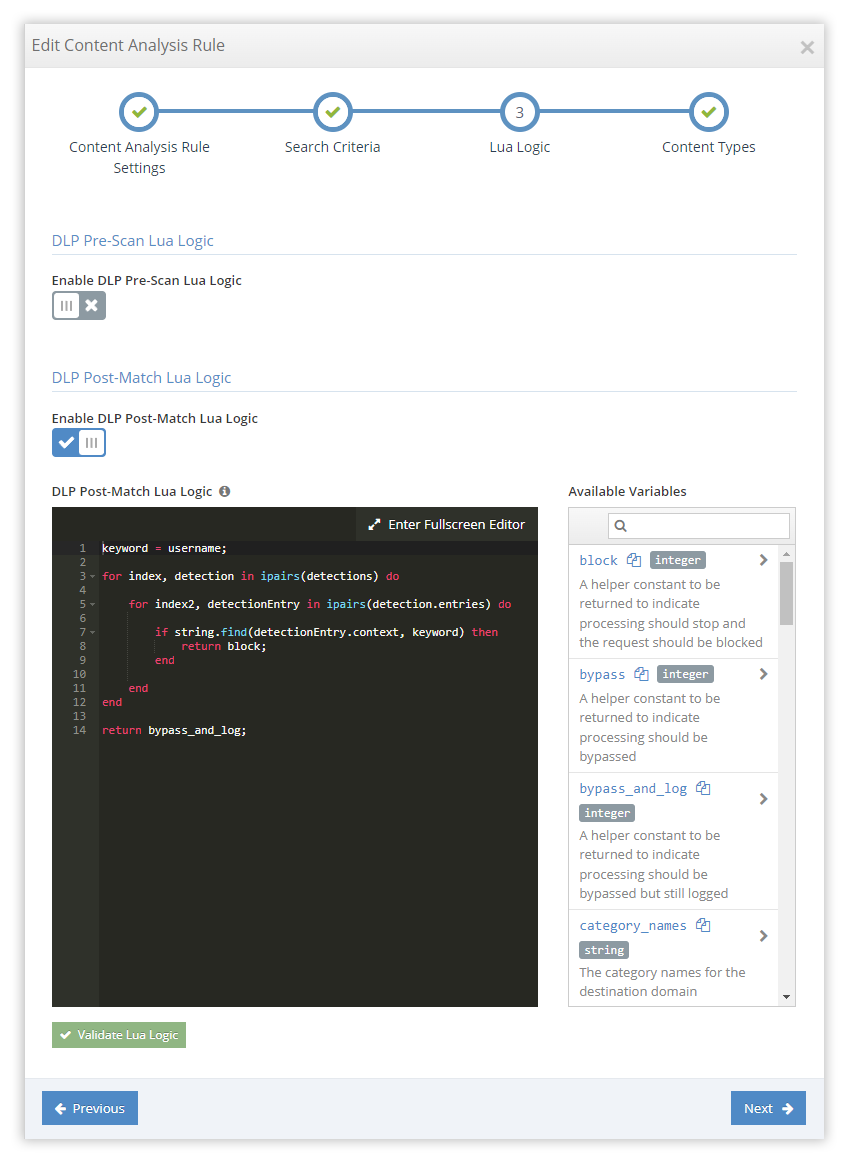
Reduce Complexity and False Positives with Pre and Post-Scan Lua Logic
iboss elevates Data Loss Prevention (DLP) through its pre and post-scan Lua Logic feature, utilizing a sophisticated IDE text editor for script creation. This functionality enables the crafting of custom DLP policy logic by allowing administrators to develop Lua scripts that execute before and after the scanning process.
Pre-scan Lua logic prepares data for scanning by filtering out irrelevant information, significantly cutting down on system strain and false positives. This step customizes data inputs based on complex criteria, making the scan more efficient and focused.
Post-scan Lua logic comes into play after the scan, offering a means to sift through results with additional criteria. It automates responses based on the outcomes, enhancing decision-making processes and tailoring actions in line with organizational policies.
