At iboss, we are dedicated to the mission of providing more effective Internet security, secure access to apps and increasing visibility across your devices no matter where users are connecting from. The iboss 9.8 release contains dozens of features that make it easier to enforce user Internet access and meet your organization’s policies as well as ever-changing regulatory compliances. In addition, we added features to increase visibility on the security posture of devices across your organization as well as improved threat detection capabilities. Updates will be available across the iboss cloud starting in early April 2019.
- User and Entity Behavioral Indicator Dashboards to Identify Risky Behaviors
- Augment User Behavior to Protect Against Data Loss by Leveraging Adaptive Access Control
- Inventory and Control for Your Cloud Connected Devices Regardless of Location
- Ensure Safe and Compliant Access to YouTube by Enforcing YouTube Channels and MyOrgVideos
- High Risk Browsing Controls Help Protect Users from Being Exposed to Online Threats
- Mitigate Potential Risk with Web Category Soft Overrides To Warn Users Before Loading Sites
iboss 9.8.0 Features and Highlights
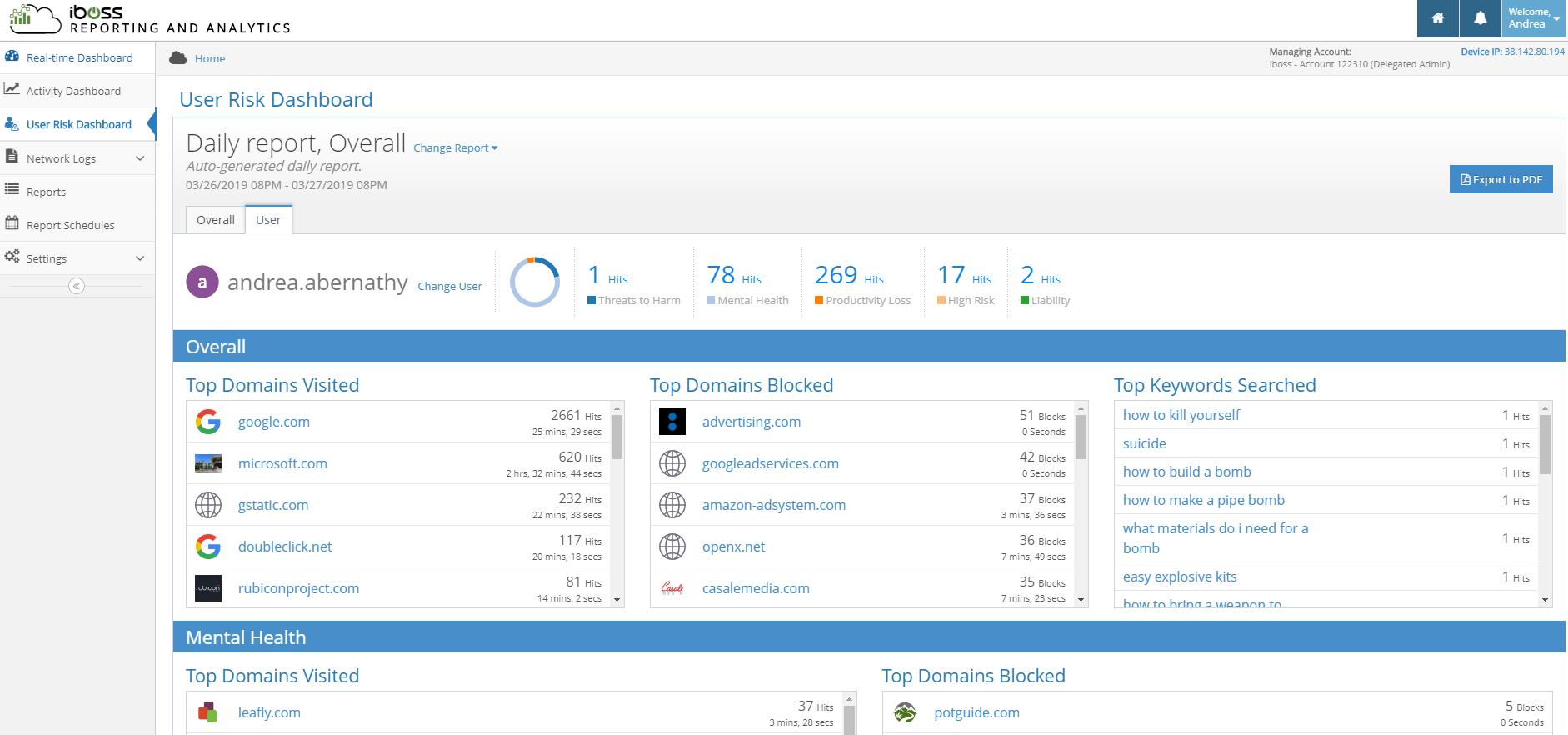
