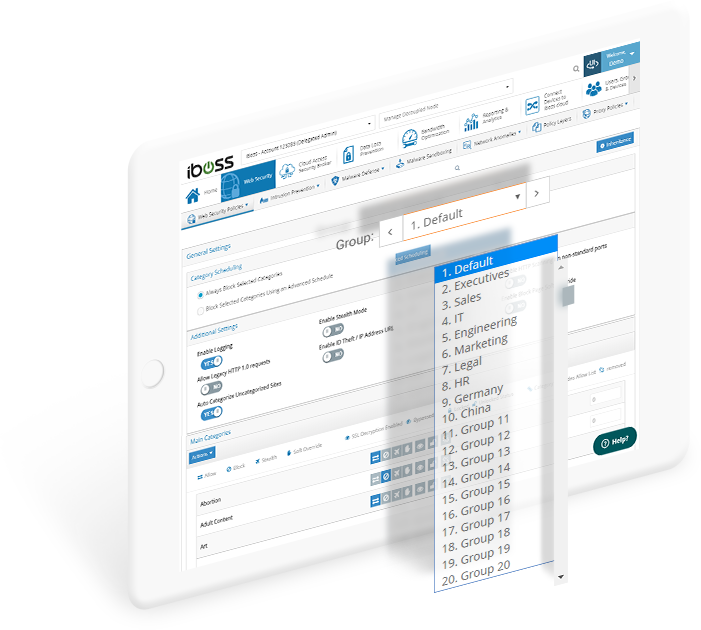
User and group based policies provide the flexibility to create differentiated role-based Internet access allowing users to be productive and secure
The iboss Zero Trust Secure Access Service Edge provides users role-based access to the critical applications and data needed to be productive while maintaining security and compliance. Criteria-based access provides users access to resources based on group membership within a directory, such as Azure AD or Okta. Administrators can easily map users to apps and data based on their roles within an organization to simplify the process of creating and managing resource access policies.
Supports Azure AD, Okta, Ping and other SAML Providers
The iboss Zero Trust Secure Access Service Edge automatically maps users to resources based on their group membership, or OU, within Active Directory, Azure AD, Okta, Ping and other Identity Providers. The platform can also map users and groups to any Identity Provider that supports SAML. By integrating with standard authentication protocols, such as SAML, administrators can ensure that any Identity Provider can be leveraged and used to provide role-based access to authenticated users.
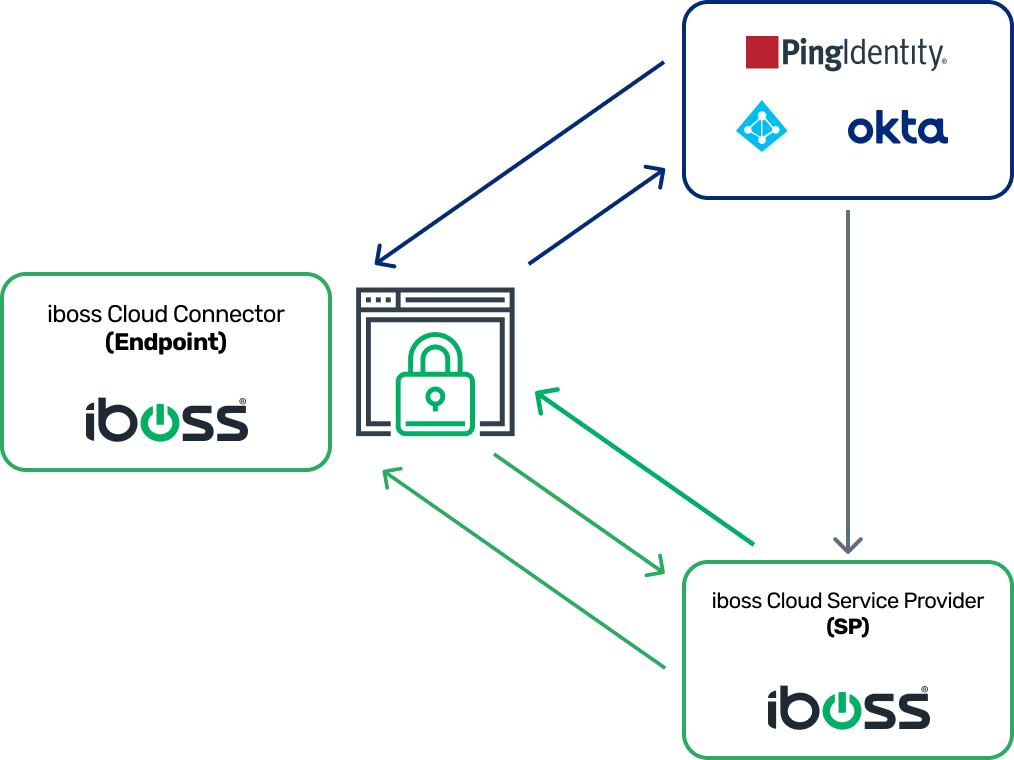
Use SAML to Assign Users and Groups to Specific Policies
SAML can be used to link policies to specific users or groups, as it eliminates the need to open firewalls to allow access to Active Directory server instances. The iboss Zero Trust Secure Access Service Edge will automatically extract the information it needs from SAML to assign group policies to users wherever they roam.
Speed Bump and Soft Block Overrides Allow Users to Override Restrictions
When users are restricted access to online content, administrators can allow users to perform self-service block page overrides. Users can use the speed bump feature to easily gain access to content – or administrators can require the user to enter credentials to gain access to restricted content. With these capabilities, IT support calls are reduced as users are warned about restricted content without being overly prohibited.





