Adaptive Access Policies Provide Conditional Access
Adaptive access is capable of cutting access to critical resources when conditional access requirements are not met. Typically, applying conditional access requirements are only possible at the time a user authenticates with their Identity Provider. However, the iboss Zero Trust Secure Access Service Edge can provide continuous adaptive access decisions even after login occurs. Reason being, the iboss Zero Trust Secure Access Service Edge sits between the user and the resource and makes per-request access decisions which consult the conditional access policies every time a transaction to sensitive apps and data occurs. This greatly reduces risk by immediately cutting access to sensitive data and applications as soon as a device is determined to be infected with malware or ransomware.
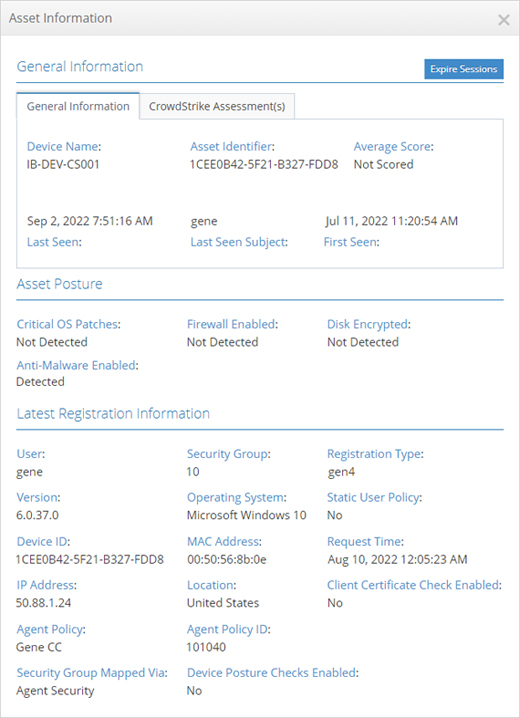
Built-in Device Posture Checks ensure assets meet compliance and health requirements before interacting with sensitive resources
Adaptive access policies are intelligent and continuous, as they apply to each request between a user and a resource to ensure that risk is greatly reduced whenever a noncompliant or risky situation occurs. It also allows devices to be cut off from resources immediately when they become noncompliant versus waiting for their current session to expire – which is typically the case when conditional access is only applied at the time of login.
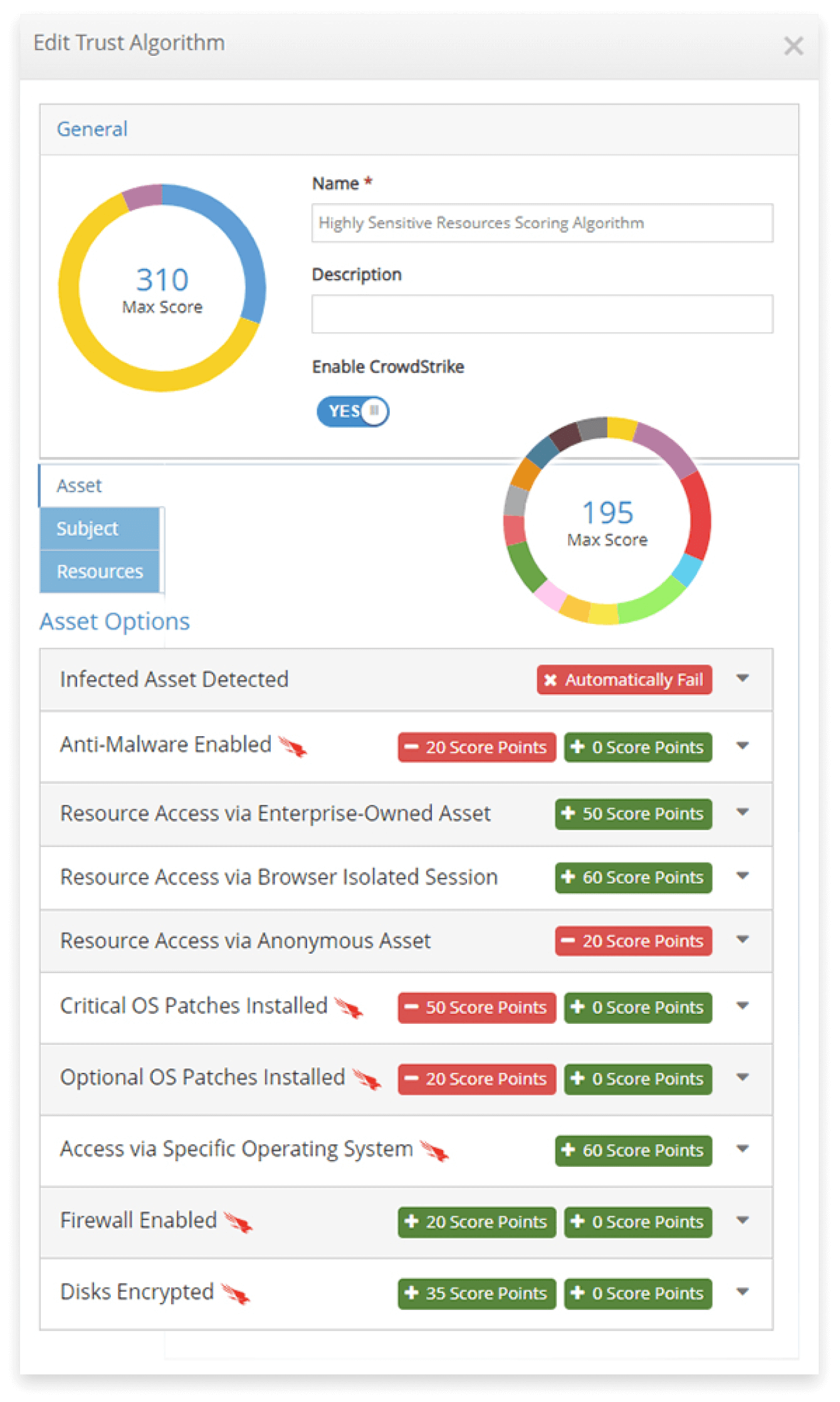
The iboss Zero Trust Secure Access Service Edge includes an extensive set of device posture checks that ensure an asset is healthy and compliant before interacting with sensitive data and applications.
Some of the asset posture checks include:
- Ensuring anti-malware is enabled
- Ensuring firewall is enabled
- Installing critical OS patches
- Ensuring the disk is encrypted
- Installing optional OS patches
- Allowing access only to specific operating systems
- Checking for installed client certificates
- Checking for specific files on the system
- Checking for specific registry keys on the system
