Ensuring devices and assets are healthy and configured optimally to avoid breach is critical for reducing risk and ensuring compliance. Checking to make sure the firewall is enabled, the disk is encrypted and antimalware is running are just a few of the device posture checks that are critical to maintain compliance and avoid unnecessary breaches. The iboss Zero Trust Secure Access Service Edge includes extensive device posture checks and automatically monitors and reports on the state of assets continuously while cutting access to protected resources when required criteria is not met.
Automatically checks device posture including firewall, disk encryption and antimalware state
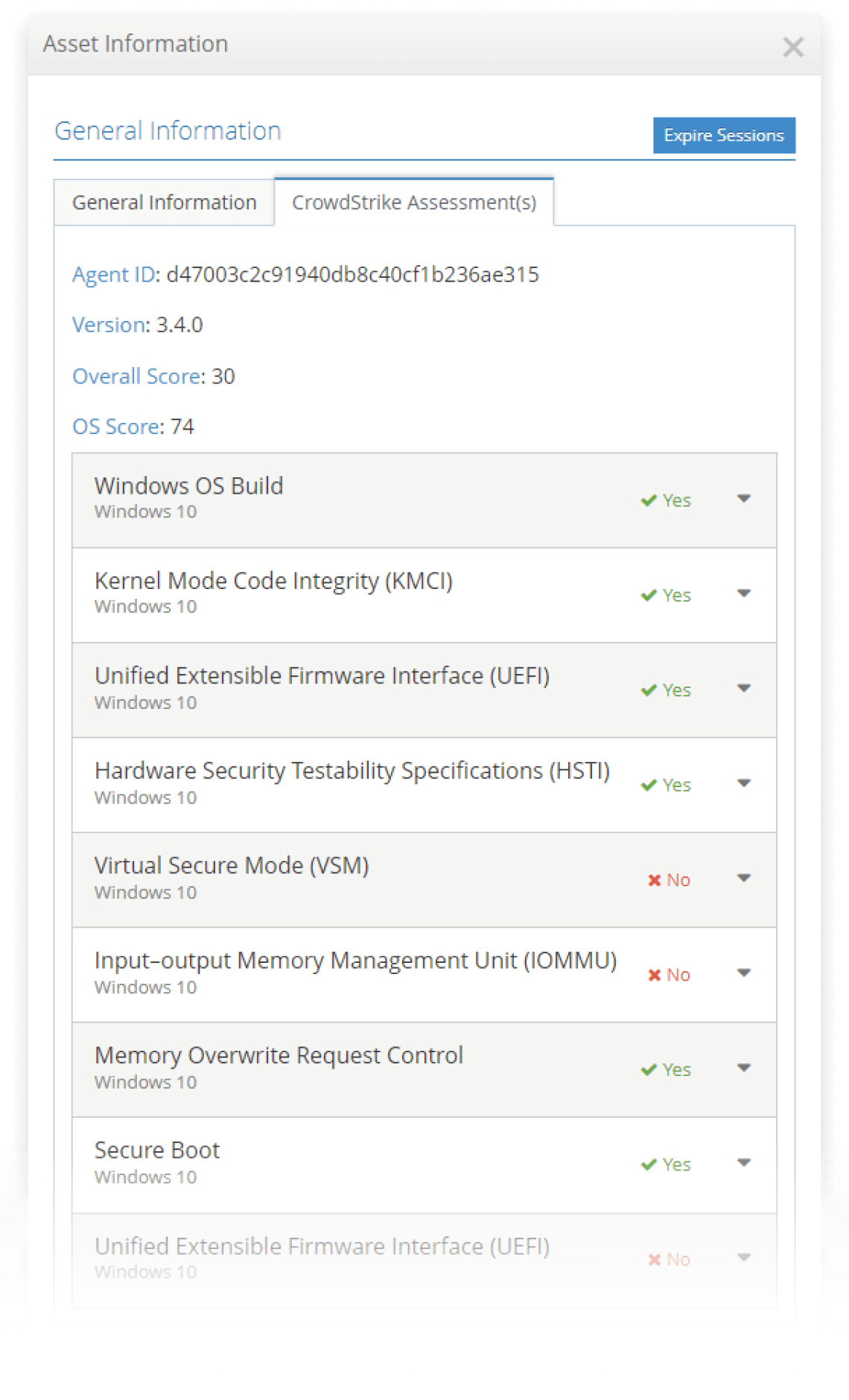
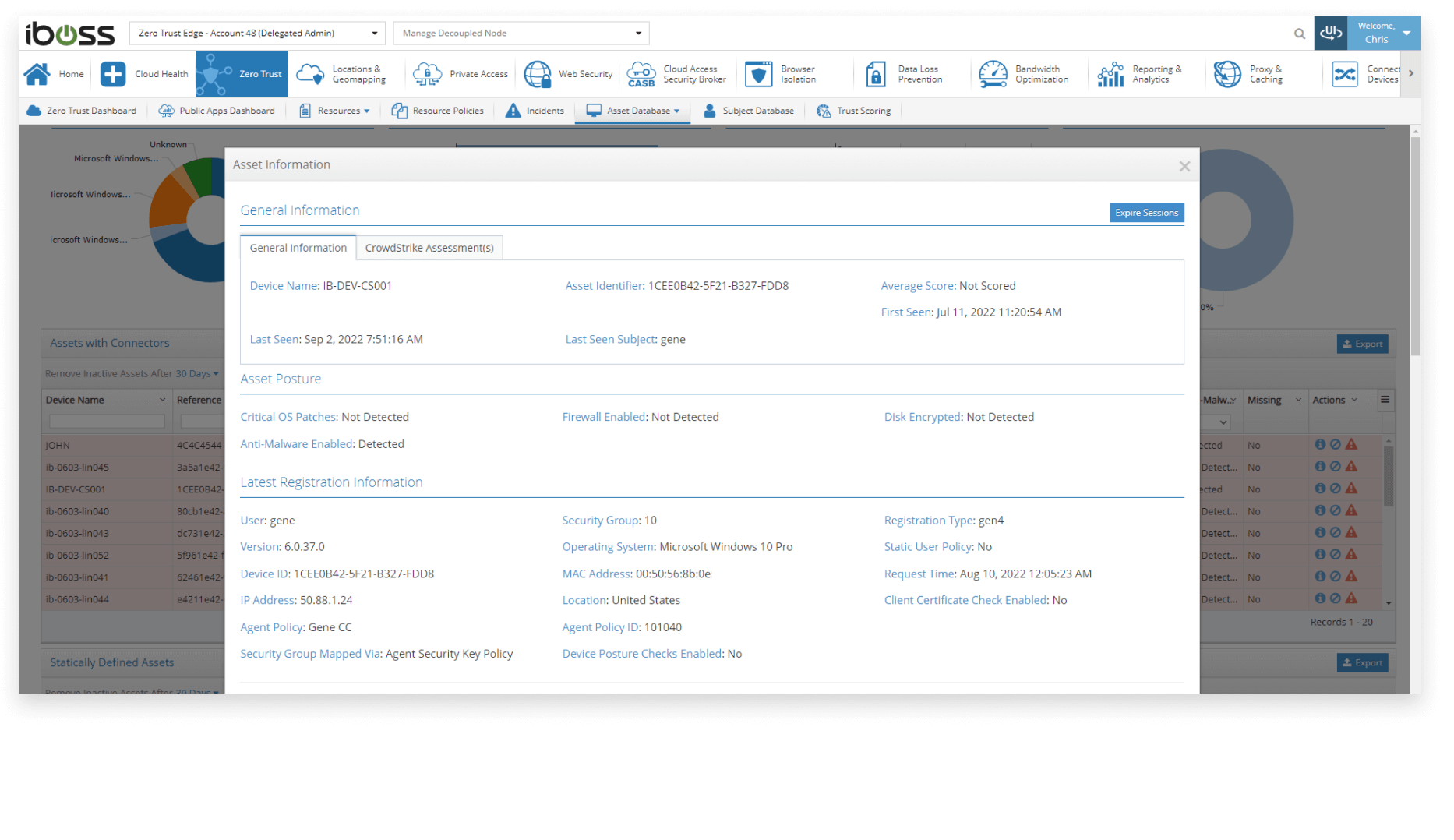
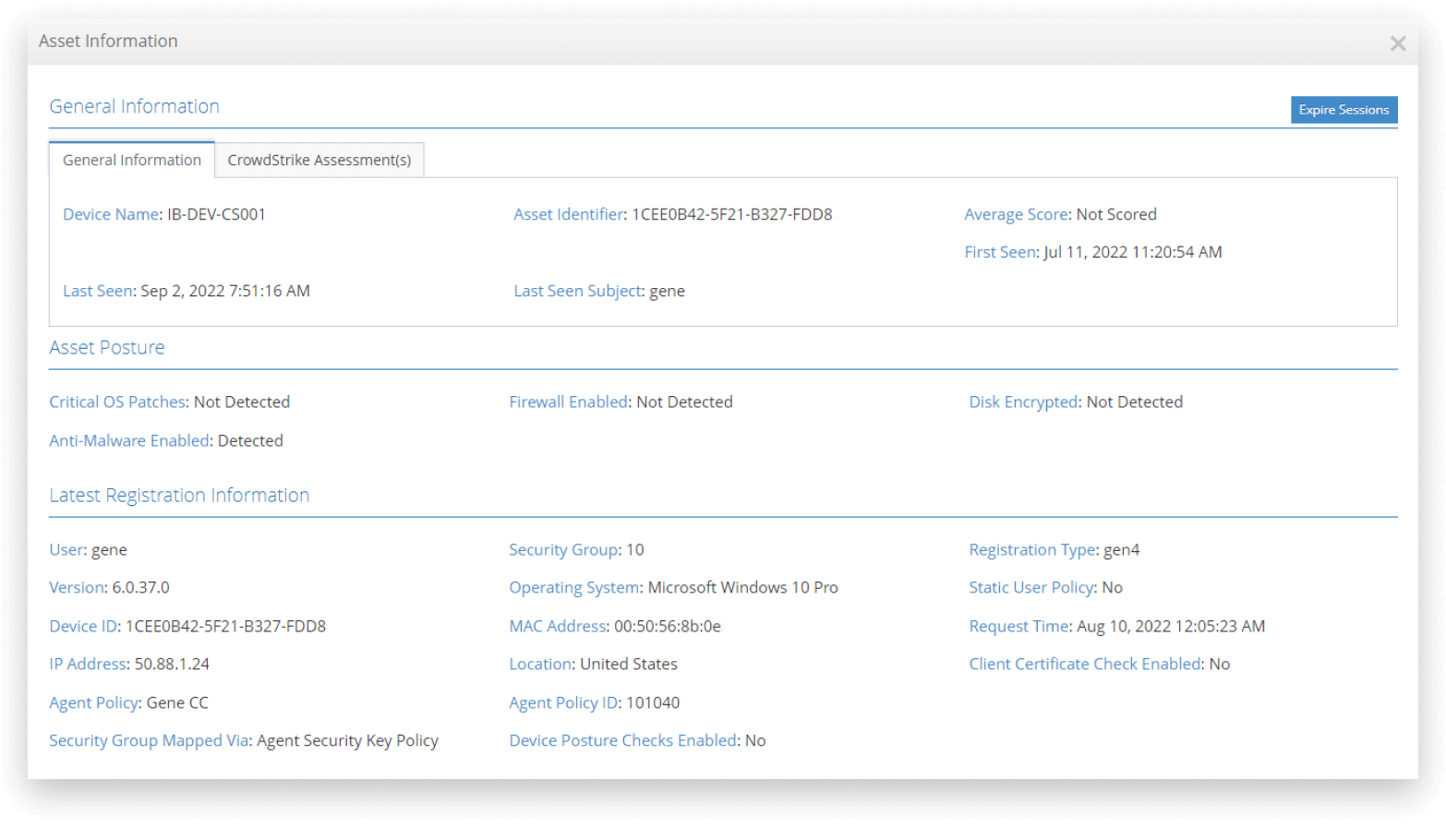
The iboss Zero Trust Secure Access Service Edge automatically performs device posture checks via the installed cloud connectors on enterprise-owned devices. The device posture checks are reported up to the iboss cloud security service which both logs the current state of the device posture and uses the device posture checks for adaptive access decisions. If device posture checks fail, access to resources can be terminated or isolated. Checks are automatic and continuous and changes to access based on these checks require no human interaction.

