Risk & Threat Reports
Detailed logs provide reports for high risk users and infected devices
The iboss Zero Trust Secure Access Service Edge has detailed threat reports that clearly show infected devices, prevented malware and other sources of risk. The dashboards are drillable and provide the needed insight to security teams so that faster response times can be achieved for potential breaches. The iboss platform also creates incidents for infected devices and situations resulting in possible data loss so that workflows can be used for remediation.
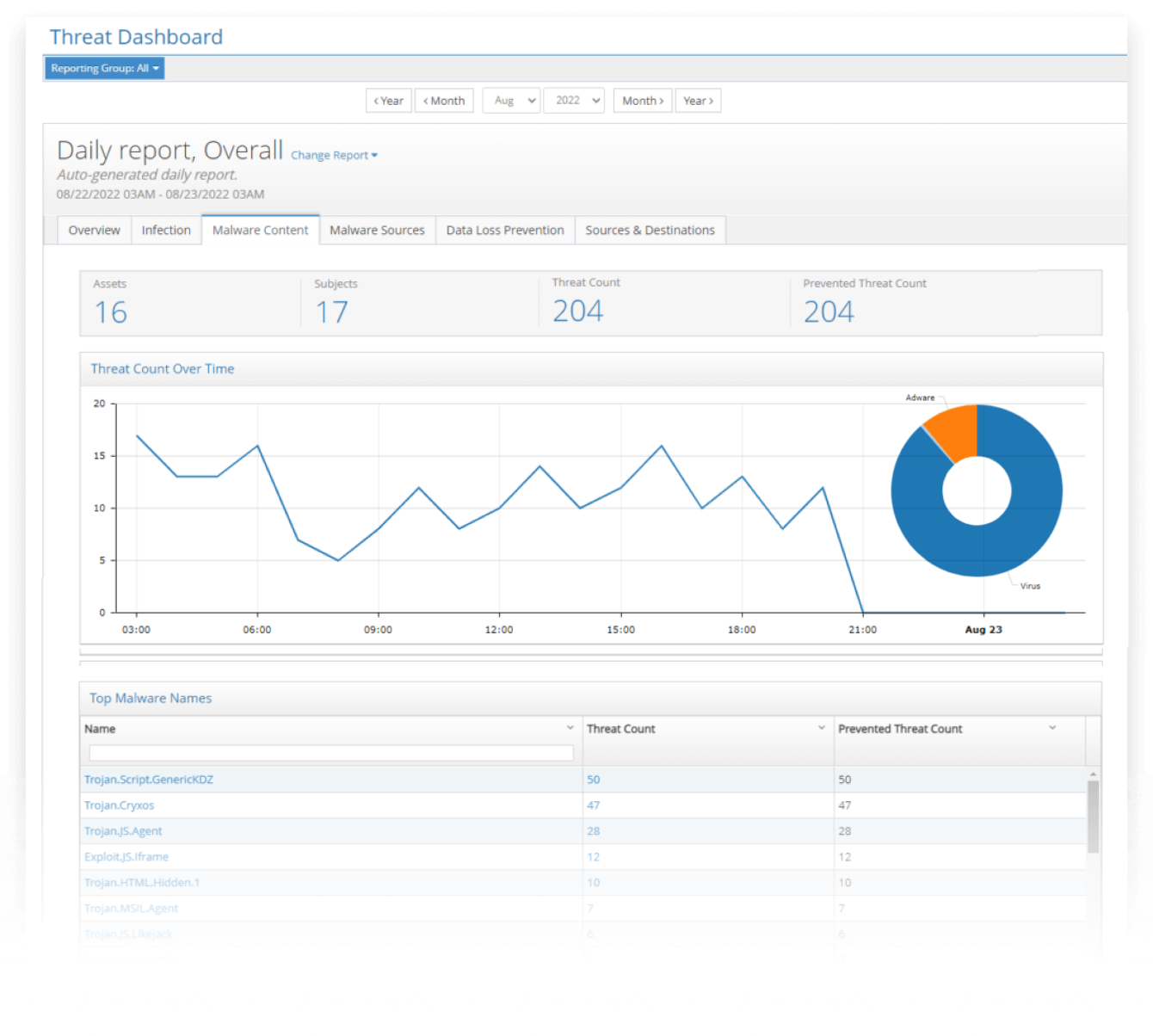
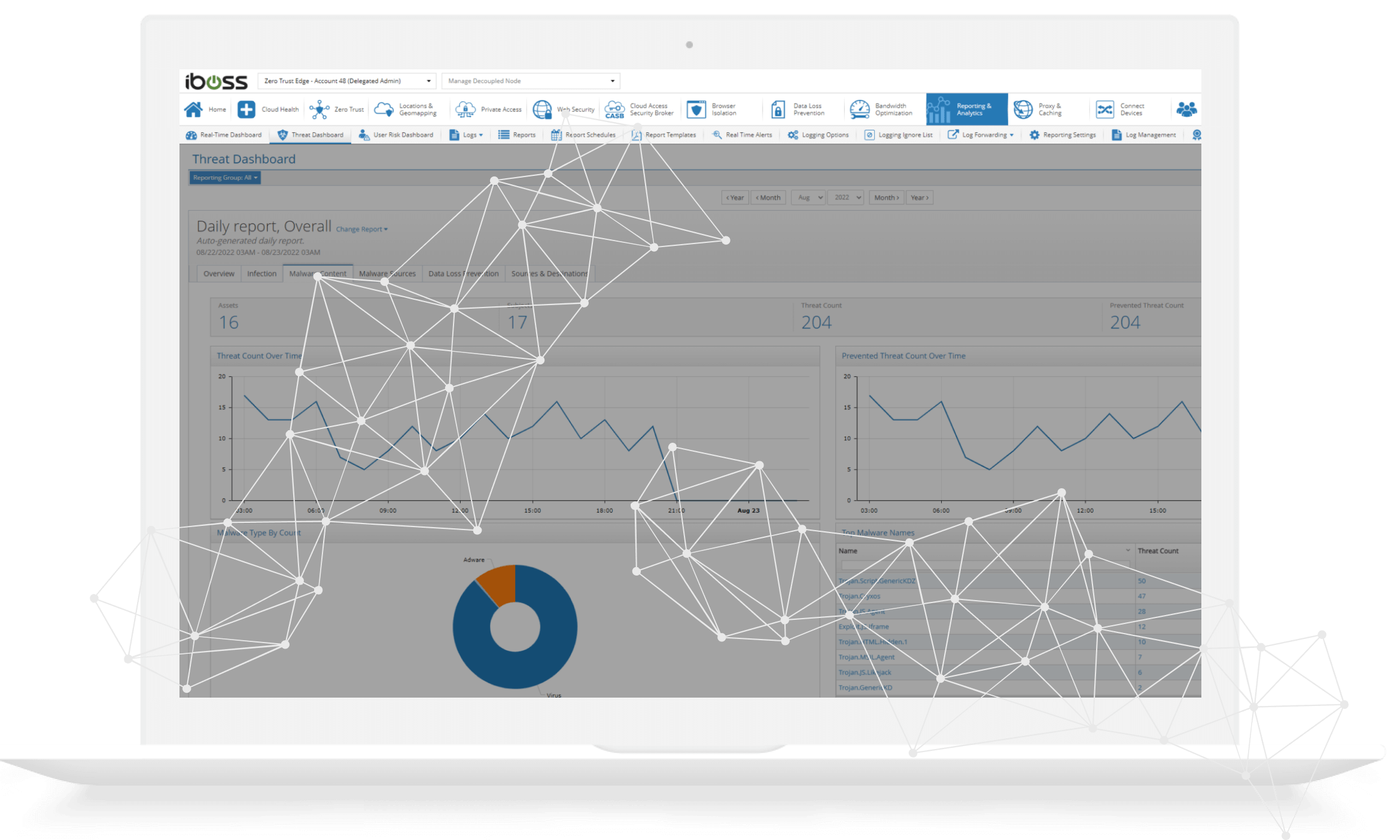
Threat dashboards include threat counts by source and threats detected within content
The iboss Zero Trust Secure Access Service Edge automatically analyzes logs and distills them to detailed threat dashboards that include information about malware content and sources. Malware incidents are broken down by type and include the malware names. Additionally, the assets and users that interacted with the malware are displayed to determine high risk users and devices within the organization. The dashboards are interactive allowing administrators to click on a malware entry, for example, and display all of the users and assets associated with that incident.