The adaptive access Trust Algorithm allows actions to be taken should any of the checks fail. For example, some common actions that can be taken when a device posture check is not met include:
- Automatically failing, which will cut access to the sensitive resource
- Isolating the session to provide separation between the user and the resource using Browser Isolation, a modern VDI replacement that is more secure and intelligent as it provides the separation that legacy VDI provides. It also includes in-app security controls and logging visibility for all interactions within the isolated session.
The adaptive access Trust Algorithm allows actions to be taken should any of the checks fail. For example, some common actions that can be taken when a device posture check is not met include:
- Automatically failing, which will cut access to the sensitive resource
- Isolating the session to provide separation between the user and the resource using Browser Isolation, a modern VDI replacement that is more secure and intelligent as it provides the separation that legacy VDI provides. It also includes in-app security controls and logging visibility for all interactions within the isolated session.
Adaptive access policies are intelligent and continuous, as they apply to each request between a user and a resource to ensure that risk is greatly reduced whenever a noncompliant or risky situation occurs. It also allows devices to be cut off from resources immediately when they become noncompliant versus waiting for their current session to expire – which is typically the case when conditional access is only applied at the time of login.
Authentication session hijacking is prevented with user conditional access checks
Once a user is authenticated to an application, a login session is created to allow the user to interact with the resource. The session allows the user to present a token to the application to prove that they have successfully authenticated and provided credentials prior during the login process. However, if that session token is hijacked by an attacker, they can present the token to the application which will grant access under the assumption that the attacker has previously properly authenticated.
