Integrates with
The iboss Zero Trust Secure Access Service Edge integrates with Identity Providers such as Azure AD, Okta, Ping and those that support SAML or OIDC. With this native integration, the iboss platform can determine which user is requesting access to resources and use this as a factor when determining whether to provide access. In addition, users are typically mapped to security groups or organizational units within the Identity Providers and these mappings can be leveraged as well to create group-based policies. Without iboss, Identity Providers can only authorize users at the time of login. However because iboss is a Zero Trust Security Service Edge, it can extend authorization to each interaction between a user and a protected resource which means access can be terminated as soon as risk increases or a device becomes infected. This reduces risk and response times to ensure additional damage is mitigated should a breach occur or a compromise attempt be detected.
Natively integrates with Azure AD, Okta, and Ping Identity Providers
The iboss Zero Trust Secure Access Service Edge integrates with popular Identity Providers such as Azure AD, Okta and Ping and automatically synchronizes users and groups so that they can be used for security policies and access logs. Dynamic access and security policies for CASB, malware defense and data loss prevention can be applied based on user and group membership making administrative management easier.
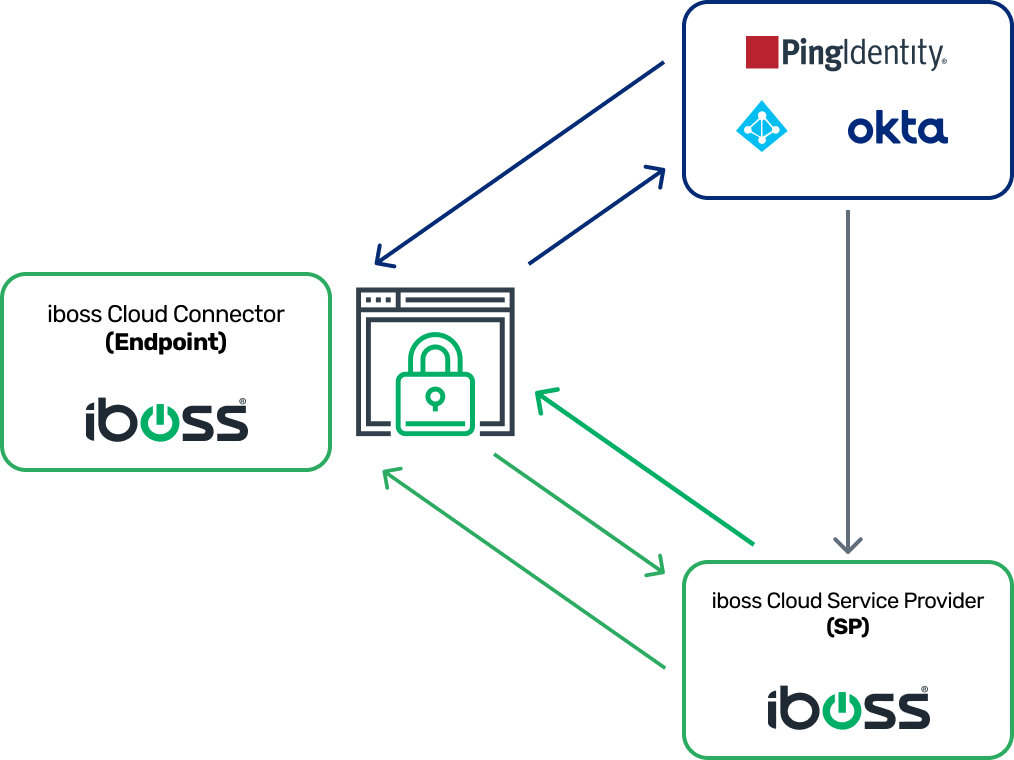
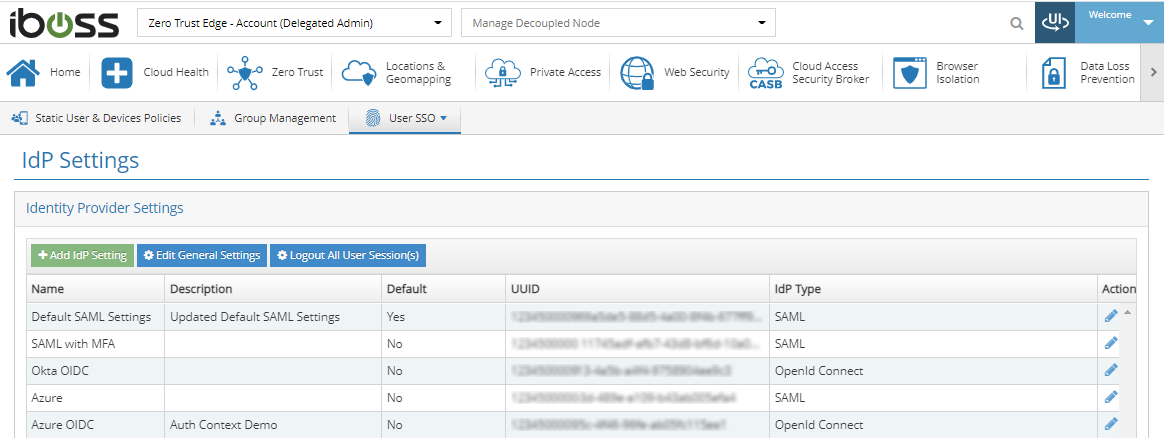
Integrates with any Identity Provider that supports SAML
The iboss Zero Trust Secure Access Service Edge also has the ability to integrate with any identity provider that supports the SAML protocol ensuring compatibility with virtually all identity providers that provide Federated Identity services. The integration will leverage the username and groups which are obtained automatically during the SAML login process which provides a great end-user experience while ensuring security and network teams get the appropriate security and access policies applied to resources.
