Blog for
Business
popular topics:
network security cloud security SASE zero-trust Ransomware Cloud Adoption CASB API CASB Remote Browser Isolation RBI policy REvil Microsoft partnership Secure Access cloud connector Cybersecurity agent backhaul cybersecurity guidelines Data Breach CISA Directive Technology Alliances DLP Cloud App Isolation plan Redirect YouTube MDM product updates NATO LinkedIn Data Breach Kayesa Microsoft 365 Future of Work FedRAMP K-12 data leak executive order cloud security awards industry awards best of network security best network security Data Loss Prevention Exact Data Match Ping Identity Technical Alliance Partnership Federal Security cyber hygiene objects primitives rules conditions reporting risk dashboard cloud connected inventory count Restricted Mode Allow List override block pages country block file uploads iOS iPad Safari Google Classroom Chromebook ChromeOS keyword filter Android Always-on VPN Lockdown mode FTP Relay private access cyberattacks 5G Workplace security 5G technology EA Sports Mass Tech Companies IPO Kaseya Colonial Pipeline JBS Healthcare HIMSS Microsoft reverse proxy passwords education advanced threats nation-states Company of the Year Globee Awards Security Cloud Cybersecurity Awareness Month cybersecurity awareness Be Cyber Smart web security secure web gateway Twitch hack ATARC momentum cyberattack Port of Houston civil cyber fraud vulnerabilities Partnerships APIs Technology Integrations modern workforce hybrid workforce strategies hybrid workforce model Top Cybersecurity Vendors CRN SAML Technology Partnerships IAM identity partnerships SSO Alliance Partners Identity Defenders Network Behavior Homeland Security Awards crisis management k-12 cybersecurity NIST ForgeRock Best Companies to Work For Best Places to Work Battery Ventures Best Enterprise SaaS Cloud Awards Apache Log4j Log4Shell Top Cybersecurity Company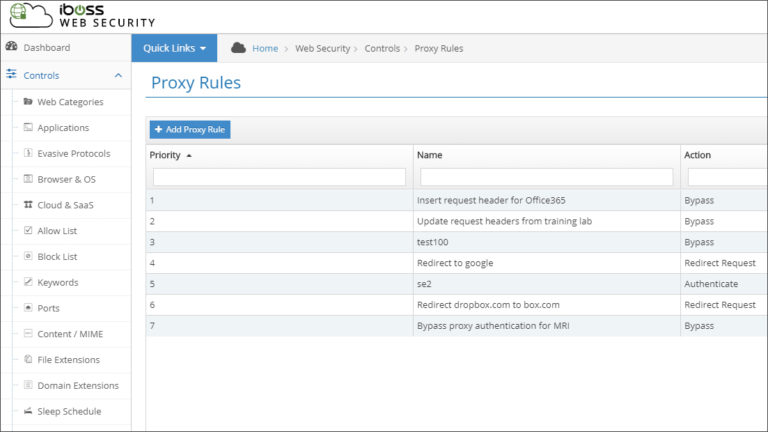
May 9, 2019
Redirect or Modify User Network Traffic Automatically by Creating Custom Rules
No two networks are exactly alike. This means that you must occasionally find workarounds for challenges and...
Redirect
objects
primitives
rules
conditions



