Support GDPR Compliance
Moving to the cloud can introduce compliance risks with regulations like GDPR.
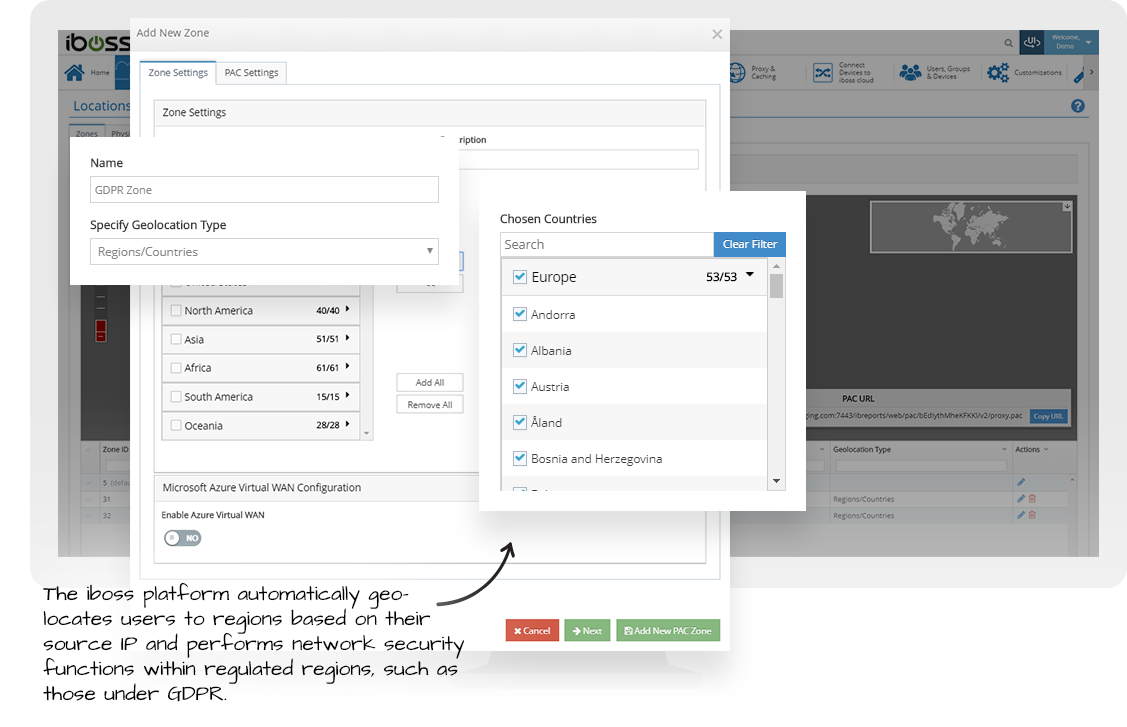
The iboss cloud allows admin created GDPR zones to ensure the cloud scans and stores data within regulated regions.
Regulations are mandating organizations implement data security measures to protect user privacy and meet data protection requirements. When moving to a cloud gateway platform, ensuring regional compliance is critical to avoid violating laws and receiving hefty fines. Cloud gateways scan user Internet data to help deliver protection from malware and prevent data loss. Since these gateways exist in the cloud and sensitive user data may traverse them, it is helpful for the gateways to remain within region in order to support regulatory constraints.
The iboss cloud allows administrators to create zones to ensure data is scanned within regulated regions when users enter those regions. In addition, the log event data that is generated by the cloud can be sent to reporting databases that reside within admin-controlled zones as well. This supports compliance with regulatory requirements while leveraging the elasticity and power of a cloud-based gateway platform.
Admin controlled zones ensure data is scanned within selected regulated regions
Cloud gateways are not only responsible for protecting user Internet access, but also generate the log events that represent cloud activity, malware and DLP alerts. The log events are critical to understanding user cloud activity and identifying infected devices and high risk users.
Data protection regulations, such as GDPR, contain certain restrictions regarding collection and storage of certain personal data, such as when user activity generates log events from within particular regions.
Solution Brief
Cloud Based Internet Security Designed for GDPR
Anonymize user log events generated by the cloud to support compliance with privacy regulations
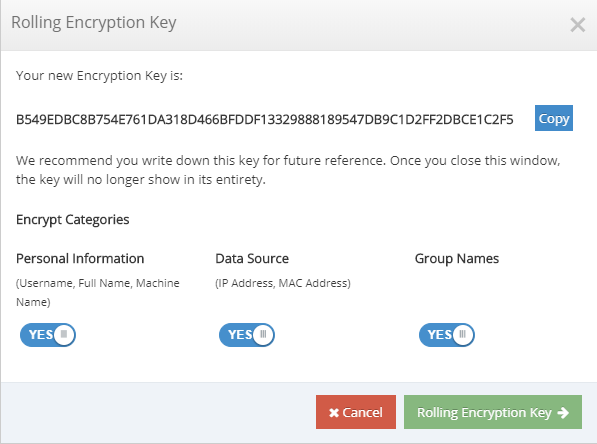
Anonymization of logs allows administrators to randomize user identity within logs. The anonymization can be configured so that different aspects of the log event are anonymized including username and group.

Containerized cloud architecture ensures data control and separation
The iboss cloud is built on the concept of containerized reporting nodes which are located within iboss cloud. The containerized reporting nodes are discrete and exist within specific regions and zones. An administrator can configure multiple containerized reporting nodes to service the organization so that log events generated by users in Europe, for example, stay within Europe while data generated from other regions are redirected to reporting nodes in those regions. This ensures data that is generated within a regulated region, remains within that region.