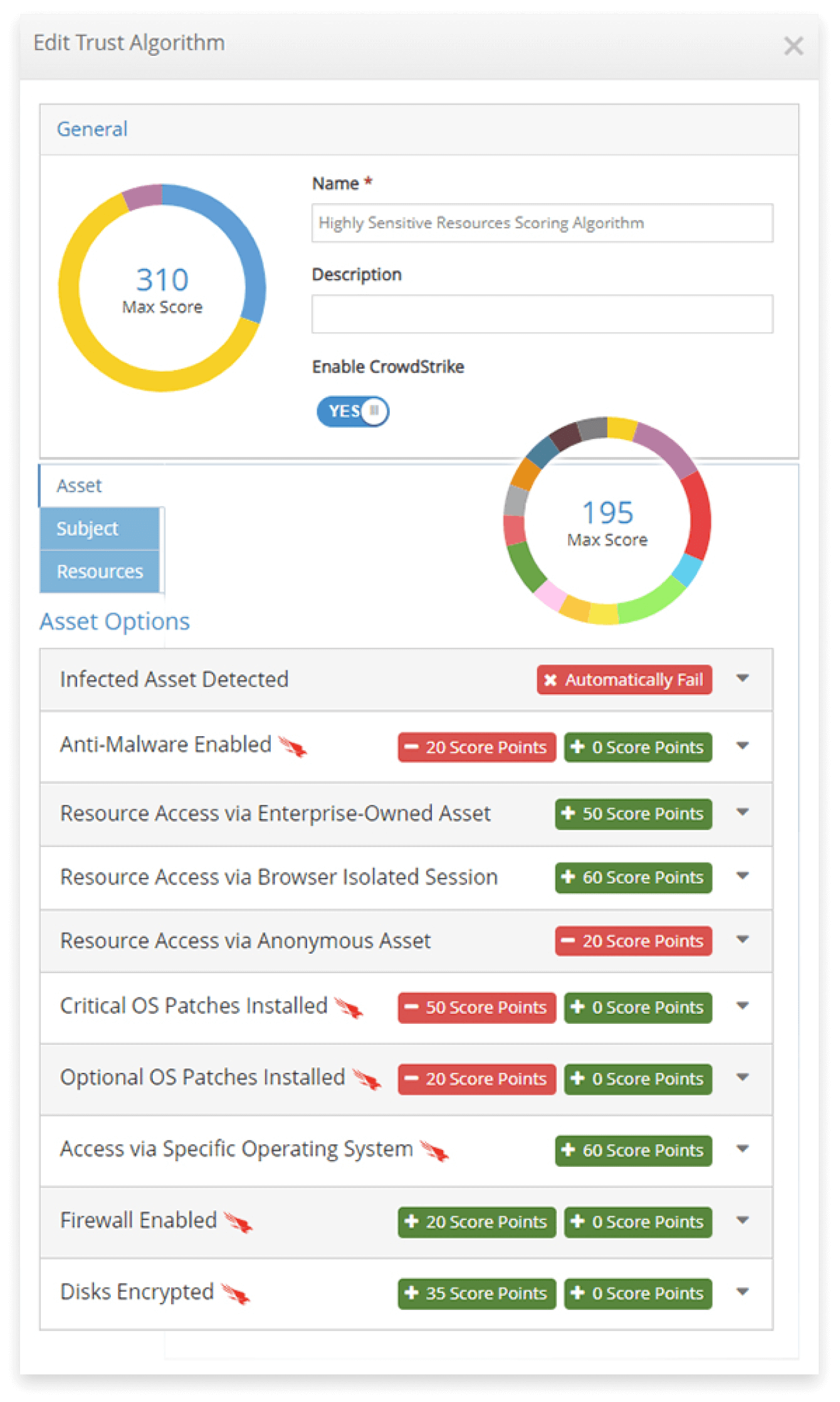
Built-in Device Posture Checks ensure assets meet compliance and health requirements before interacting with sensitive resources
The iboss Zero Trust Secure Access Service Edge includes an extensive set of device posture checks that ensure an asset is healthy and compliant before interacting with sensitive data and applications. Some of the asset posture checks include:
- Ensure anti-malware is enabled
- Ensure firewall is enabled
- Critical OS patches are installed
- Ensuring the disk is encrypted
- Optional OS patches are installed
- Access is allowed only to specific Operating Systems
- Checking for installed client certificates
- Checking for specific files on the system
- Checking for specific registry keys on the system
The adaptive access Trust Algorithm allows actions to be taken should any of the checks fail. For example, some common actions that can be taken when a device posture check is not met include:
Automatically failing which will cut access to the sensitive resource.
Isolating the session to provide separation between the user and the resource using Browser Isolation.
Browser Isolation is a modern VDI replacement that is more secure and intelligent as it provides the separation that legacy VDI provides but also includes in app security controls and logging visibility for all interactions within the isolated session.
The adaptive access Trust Algorithm allows actions to be taken should any of the checks fail. For example, some common actions that can be taken when a device posture check is not met include:
Automatically failing which will cut access to the sensitive resource.
Isolating the session to provide separation between the user and the resource using Browser Isolation.
Browser Isolation is a modern VDI replacement that is more secure and intelligent as it provides the separation that legacy VDI provides but also includes in app security controls and logging visibility for all interactions within the isolated session.
Adaptive access policies are intelligent and continuous so that they apply to each request between a user and a resource to ensure that risk is greatly reduced whenever a non-compliant or risky situation occurs. It also allows devices to be cut off from resources immediately when they become non-compliant versus waiting for their current session to expire which is typically the case when conditional access is only applied at the time of login.

Provides detailed status of device posture via a centralized asset catalog
The iboss Zero Trust Secure Access Service Edge provides a centralized asset catalog which includes the current state of critical device posture checks such as the state of the firewall, whether the disks are encrypted and antimalware is enabled. The device list can be exported or extracted via API. In addition, with the native Crowdstrike integration, the posture checks provided by Crowdstrike are also displayed for each asset.