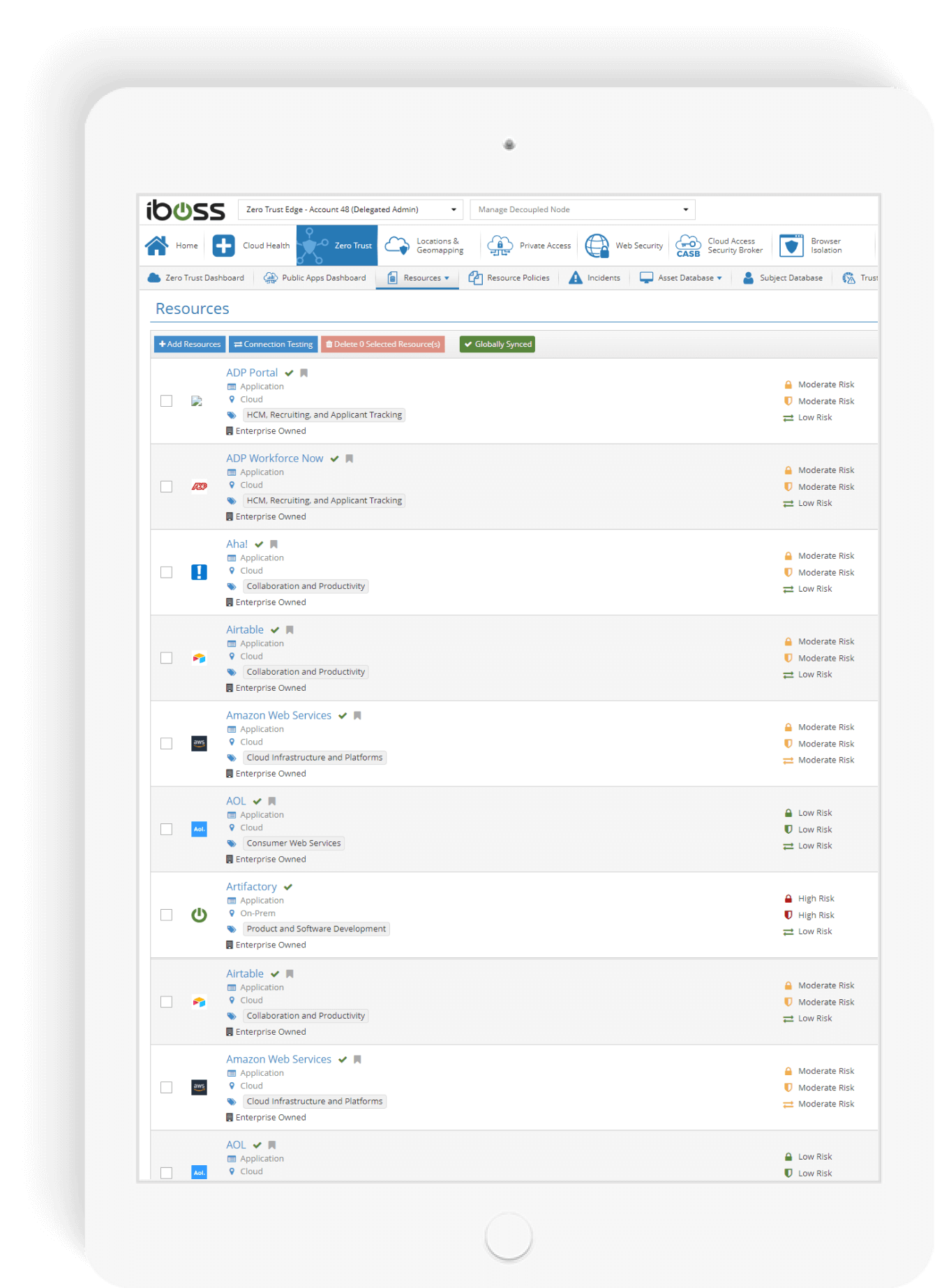
The iboss Zero Trust Secure Access Service Edge provides cataloging capabilities that can be used to inventory what sensitive resources need to be protected. The resource catalog organizes applications and services which can be labeled by type and security impact. Understanding what resources exist within the enterprise is critical for understanding risk and creating appropriate access policies.
