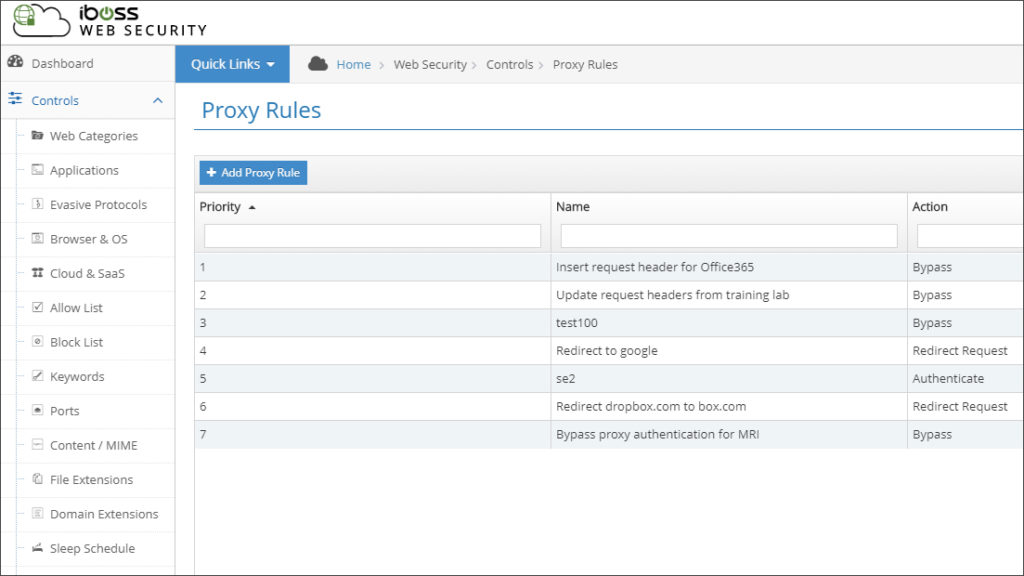
No two networks are exactly alike. This means that you must occasionally find workarounds for challenges and quirks that are unique to your environment.
Adaptive Access Control allows you to design your own custom rules. This enables you to tailor the iboss functionality to the unique needs of your environment.
Let’s look at a couple of scenarios.
Use domain redirection to automatically route users to approved services.
Imagine that your organization has discovered that many users are transferring files to their personal file hosting accounts, including Dropbox. To enforce compliance with the policies of your organization, you decide to add a rule that automatically redirects attempts to visit dropbox.com to <your-org>.box.com, the domain for the file hosting service that is used by your organization. You must also be able to easily update the rule to add additional domains as the need arises.
Adaptive Access Control enables you create rules that automatically redirect network users away from their personal services to the ones that are approved by your organization.
Create modular rules to accommodate single-purpose devices without comprising your overall security.
The Internet of Things (IoT) expands the need for visibility and control over your cloud connections. As devices rely more on cloud connectivity for software updates and data exchange, so does an organization’s need for reliable and secure internet access.
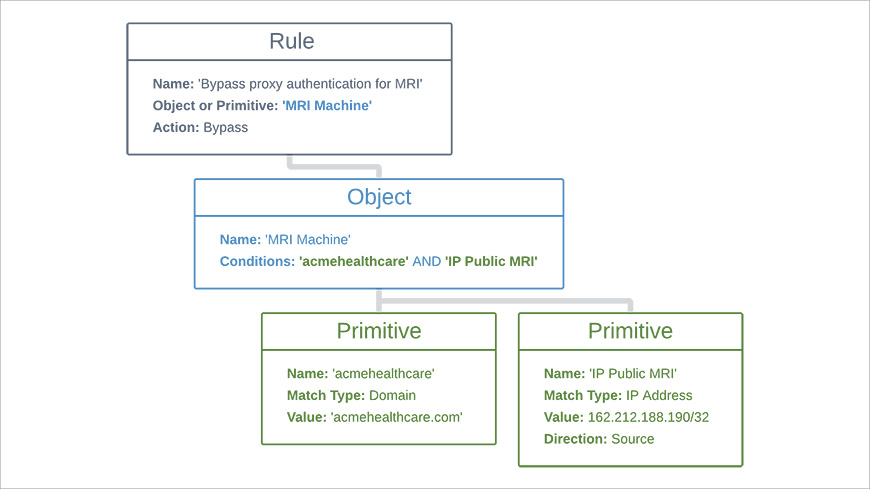
Consider the challenge of a hospital that recently installed a new MRI machine. The machine must regularly check for updates from an external server. All of the hospital’s devices connect to a proxy server to gain secure access to the Internet. Because the MRI machine has limited network functionality, it is unable to fulfill the authentication requests from the proxy server. Adaptive Access Control enables you to design granular rules to allow the MRI machine to bypass the proxy authentication without compromising the security of your other devices.