Extends Authorization beyond the point of login to every resource interaction

Identity Providers only have the ability to authenticate and authorize users to access applications and services during the user login process. This leaves massive blind spots for security teams on the interactions between the users and sensitive resources as interactions with data and applications occur after login grants access. Since the iboss Zero Trust Secure Access Service Edge is the only path to protected data and applications, it can enforce authentication and authorization for each and every interaction to protected resources. This is the foundational principle of Zero Trust according to the NIST 800-207 Zero Trust Architecture and its the capability that the iboss platform provides. This substantially reduces risk by providing per-request access decisions that can terminate access to a resource if a device were to be breached as well as provide visibility to security teams by generating log events for every transaction.
Logs username and group from Identity Provider with every log event for better attribution
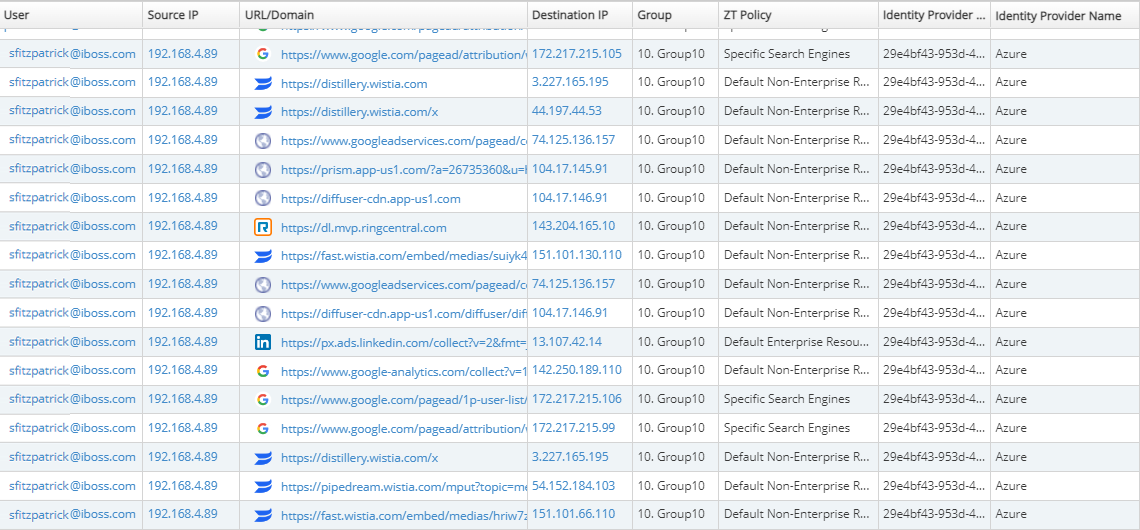
The iboss Zero Trust Secure Access Service Edge leverages the username and identity information obtained from Identity Providers and logs that information for every event generated by the platform. As users interact with resources, log events are continuously generated to capture those interactions. Having the username associated with log events means security teams can quickly associate who an event is associated with which reduces response times for risky situations or potential breaches. The log events are forwarded to any external SIEM or logging database so that the copy of the logs also contain the username attribution.