This is a common technique used by attackers and is one of the top three initial infection vectors for ransomware according to the Cybersecurity and Infrastructure Security Agency, CISA
This is why it is critical to follow the NIST 800-207 Zero Trust Architecture principle of applying “per-request” access decisions instead of only providing authorization once, at the time of login. With the iboss Zero Trust Secure Access Service Edge, each request is authenticated and authorized including those that occur after login. This protects from authentication hijacking as an attacker that has hijacked the session and presents the authentication token at distances that indicate impossible user travel would be rejected automatically. The iboss platform compares the location of where the login occurred to the location of where access is occurring and, if the distance is too great, will automatically reject the request to the protected resource. This extends conditional access far beyond just the point of login, making it continuous to ensure data and applications remain safe from attackers.
Access to sensitive apps and data is automatically cut when a device becomes infected
With the iboss Zero Trust Secure Access Service Edge, adaptive access trust algorithms are continuously evaluating, authenticating and authorizing every transaction between a device and a protected enterprise-owned resource. The device can only access sensitive resources through the iboss Zero Trust Secure Access Service Edge, which acts as a checkpoint to the protected application. The trust algorithm used for adaptive access includes a signal that indicates whether the device is infected and automatically cuts access when an infection is detected. The iboss platform cuts access immediately and automatically, with no human intervention, to prevent infections from spreading and causing massive harm. The iboss Zero Trust Secure Access Service Edge automatically flags devices as infected by inspecting communication to malware Command and Control (CnC) Centers which indicate a device is breached. Once a breach is detected, access to data and applications is automatically terminated via the adaptive access trust algorithms.