User and Entity Behavioral Indicator Dashboards to Identify Risky Behaviors
The new User Risk Dashboard shows top users of concern, especially useful for helping to flag at-risk or high-risk individuals. The dashboard contains two views – Overall and User. The Overall tab displays top users of concern for those browsing to sites in categories such as Mental Health, High Risk, Threats to Harm, Productivity Loss, and Liability. From there, you can drill down into a specific User view. The user-specific view shows the top domains visited and blocked within each of those categories for the selected user, the number of times the user has visited the site, and the total duration of time the user spent on each site.
Example Use Cases:
- A Principal or Administrator needs a report on all of a particular student’s activity when investigating or responding to an incident
- Management would like an overall summary of high risk behaviors and potential productivity loss for workforce monitoring
Augment User Behavior to Protect Against Data Loss by Leveraging Adaptive Access Control
The Adaptive Access Control feature provides organizations with powerful governance over user Internet access making it easier to meet internal and regulatory compliances and protect against shadow IT. Advanced policies go beyond static group-based access policies by allowing advanced policies based on any combination of a user, security group, destination IP or location.
Example Use Cases:
- Redirecting specific users (ex. contractors) attempting to access the corporate Microsoft Sharepoint page to a block page
- If a user attempts to access a personal DropBox page, redirect to a Corporate DropBox page or similar corporate file sharing site mitigating Shadow IT
- If a website requires an HTTP header such as with Microsoft Office 365, you can set policy to automatically inject one
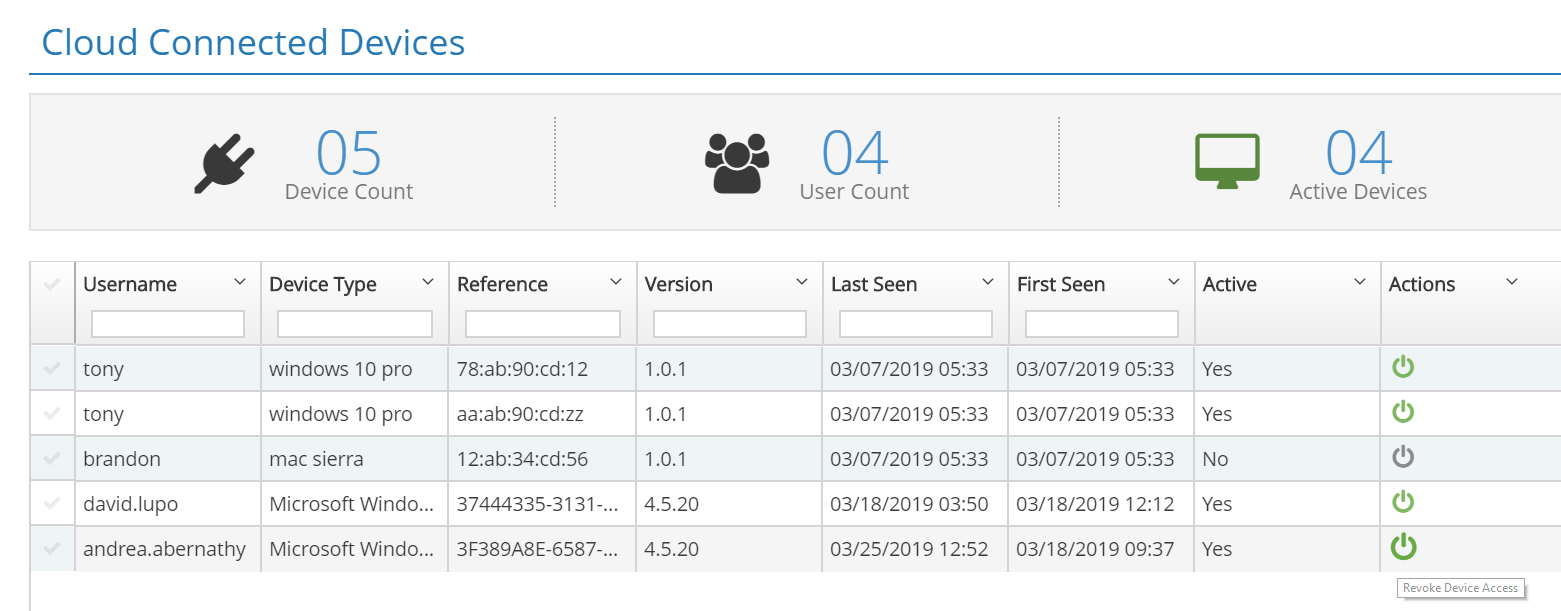
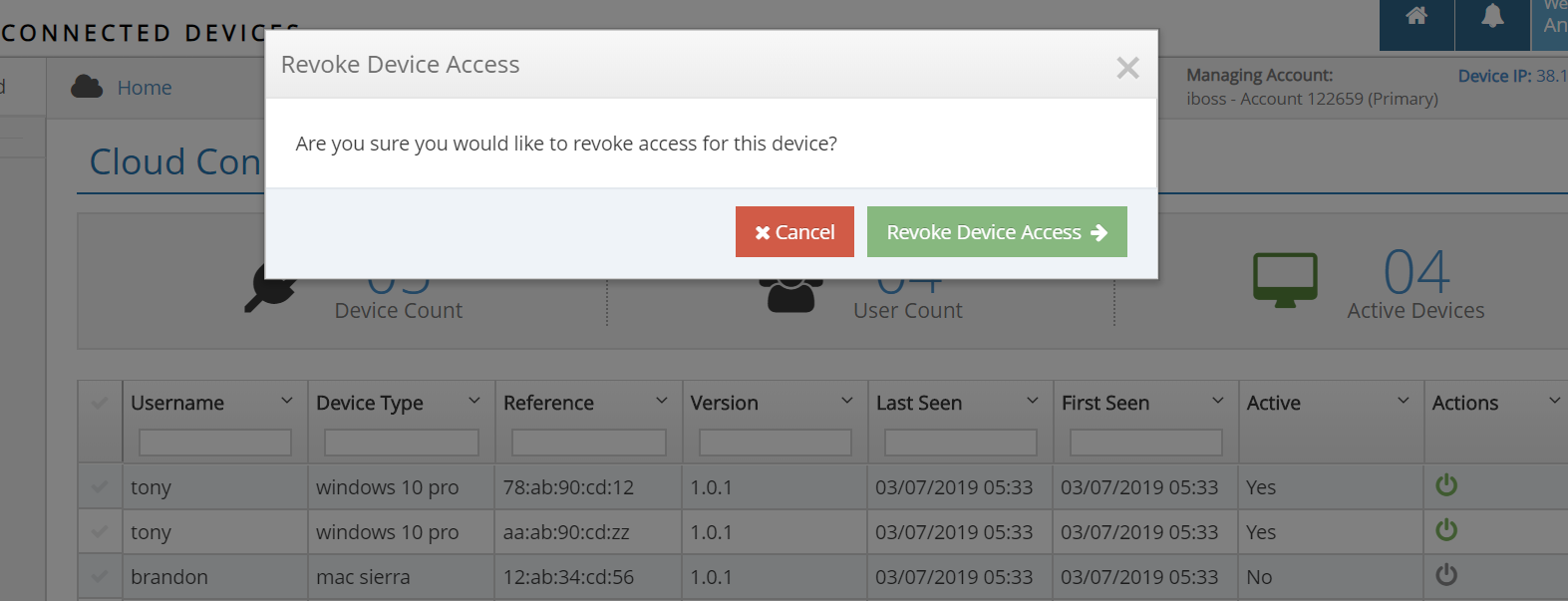
Inventory and Control for Your Cloud Connected Devices Regardless of Location
The Cloud Connected Devices Dashboard provides instant visibility for all of the enrolled devices across your organization regardless of where in the world they are being utilized. In addition to identifying cloud connector devices, the page also provides vital information including the associated user, type of device, reference ID, version, first and last seen, its active status and also provides actions to remove the device from the iboss cloud.
