Large enterprises may require authenticating users that belong to independent domains.
This can be challenging as most platforms can only integrate with a single Federated Identity Provider.
The iboss Zero Trust Secure Access Service Edge is able to integrate with as many independent Identity Providers as needed while authenticating users against the correct identity provider that matches the requested resource.
Integrate with multiple independent Identity Providers concurrently
The iboss Zero Trust Secure Access Service Edge can integrate with an unlimited number of SSO Identity Providers concurrently. Groups of applications and services can be assigned to the iboss policies that map those resources to a specific Identity Provider for authentication. If a attempt to access a protected resource is made that requires a specific SSO Identity Provider, the iboss will automatically redirect the user to the appropriate Identity Provider for authentication before granting access.
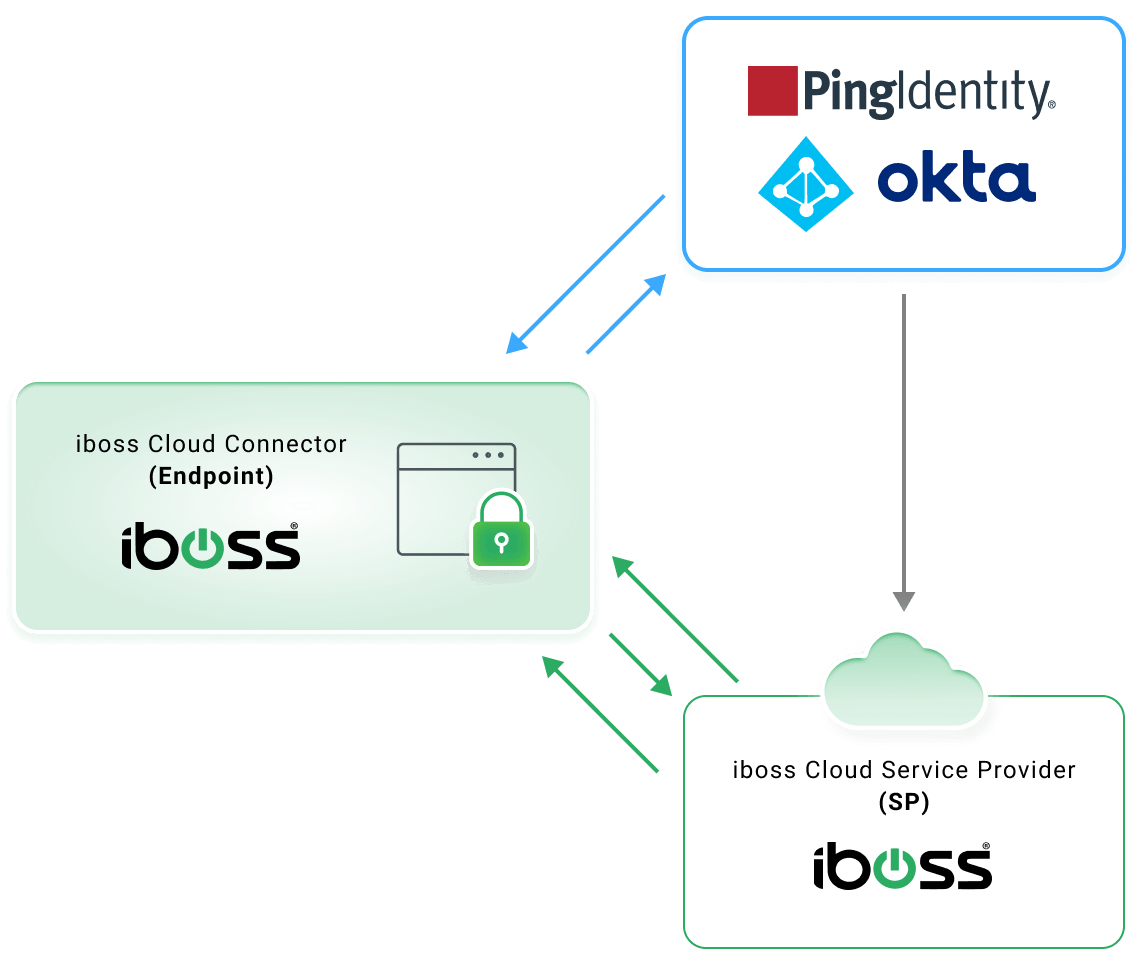
The iboss Zero Trust Secure Access Service Edge can integrate with an unlimited number of SSO Identity Providers concurrently. Groups of applications and services can be assigned to the iboss policies that map those resources to a specific Identity Provider for authentication. If a attempt to access a protected resource is made that requires a specific SSO Identity Provider, the iboss will automatically redirect the user to the appropriate Identity Provider for authentication before granting access.