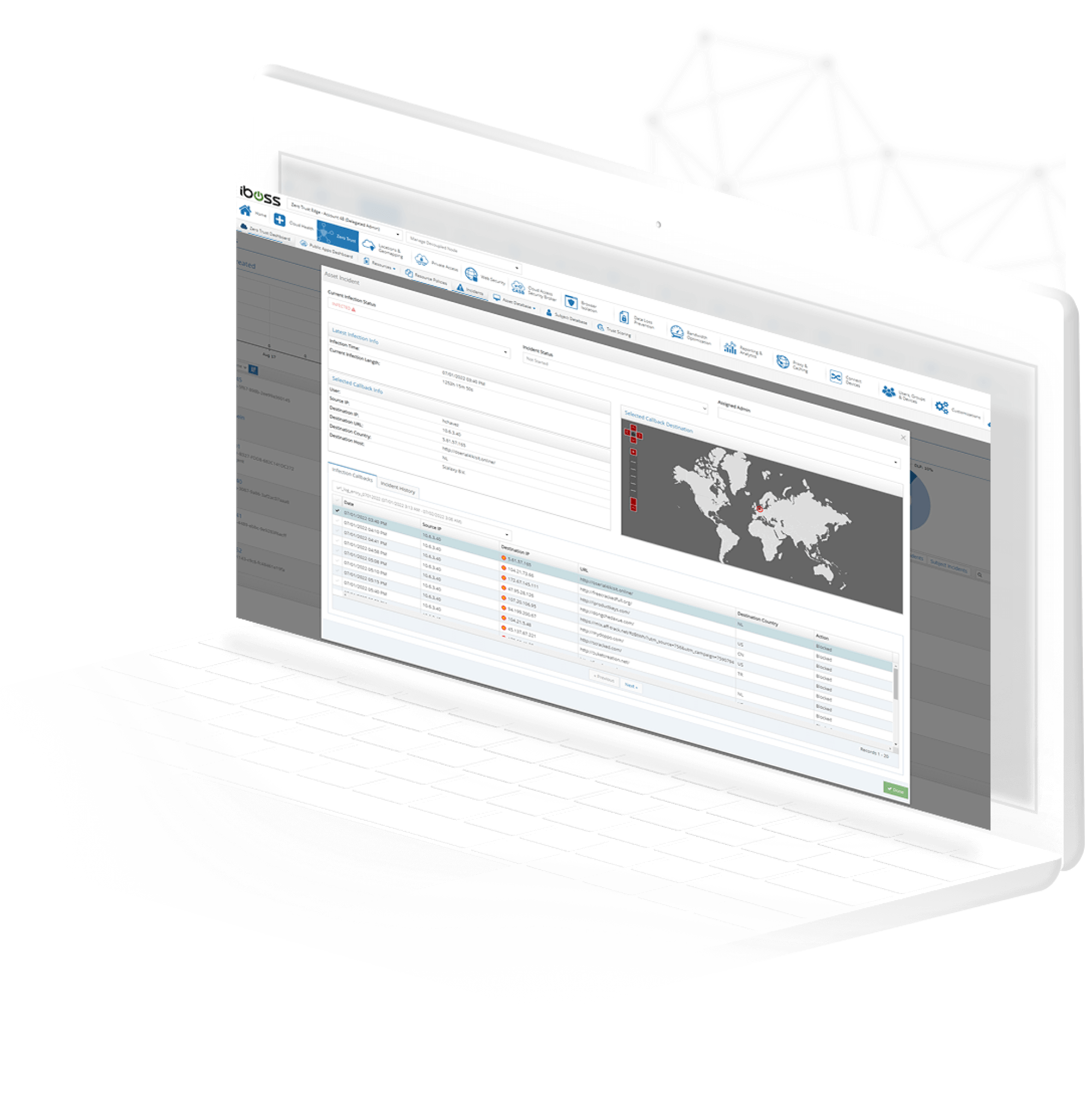
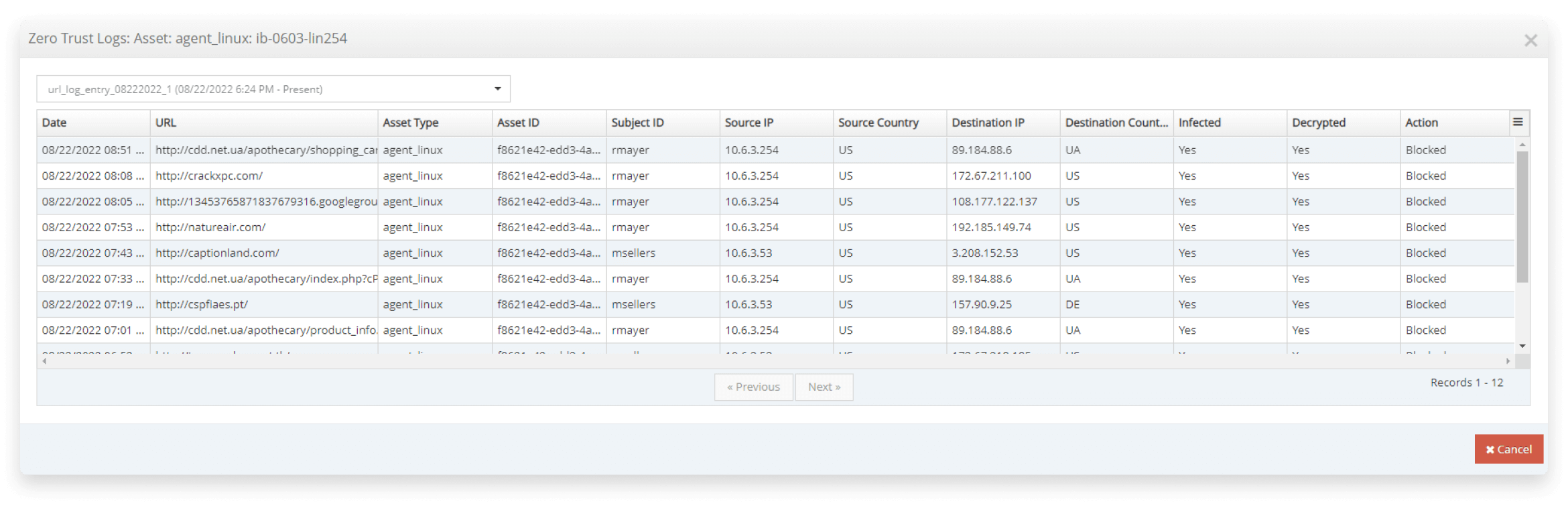
Infected asset dashboards include detailed infection callback URLs
The infection dashboards clearly show infected devices and users that have been involved with incidents leading to the infection. When drilling into the details of an infected asset, a list of Command and Control Center (CnC) callbacks are clearly displayed to understand what the lead to the asset being flagged as infected. This helps security teams determine what assets are compromised and remediate quickly to minimize impact to the organization.
Incident dashboards tracks incidents related to infections and data loss
The incidents dashboard tracks active incidents related to malware breaches and data loss. Detailed information about the incident is clearly displayed, including the history of accesses leading up to the breach and prior incidents for the asset. When investigating the incident, deep information is provided for the risky access such as associated malicious URLs. This helps incident responders determine the scope of the breach and the impact to the organization.