Blog
Putting Trust in Zero Trust
Read Morepopular topics:
network security cloud security SASE zero-trust Cloud Adoption Ransomware cloud connector backhaul agent plan Redirect YouTube Google Classroom MDM CASB support policy cybersecurity guidelines NATO REvil Kayesa executive order cyber hygiene objects primitives rules conditions reporting risk dashboard cloud connected inventory count Restricted Mode Allow List override block pages country block file uploads G Suite iOS iPad Safari Chromebook ChromeOS keyword filter Android Always-on VPN Lockdown mode Cloud Access Security Broker block Dropbox block OneDrive block box.com block Google Drive Reports logs event viewer timeframe callout scheduling reports dashboard secure Internet SD-WAN IPSec GRE dedicated IP Microsoft Azure Secured Virtual Hubs Microsoft Virtual Hubs VirtualHubs Internet Security Azure Secured Virtual Hubs SSO migration partners channel RSAC FTP Relay product updates private access cyberattacks EA Sports Data Breach Colonial Pipeline JBS Healthcare HIMSS Microsoft 365 Microsoft partnership reverse proxy API CASB Remote Browser Isolation RBI Cybersecurity Awareness Month cybersecurity awareness Be Cyber Smart FedRAMP ATARC Cybersecurity civil cyber fraud vulnerabilities DLP Data Loss Prevention Cloud App Isolation Exact Data Match Defenders Network Behavior crisis management NIST Apache Log4j Log4Shell Threat Landscape Cyber Threats hackers
March 6, 2024
Navigating Ivanti Vulnerabilities: A Proactive Approach for Enterprise Security
The recent advisories and alerts issued by the Cybersecurity and Infrastructure Security Agency (CISA) concerning vulnerabilities in...

February 29, 2024
Empowering Educators in the Digital Classroom: The iboss Classroom Management Solution
In today's rapidly evolving educational landscape, the integration of technology into classrooms has become an essential part...

January 10, 2024
Optimizing Compliance and Security: iboss Integrates with CISA’s Protective DNS for Enhanced Government Defense
In the ever-evolving cybersecurity landscape, where threats multiply and diversify daily, government agencies find themselves in a...
September 29, 2023
Enhancing Digital User Experience in the Age of Cloud Applications: A Look at iboss Digital Experience Management
In today's era of rapid digital transformation, business-critical applications are increasingly cloud-based. While the shift to the...
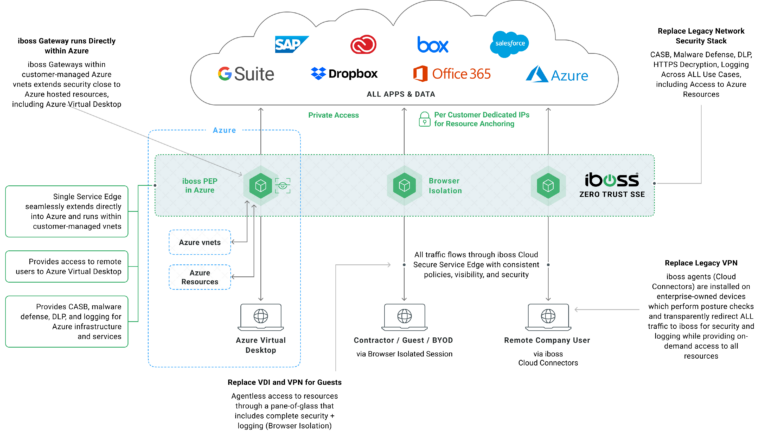
September 19, 2023
Solving Modern Azure Migration Challenges: iboss’ Azure Cloud Security Gateways
Organizations are migrating their infrastructure to the cloud in the fast-paced digital landscape. As enterprises make this...

September 8, 2023
Empowering K12 Education: iboss’s Unwavering Commitment to Safeguarding Schools Against Modern Cyber Threats
After having the privilege of serving as a CIO in K12 public education for many years, I...