Example Use Cases:
- Identify a compromised device and immediately remove that device from the network
- Help shorten incident investigation response times by identifying user/s associated devices that may have been compromised
Ensure Safe and Compliant Access to YouTube by Enforcing YouTube Channels and MyOrgVideos
YouTube Channels & MyOrgVideos provide users safe access to YouTube protecting them from inappropriate material while also allowing your organization to promote focused content. The YouTube Channel enforcement feature redirects to your organization’s YouTube Channel restricting general access to YouTube.
MyOrgVideos adds to the focused content list by providing the ability to bypass YouTube Safesearch on a per video basis. Further, if hosting a training or classroom session, the content can be timed out after minutes or days, making it easy to manage the video lifecycle.
Example Use Cases:
- Your organization’s Internet access policy restricts YouTube access but you require access to training videos on YouTube. Now users can be redirected to your organization’s YouTube channel allowing access to only the training material.
- A teacher wishes to show content to a class on a particular subject which is restricted under YouTube Safesearch. With this feature, the video can be added to the allow list, timing out the URL the day after the showing is scheduled.
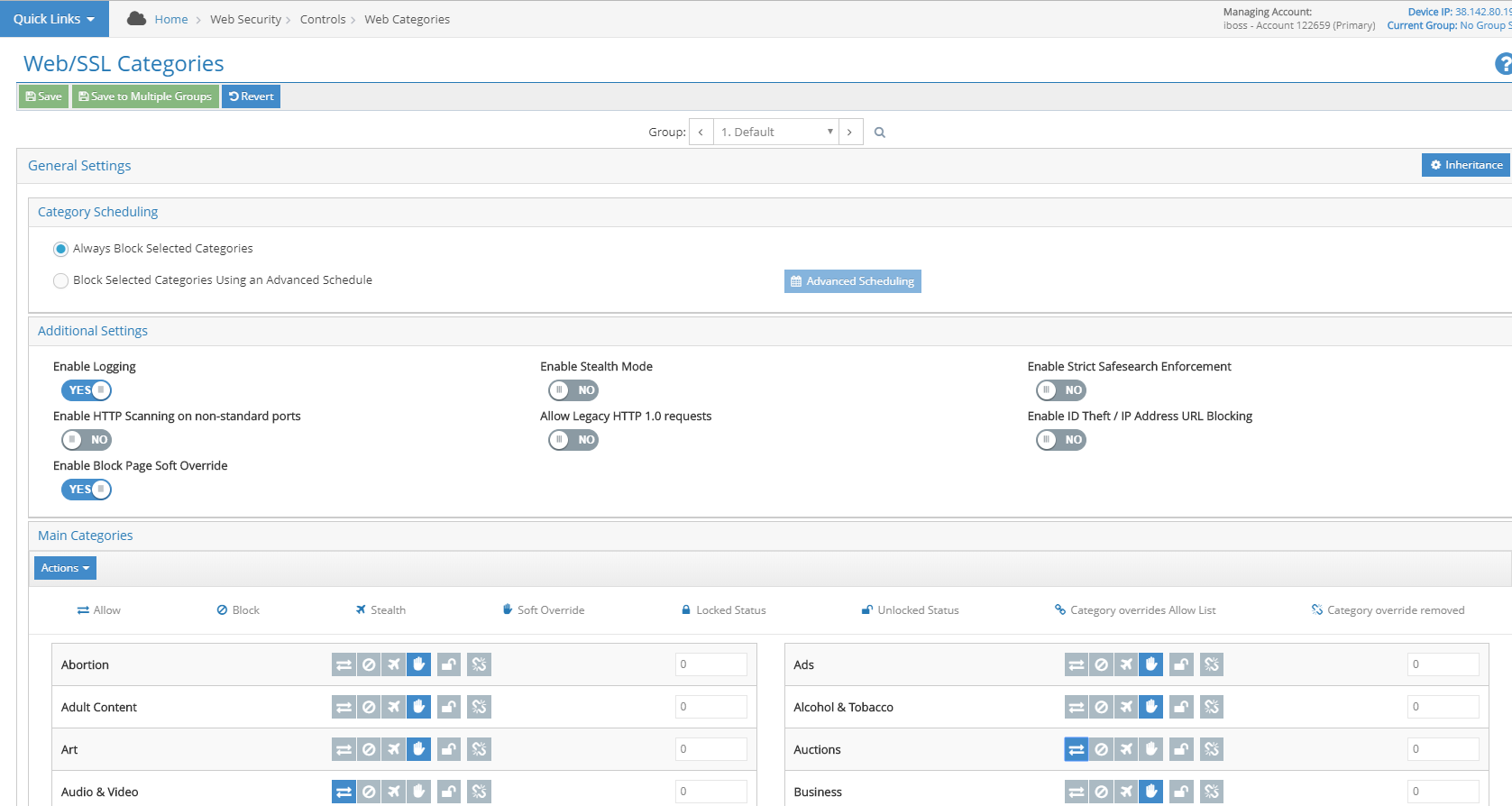
Mitigate Potential Risk With Web Category Soft Overrides To Warn Users Before Loading Sites
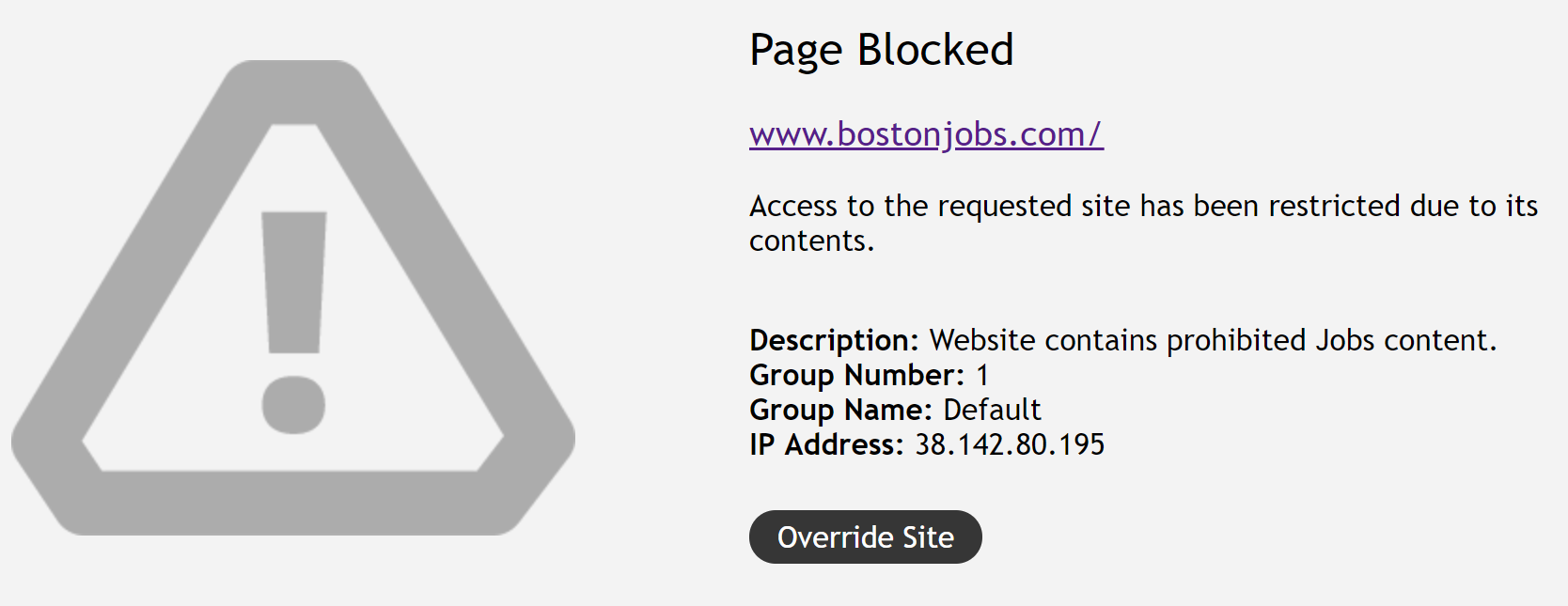
Certain users may need to access otherwise blocked content at their own discretion. Soft Overrides provide the flexibility to configure block pages that still allow the user to proceed to the destination. The Soft Overrides can be configured on a Web Category basis. If a Soft Override is enabled, an ‘Override Site’ button is presented on the block page, allowing the user to proceed to the site if desired.
