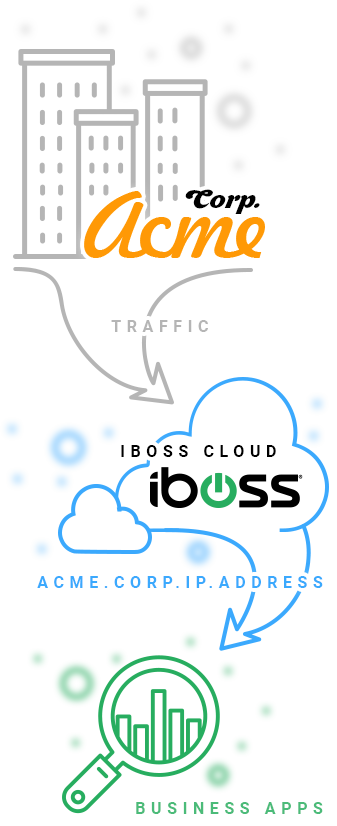
The iboss Cloud Platform provides unique source IP Address identity in the cloud so that existing policies that rely on them are maintained
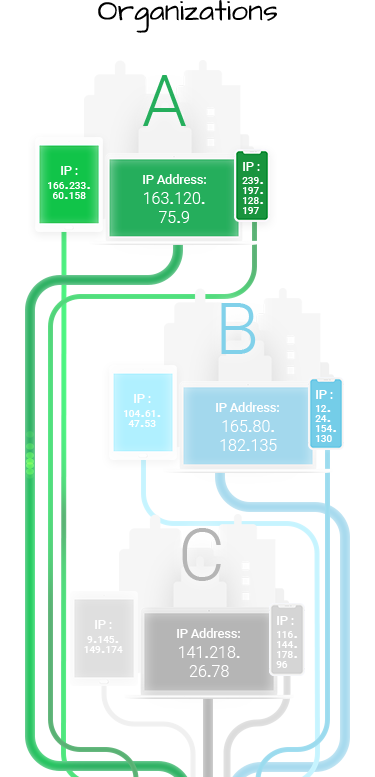
When traffic leaves an organization’s network destined to the cloud, the source IP Address of that traffic is uniquely associated with the organization. These addresses are typically assigned by the Internet Service Provider to the organization. This IP is used to restrict access to portals and connect to back-office networks.
The unique association between the source IP Address and an organization’s identity on the Internet has become an important aspect for integration due it’s use by IT departments to connect vendors and technology integrations. IT teams provide these IP Addresses to third-parties to connect the organization’s network and provide access to the resources provided by the third-party.

Maintain connections to back-office providers and third-parties which require your IP Address for connectivity
Back-office partners may require that an organization provide their unique Source IP Addresses in order to allow traffic from the organization to the back-office network. This becomes especially important in countries where regulations are in place that require Source IP Addresses to originate from within the country itself but still be unique to the organization.
In addition, organizations typically create Access Control Lists (ACLs) that are configured on firewalls and network equipment that rely on unique and dedicated source IP Addresses. This is a requirement that is typically required as web gateway appliances are eliminated and web security moves to the cloud.

Back-office partners may require that an organization provide their unique Source IP Addresses in order to allow traffic from the organization to the back-office network. This becomes especially important in countries where regulations are in place that require Source IP Addresses to originate from within the country itself but still be unique to the organization.
In addition, organizations typically create Access Control Lists (ACLs) that are configured on firewalls and network equipment that rely on unique and dedicated source IP Addresses. This is a requirement that is typically required as web gateway appliances are eliminated and web security moves to the cloud.
With the iboss Cloud Platform, organizations maintain unique and dedicated source IP Addresses which can be used to meet these requirements while moving to a cloud-based gateway platform. This reduces the complexity of migrating from legacy Secure Web Gateway Appliances to the cloud by maintaining critical IT requirements for connectivity.
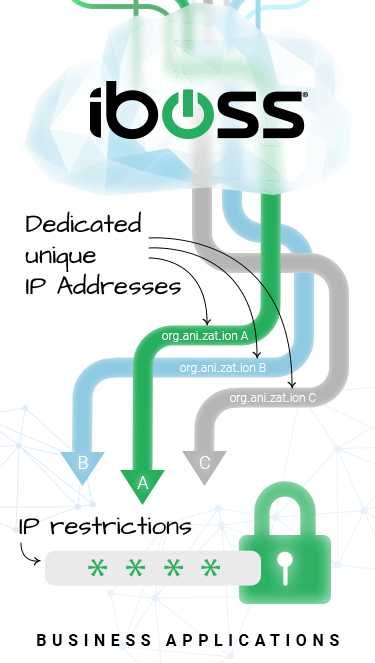
Easily Integrate with third-party technology providers which require dedicated IP Addresses
Integrating an organization’s gateway with third-party technology solutions can require that data forwarded from the gateway originate from unique organization-owned IP Addresses. This is easily accomplished with on-prem Secure Web Gateway appliances because the data leaving the network is created by connections leaving the organization’s physical perimeter. Moving to a cloud gateway platform can make preserving the unique IP Address needed to tie the gateway to third-party solutions challenging.
The iboss Cloud Platform eliminates this challenge by providing unique and dedicated IP Addresses in the cloud so that organizations can leverage them for connecting to external third-party systems. This includes sending Platform log data to third-party SIEMs and logging databases with a dedicated non-changing source IP Addresses for added security.
Regardless of user location, a user will always appear to be part of an organization while using organization owned devices including in the office, on the road or at home.
Restrict business app portal logins to iboss Cloud Platform IP Addresses for added mobile user security
Many business applications allow you to restrict user login by source IP. Typically, the source IP Addresses from the office is used to ensure users can only login to these portals when located within the office. With business applications moving to the cloud and users becoming increasingly mobile, the ability to restrict login based on source IP Address may seem impossible due to users needing access to those applications from outside the office.
With iboss Cloud Platform, users are always protected in the cloud and the source IP Addresses the Internet sees are the dedicated IP Addresses assigned to the organization within the Platform. This allows administrators to use those Source IP Addresses to restrict login to app portals based on the iboss cloud dedicated IP Addresses. This ensures the same level of protection even when users are outside of the office.

Take the next step in shifting to the world’s largest security platform built for the future.
Sign up for a demo to see how the iboss Zero Trust SASE prevents breaches by making applications, data and services inaccessible to attackers while allowing trusted users to securely and directly connect to protected resources from anywhere.