Access logs associate the Identity Provider used for resource access
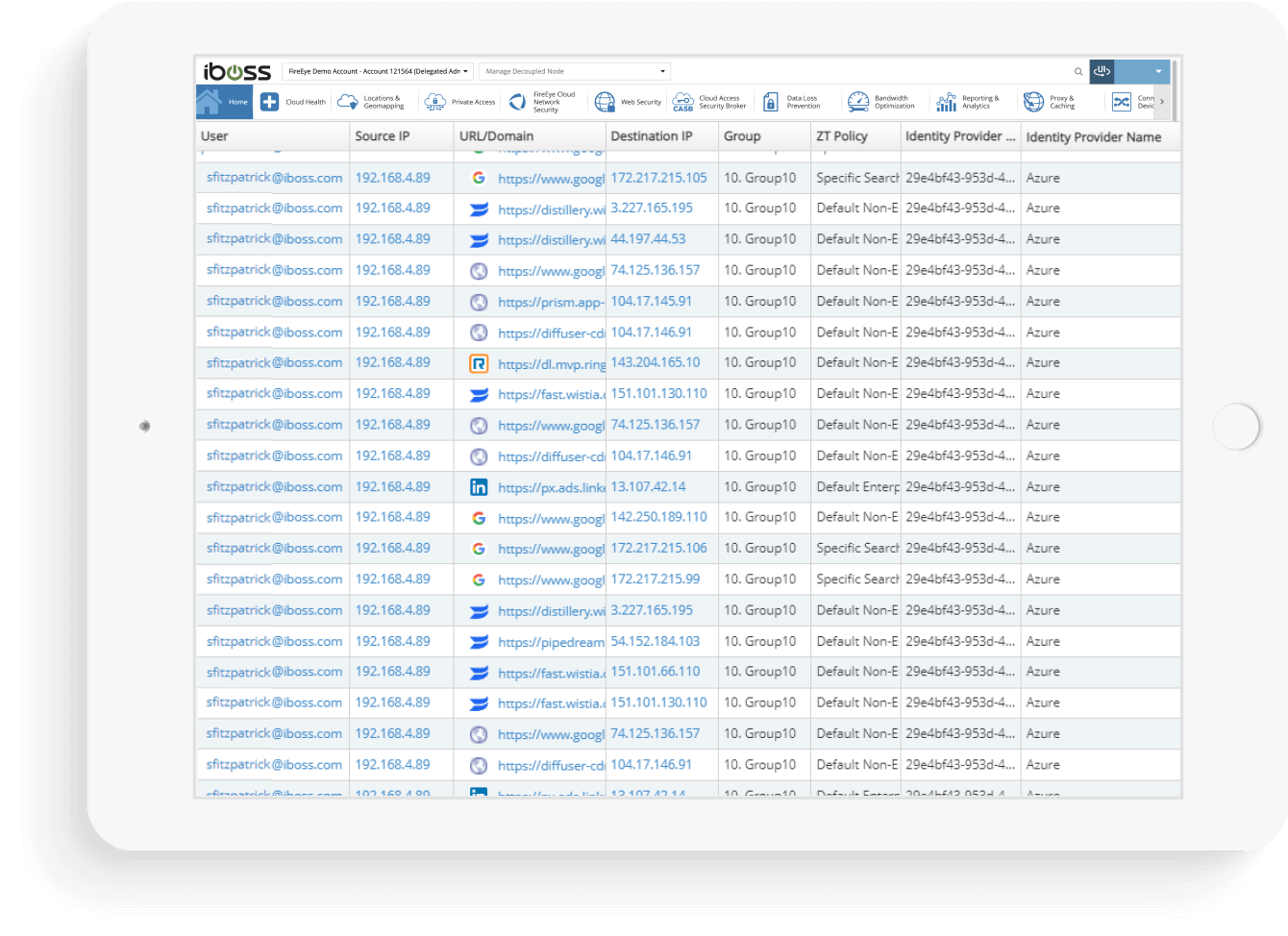
As users interact with protected resources that leverage different Identity Providers, security operations teams want to know how a user authenticated and against what Identity Provider the user authenticated to. The iboss Zero Trust Secure Access Service Edge adds the Identity Provider used to authenticate the user to every log event so that the username logged can be correlated to the correct Identity Provider. This is especially useful when multiple Identity Providers are used as usernames may overlap between the different domains containing user directories for different organizations.
Adaptive access capabilities can force step up authentication when access location is risky
The iboss Zero Trust Secure Access Service Edge allows policies to be linked based on identity and other context such as location. If a user is authenticating from a high risk location, policies can be created to force a higher level confidence authentication, such as MFA. The user is automatically redirected for authentication with the MFA requirement before gaining access to the resource from the high risk location.