As soon as a device becomes infected with malware or ransomware, the damage to other systems, applications and data can spread like wildfire. The infected device becomes a vehicle for infecting other devices that can result in catastrophic losses and downtime. It is critical to isolate a device as soon as it is breached and ensure all sensitive resources are completely inaccessible by the compromised asset. Typically, the time it takes to identify an infected device and take action can be impeded by human processes and workflows needed to identify the compromised device and restrict access to sensitive data and applications.
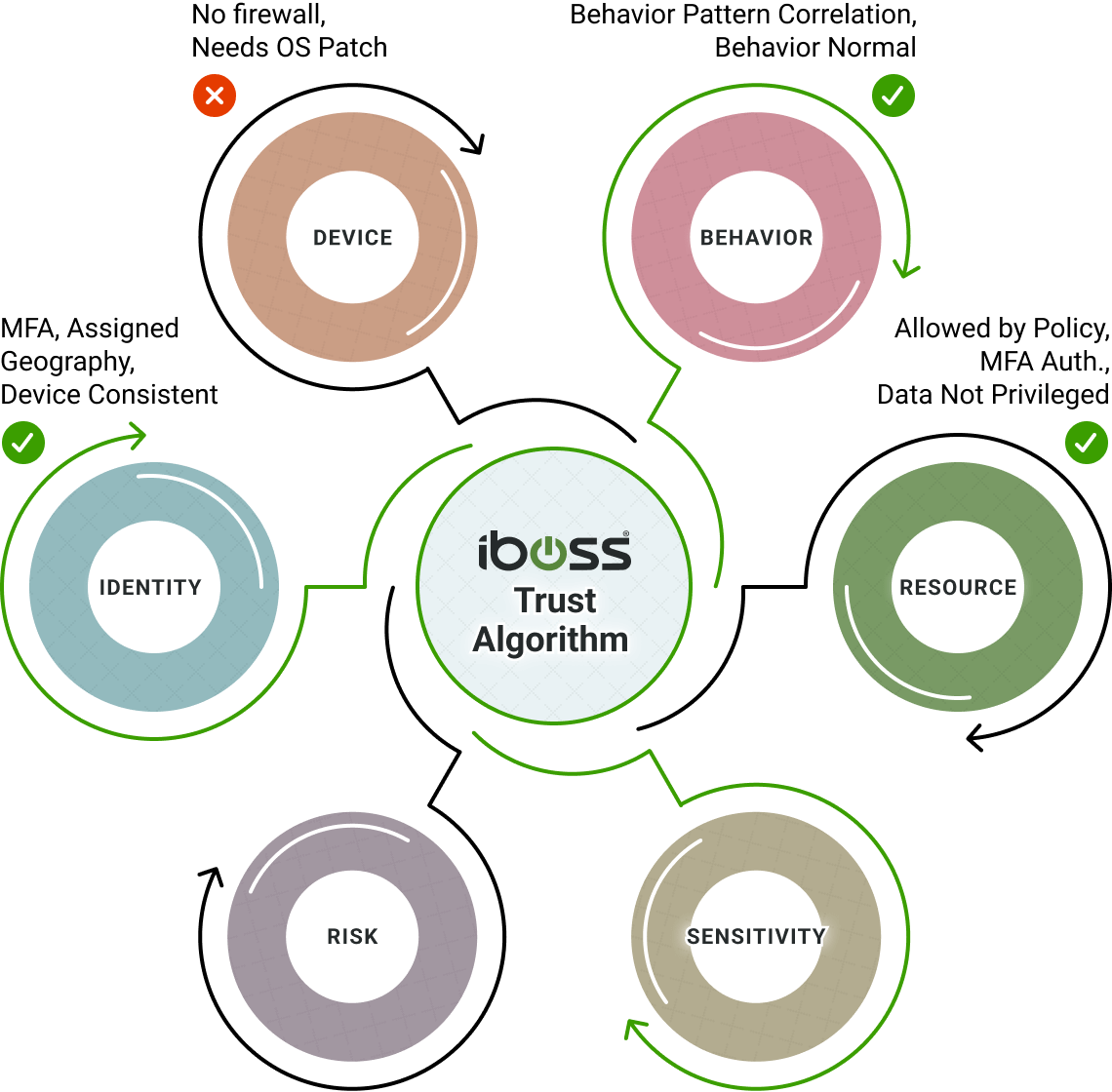
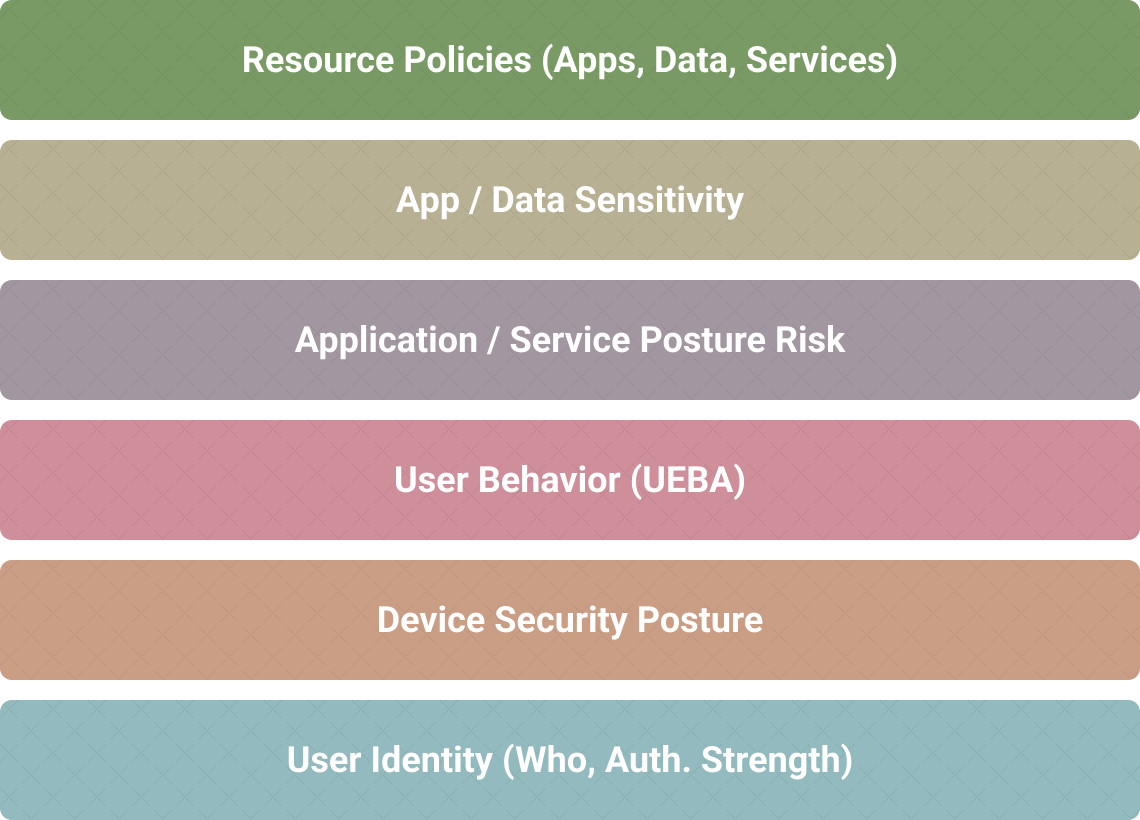
Adaptive Access Based On Trust Algorithms
as defined by
NIST 800-207 Zero Trust Architecture
Adaptive Access Based On Trust Algorithms
as defined by
NIST 800-207 Zero Trust Architecture
The NIST SP 800-207 Zero Trust Architecture defines a framework for adaptive access trust algorithms which includes receiving a series of signals from various sources, running them through a trust algorithm within the Zero Trust service, and making a final decision of whether to authorize access or deny access to a protected resource. This is an important design concept as the signals that are analyzed include user signals, such as how the user is authenticated, device signals, such as whether the device is infected, and others that are available at the time access is needed to a resource. The trust algorithm ingests all signal types in a unified method and uses them to make a final determination for access. The iboss Zero Trust Secure Access Service Edge follows this design pattern by combining the various signals and analyzing them via the configurable trust algorithm to take actions. Actions include denying access to a resource – for example, when a device is infected, isolating access to a resource, increasing the trust score or decreasing the trust score for the transaction.
The NIST SP 800-207 Zero Trust Architecture defines a framework for adaptive access trust algorithms which includes receiving a series of signals from various sources, running them through a trust algorithm within the Zero Trust service, and making a final decision of whether to authorize access or deny access to a protected resource. This is an important design concept as the signals that are analyzed include user signals, such as how the user is authenticated, device signals, such as whether the device is infected, and others that are available at the time access is needed to a resource. The trust algorithm ingests all signal types in a unified method and uses them to make a final determination for access. The iboss Zero Trust Secure Access Service Edge follows this design pattern by combining the various signals and analyzing them via the configurable trust algorithm to take actions. Actions include denying access to a resource – for example, when a device is infected, isolating access to a resource, increasing the trust score or decreasing the trust score for the transaction.
This is unlike competitors such as Zscaler which lack a unified signal trust algorithm and instead treat signals such as “asset posture checks” as independent criteria. To make matters worse, with Zscaler, there are multiple admin interfaces to manage settings not only for ZIA and ZPA, but also a separate console for managing asset posture checks. With the iboss Zero Trust Secure Access Service Edge there is a single, global unified policy engine which includes the trust algorithms for adaptive access that can be applied to all users, devices and resources regardless of where they are located.