Catalog applications and services by type and security impact level
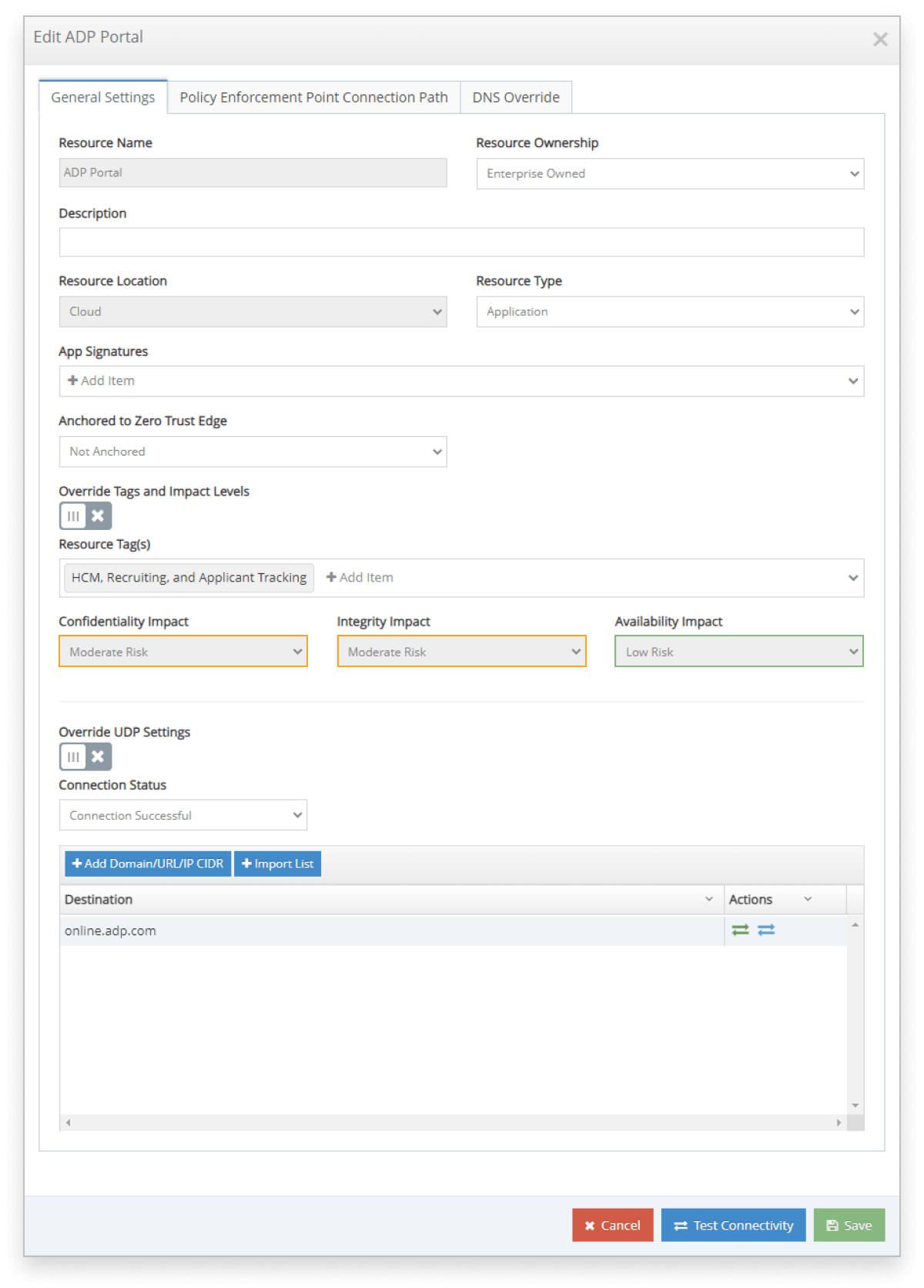
The iboss Zero Trust Secure Access Service Edge provides a resource catalog that allows applications and services to be organized by type, risk and location. Labels can indicate the type of resource and multiple labels can be added to each resource. There are many built-in labels and label categories but custom labels can be created as well. In addition, each application or service can be configured with security objectives and impact levels for data loss, data destruction or loss of access to the resource. The security impact levels are aligned directly with NIST FIPS 199 which define the three security objectives Confidentiality, Integrity and Availability as well as impact levels low, moderate and high.