Manage User Access to Online Services and Adapt to Future Changes
Managing user access to online services is an ongoing dilemma for most organizations. Unsanctioned services decrease user productivity and increase your risk of malware infections or the exposure of confidential data. New online services are introduced every day while existing services often undergo updates that break the solutions that were implemented previously to manage access to them.
The iboss platform includes many built-in controls that can be used to manage user access to the most common online services. Adaptive Access Control complements the built-in controls by adding the flexibility needed to address new online services or adapt to future changes to existing ones.
Let’s revisit the first scenario. The organization can easily add a rule that redirects attempts to access the dropbox.com domain to https://<your-org>.box.com (Figure 1). But what about the requirement to be able to add additional domains easily. Adaptive Access Control makes it easy to update the conditions for a rule without having to recreate it. In addition to adding other domains to be redirected, you have the flexibility to add different match types, such as a specific value from an HTTP Request header, port ranges, or even group policies.
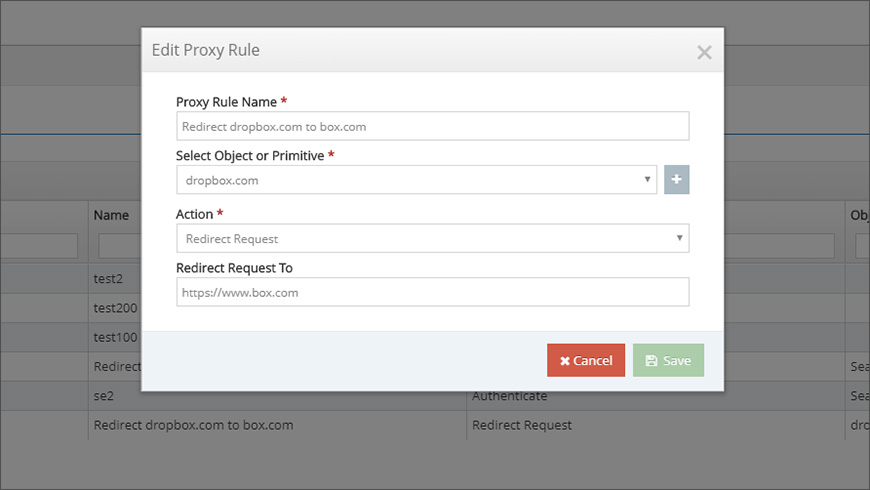
Modular Design Allows For Finer Granularity When Defining Rules
In a perfect world, a rule only affects the items that you intend, and nothing more. If the logic for a rule is overly broad and inclusive, it may be applied to unintended targets.
Recall the hospital scenario that was introduced earlier. To allow the MRI machine to access the external server, you could just add a simple rule that automatically bypasses proxy authentication for all traffic going to the domain needed by the MRI machine (Figure 2). While this rule would allow the MRI machine to access the external domain, the logic is so broad that the bypass would also be applied to all other devices.