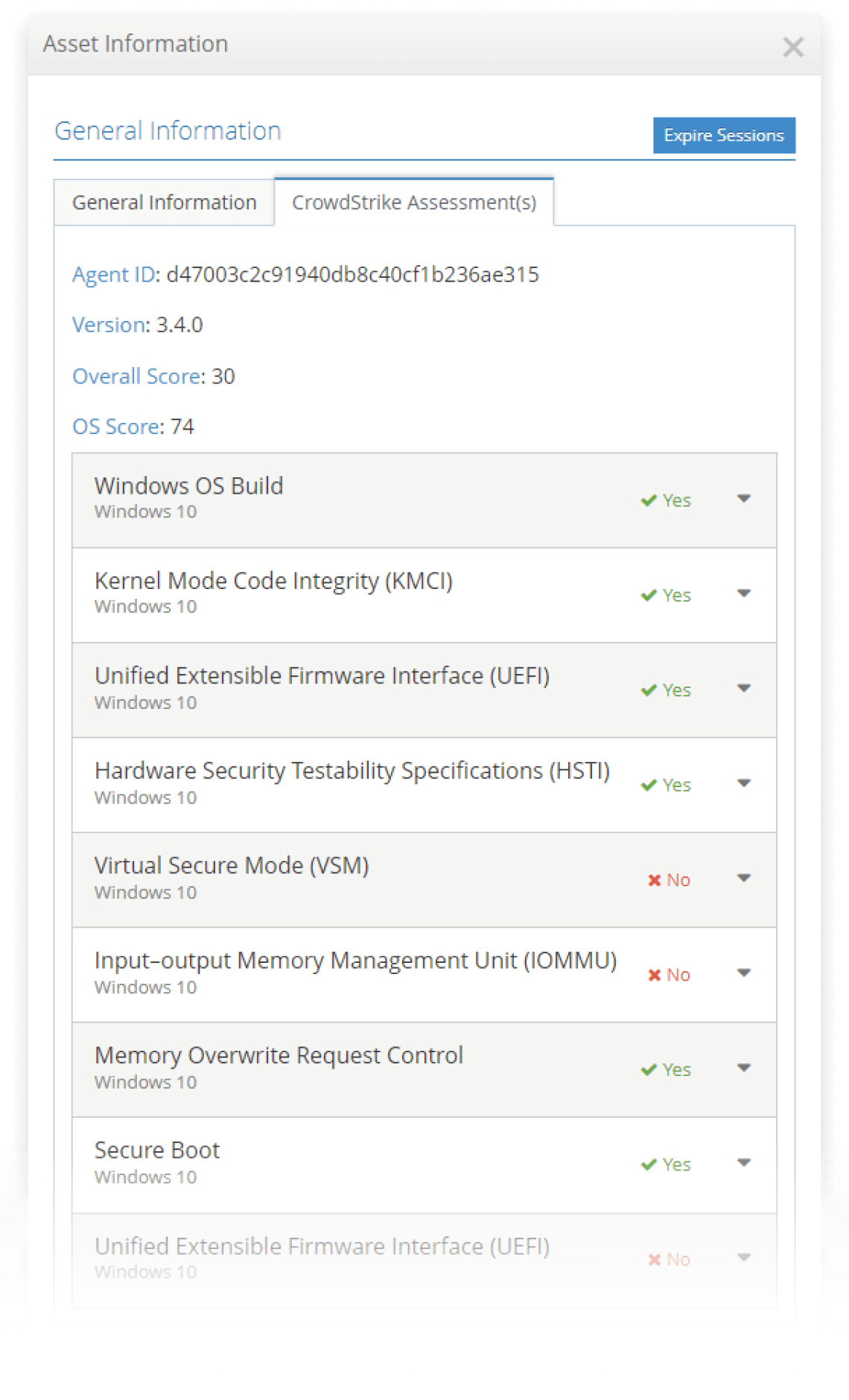
Integration with CrowdStrike turns XDR insights into real-time access decisions
Integration with CrowdStrike turns XDR insights into real-time access decisions
With the adaptive access trust algorithms available in the iboss Zero Trust Secure Access Service Edge, signals coming from external sources can feed into the algorithm, which takes automatic action including cutting access to resources from infected devices. The iboss Zero Trust Secure Access Service Edge is natively integrated with CrowdStrike and can take the large number of signals from the CrowdStrike endpoint agent, including its determination if a device is infected or compromised, and feed them into the iboss adaptive access trust algorithm for automatic and immediate action. For example, if CrowdStrike signals that a device is infected or compromised, iboss can automatically terminate access to sensitive resources. The iboss Zero Trust Secure Access Service Edge is capable of ingesting a large number of signals from CrowdStrike for additional device posture checks and leveraging them within the iboss trust algorithm. The iboss Zero Trust Secure Access Service Edge provides a platform to unify normally disparate cybersecurity technology into a cohesive cybersecurity approach.