Blog for
General
popular topics:
network security cloud security SASE reporting GDPR compliance virtual desktop infrastructure (VDI) internet access speed Cloud Adoption zero-trust network perimeter Ransomware secure Internet Zero Trust Network Access packet capture on-prem web proxy appliances subscription Kayesa REvil executive order plan cyber hygiene Security Information and Event Management (SIEM) Microsoft Cloud App Security (MCAS) Switching to iboss cybersecurity awareness SD-WAN Cybersecurity Awareness Month RBI Remote Browser Isolation API CASB CASB cloud-based web security Microsoft partnership Microsoft 365 security layers migration to the cloud SIEM Data security Remote device security HIMSS Be Cyber Smart FedRAMP Rapid deployment ATARC Cybersecurity civil cyber fraud vulnerabilities DLP Data Loss Prevention Cloud App Isolation Exact Data Match Wessex Water NIST Apache Log4j Log4Shell Instant Search GeoZone 9.8.27 malware Knowledgebase Apple SSL cloud-hosted ISO standards Apple TLS throttle video UI GUI user interface UX Next Generation User Interface Faster page loads Knowledge base Autosuggestion admin console next-gen cloud admin console PAC script FireEye Cloud iboss platform version Block YouTube HD log tuning EA Sports Data Breach Tunneling WCCP Colonial Pipeline JBS Healthcare
January 10, 2024
Optimizing Compliance and Security: iboss Integrates with CISA’s Protective DNS for Enhanced Government Defense
In the ever-evolving cybersecurity landscape, where threats multiply and diversify daily, government agencies find themselves in a...
September 29, 2023
Enhancing Digital User Experience in the Age of Cloud Applications: A Look at iboss Digital Experience Management
In today's era of rapid digital transformation, business-critical applications are increasingly cloud-based. While the shift to the...
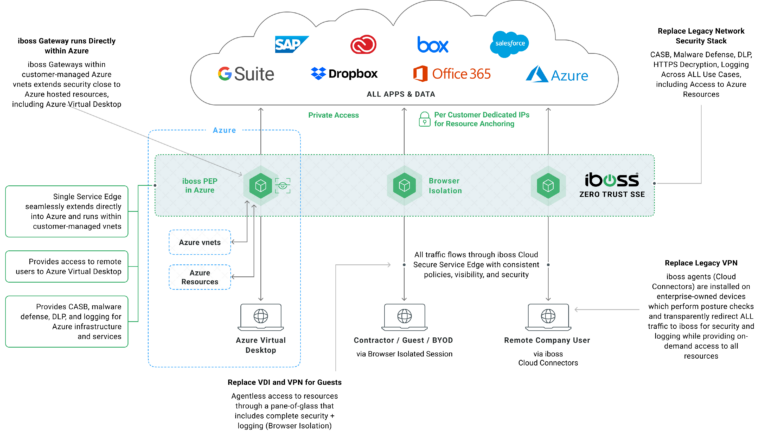
September 19, 2023
Solving Modern Azure Migration Challenges: iboss’ Azure Cloud Security Gateways
Organizations are migrating their infrastructure to the cloud in the fast-paced digital landscape. As enterprises make this...

February 27, 2023
CISA Urges Increased Vigilance One Year After Russia’s Invasion of Ukraine
In response to the CISA alert urging increased vigilance one year after Russia’s invasion of Ukraine, organizations...

January 23, 2023
Browser Isolation: The Zero Trust VDI Replacement
Accessing customer data is an essential part of the customer service experience. However, when Call Center agents...
June 23, 2022
Zero Trust: The glue that holds everything together
A holistic approach to Zero Trust can provide a multitude of benefits, including preventing malware from entering...