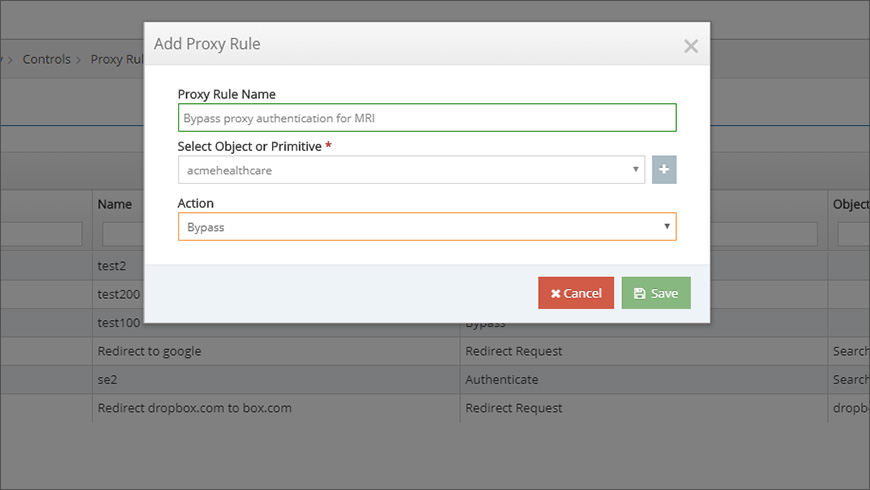
This rule can be improved by adding a second condition that restricts the rule’s scope to traffic that matches the IP address that is used by the MRI machine. To keep things simple, we’ll assume that this MRI machine either has its own public IP address or that it’s sharing an IP with a small group of similar devices.
Adaptive Access Control uses a modular approach that enables you to define conditions and rules independently of each other. The logical separation frees them to be associated with each other in many different combinations, maximizing the logical possibilities.
What Exactly Are Objects and Primitives, Anyway?
Now that we’ve covered the theory, it’s time to introduce primitives and objects, and learn how you can use them to build new rules.
Don’t worry if this terminology is unfamiliar. You’ll be an expert by the time you reach the end of this article.
Primitives
A primitive is a match condition, or pattern, that is used to define when a rule is triggered (Figure 3). Primitives can be IP ranges, port ranges, domains, group policies, or even HTTP request header values. When a network event occurs that matches the condition that is defined by a primitive, the state of the primitive is set to a logical value of “true.” While it’s possible for a rule to use only a single primitive, many rules require more. That’s where objects come in.
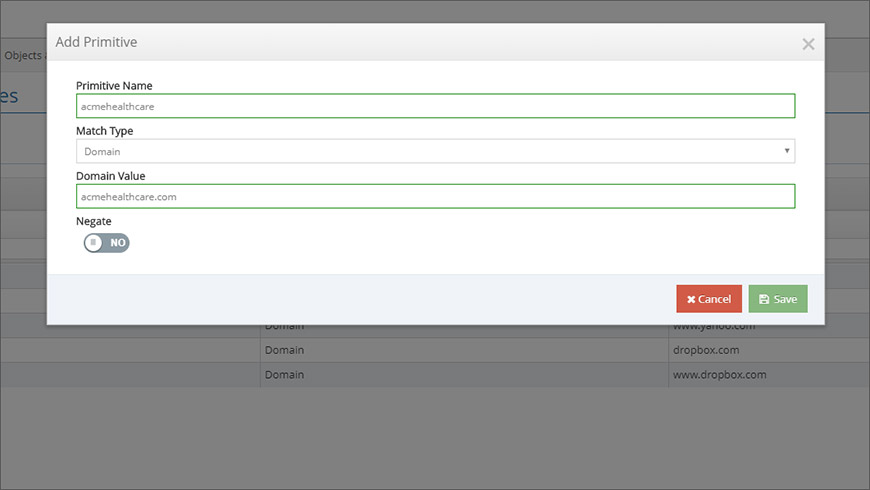
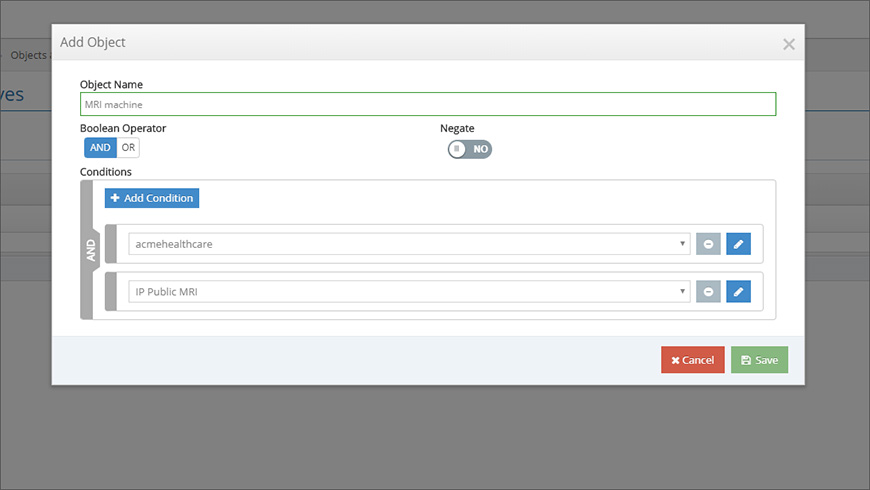
Objects