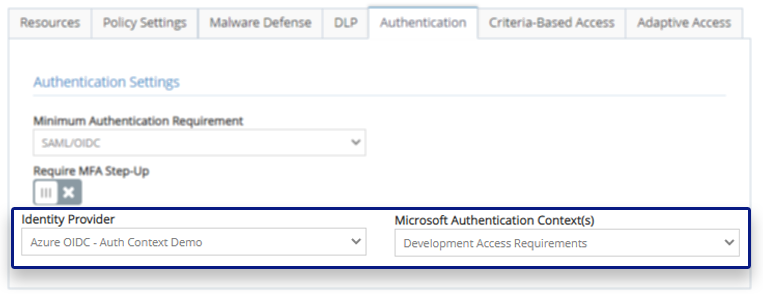
Microsoft Conditional Access provides additional criteria that can be applied when a user logs into an application which is used to determine whether access should be granted or denied to the protected resource. This is a powerful Microsoft capability because it allows administrators to add more identity confidence when providing access, such as whether or not a user leveraged Multi-Factor Authentication, or MFA, when logging into a resource. To make this capability more powerful, it can be combined with the iboss Zero Trust Secure Access Service Edge which extends conditional access beyond the point of login and applies these checks to every request, including those after login, to ensure continuous conditional access requirement checks. The iboss platform automatically synchronizes the Microsoft conditional access requirements and allows administrators to apply these to resources for various levels of conditional access requirements.
Integrated with Microsoft Conditional Access to provide continuous adaptive access decisions beyond login time
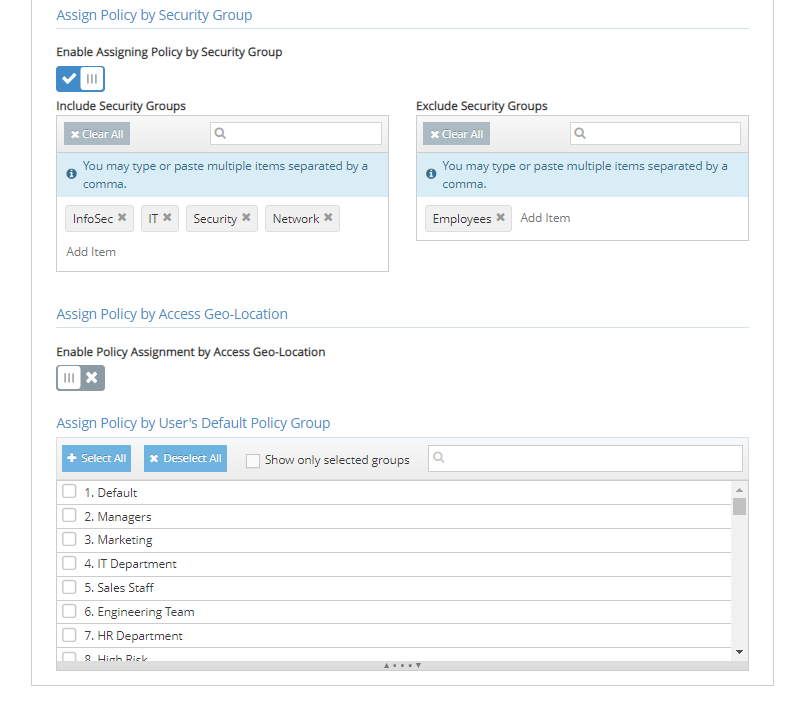
Leverages Identity Provider group assignments for security policy creation
The iboss Zero Trust Secure Access Service Edge automatically extracts user group membership from the Identity Provider so that security and access policies can be easily applied to sets of related users. This allows network and security teams to quickly leverage existing organizational structures and group policies which greatly reduces management overhead and implementation time.
Take the next step in shifting to the world’s largest security platform built for the future.
Sign up for a demo to see how the iboss Zero Trust SASE prevents breaches by making applications, data and services inaccessible to attackers while allowing trusted users to securely and directly connect to protected resources from anywhere.