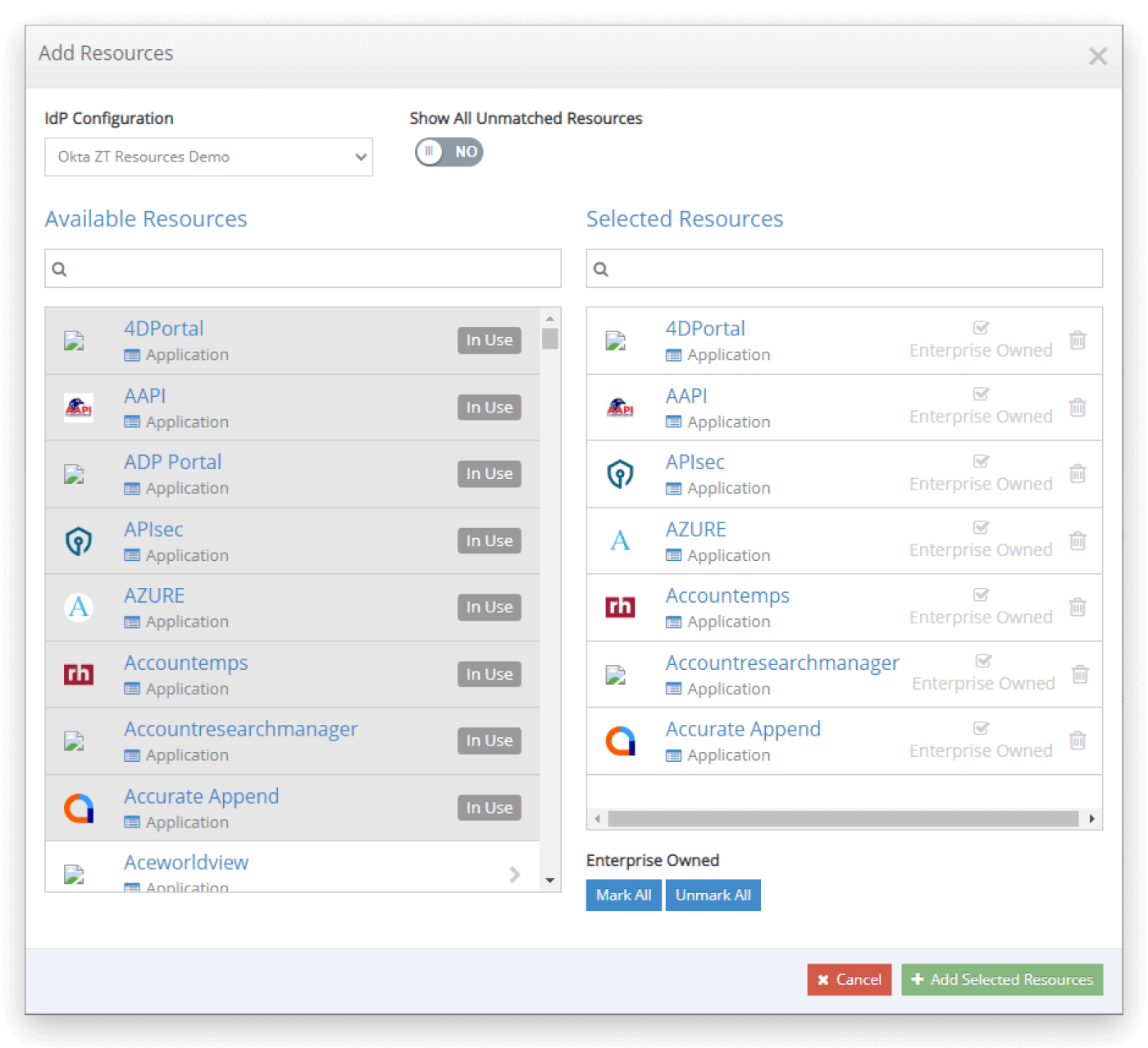
Synchronizes resources from Azure AD and Okta
If applications or services are already configured within Azure AD or Okta, the iboss Zero Trust Secure Access Service Edge can extract those applications and catalog them automatically. The iboss platform has thousands of pre-labeled applications including security risk levels. As applications are synchronized from Azure AD or Okta, they are automatically stored into the iboss resource catalog.
Employs Unified Resource Catalog for SaaS, cloud and on-prem resources
The iboss Zero Trust Secure Access Service Edge provides a global, unified service to protect resources and users, regardless of location. The location of the resource does not affect the security capabilities that can be applied by the iboss platform as iboss treats all resources equally whether they are SaaS, in cloud providers or on-prem.
This is unlike Zscaler, which uses multiple admin consoles to manage resources differently, depending on location.
For example, Zscaler utilizes two service edges, ZIA and ZPA. Each service edge has different capabilities and disparate admin consoles which not only increases management complexity but limits the type of protection that can be applied depending on the service edge leveraged.
With iboss, all resources are unified under a single service edge for consistent security and visibility, regardless of resource location while simplifying security administration with a single pane of glass admin console.