An object is a container that groups multiple primitives into compound conditions (Figure 4). Within an object, you can set the logical dependencies between multiple primitives with logical operators, like AND, OR, and NOT. An object allows a set of multiple primitives to be evaluated as a single item, regardless of how many actual primitives or logical operators it contains.
Rules
After you create a new object or primitive, you can add it to a rule. A rule is triggered when the state of the primitive or object becomes “true.” You can specify the action that is performed when the rule is triggered. Possible actions include domain redirection, bypassing or enforcing proxy authentication, and even modifying HTTP Request headers.
Here’s a diagram that illustrates the relationships between rules, objects, and primitives, using the components from our hospital scenario (Figure 5).
Step-by-Step Introduction
Here’s a quick overview of how the Adaptive Access Control works.
Step 1: Locate Objects & Primitives
From the iboss Home page, click the Web Security tile. Notice that the sidebar contains an Objects & Primitives button (Figure 6).
Step 2: Add a Primitive
Before creating a new rule, you’ll need to add a primitive.
Click the Primitives tab, followed by the Add Primitive button. From the window that opens, you can define the match pattern. Notice that there is a long list of match types available. This gives you a comprehensive toolkit that you can use to match a variety of network patterns and conditions.
An individual primitive can only have one match pattern, but you easily can add more primitives if you need to match multiple conditions. Remember that you can reuse the same primitives and objects that are already being used by other rules.