By integrating both pre and post-scan Lua logic, iboss provides a dynamic approach to minimize false positives and streamline DLP policy management. This approach not only offers flexibility and efficiency but also aligns DLP operations closely with an organization’s specific requirements, ensuring data protection is both precise and effective.
Post-scan Lua logic comes into play after the scan, offering a means to sift through results with additional criteria. It automates responses based on the outcomes, enhancing decision-making processes and tailoring actions in line with organizational policies.
By integrating both pre and post-scan Lua logic, iboss provides a dynamic approach to minimize false positives and streamline DLP policy management. This approach not only offers flexibility and efficiency but also aligns DLP operations closely with an organization’s specific requirements, ensuring data protection is both precise and effective.
Enhanced Desktop App Notifications
The iboss platform’s Enhanced Desktop Notifications capability bridges the gap between user interaction and security enforcement, all while maximizing convenience. As part of the iboss Zero Trust SASE, the feature complements the platform’s dynamic security by pushing essential notifications directly to the user’s desktop.
Whether the need arises for advanced authentication in non-browser applications or immediate attention is needed due to DLP violations, the Enhanced Desktop Notifications feature delivers clear, interactive alerts. Unlike traditional systems that often struggle with non-browser-based applications, this iboss capability simplifies the process. It allows users to validate their identity in applications like SSH with the same modern SAML authentication methods used in browser-based apps.
The feature also addresses DLP violations in an innovative way. Even if a violation is detected within a custom widget in a modern app, this feature ensures that the violation alert is clear and actionable, overcoming the limitations of browser-based notifications. Furthermore, it enables end-users to request exceptions within the notification modal itself, saving time and facilitating a smoother workflow.
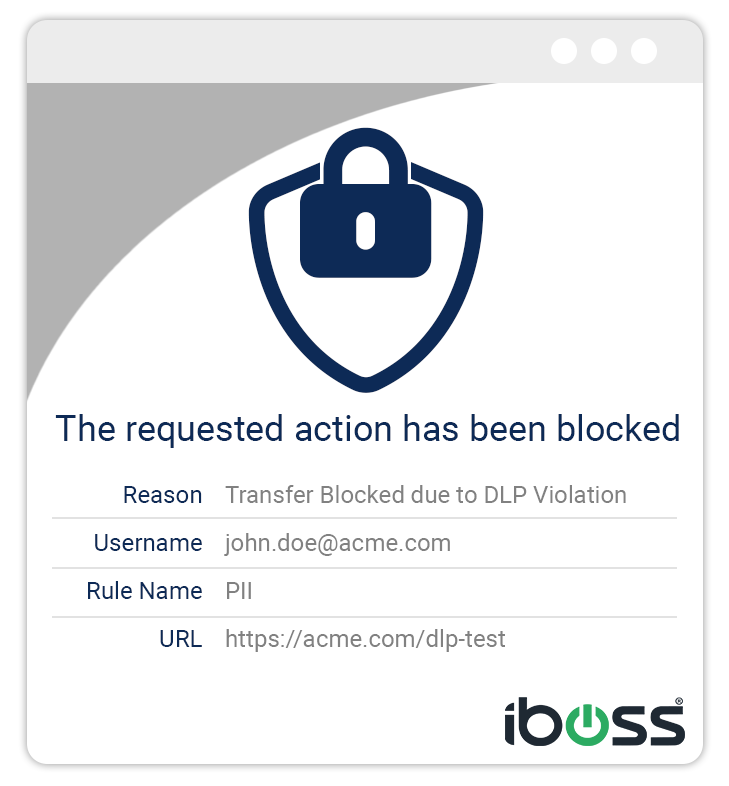
The Enhanced Desktop Notifications feature is a unique extension of the iboss Zero Trust SASE platform. It is designed to provide instant, unambiguous notifications to end-users, including step-up authentication requests for non-browser applications and alerts for Data Loss Prevention (DLP) violations. This feature offers users the option to request exceptions directly within the notification modal, facilitating real-time resolution of access issues.