Step 3: Create an Object
If the new rule requires more than one primitive, then you must also create a new object to contain them.
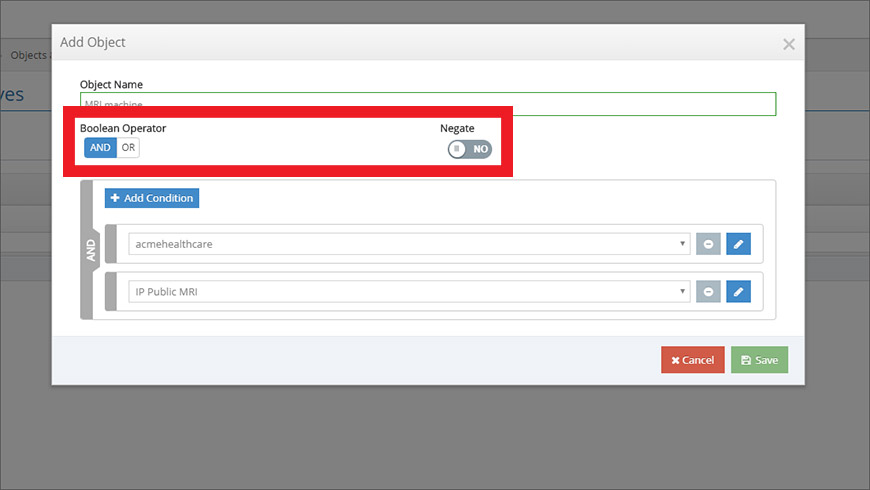
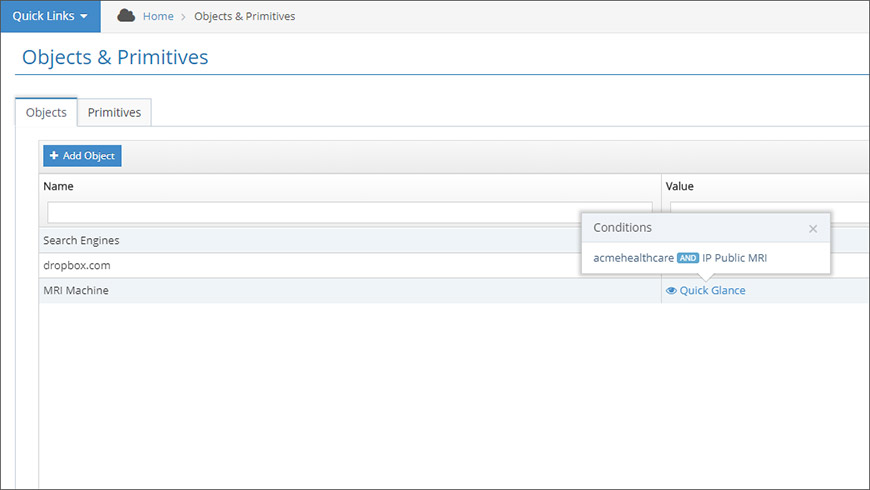
Click the Objects tab, followed by the Add Object button. From the window that opens, you can add primitives into the Condition fields. Use the Boolean Operator switch (Figure 7) to toggle between the AND and OR logical relationships between the primitives. The logical NOT operator is represented by the Negate switch (Figure 7).
After a new object is created, the Quick Glance tool (Figure 8) makes it easy for you to review the logical relationships between the conditions.
Step 4: Define a Rule
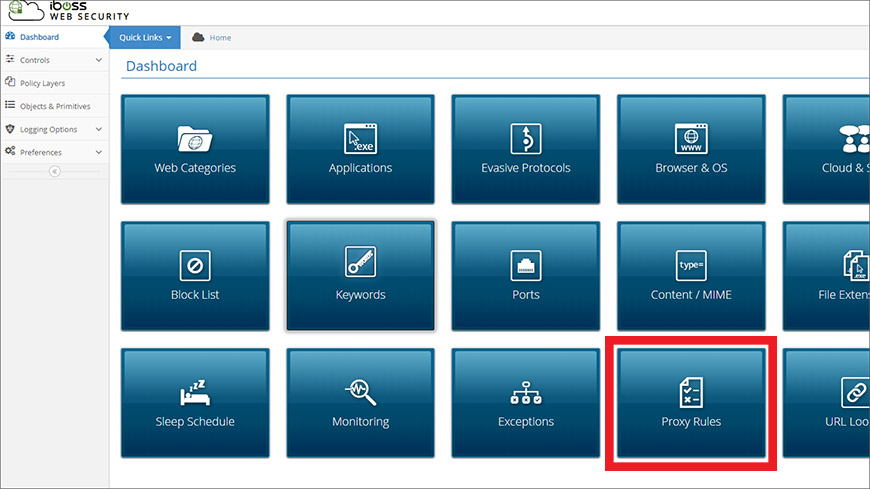
Unlike primitives and objects, rules are created in the Proxy Rules section.
To access the Proxy Rules, return to the iboss Home page and click the Web Security tile. From the new list of tiles, click the Proxy Rules tile (Figure 9), followed by the Add Proxy Rule button.
Summary of Key Features
Let’s review the key features of Adaptive Access Control.
- Design custom rules to manage user access to online services that are too new to have built-in Web Security controls
- Apply the modular system of objects and primitives to devise a variety of logical solutions to network challenges
- Easily define new match conditions by adding primitives
- Build compound conditions by grouping multiple primitives into objects
- Freely edit and reuse existing primitives and objects with multiple rules without having to recreate them