Example Use Cases:
- Your organization may need to provide some users more freedom when browsing to certain categories of websites. The soft override block can be configured to allow the user to access the content at their own discretion. For example, the HR team may need to access Jobs sites for recruiting purposes, but the initial block page is a warning to the rest of the organization.
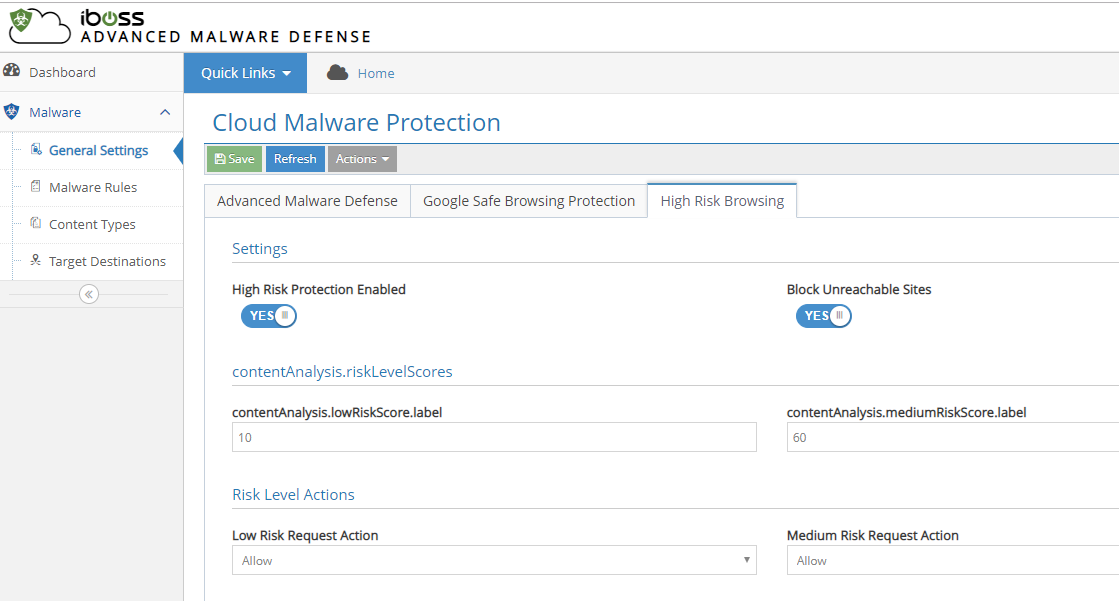
High Risk Browsing Controls Help Protect Users from Being Exposed to Online Threats
High-Risk Browsing Controls help protect users from being exposed to online threats from potentially compromised websites. The feature monitors websites behavior based on various aspects of its behavior to create a score that if met allows it to dynamically restrict access to users. This increases threat detection for compromised sites that have not yet been classified by reputation or signature-based anti-malware engines.
Example Use Case:
- Your organization seeks to increase protection for high target users such as members of the finance department. By enabling High Risk Browsing Controls, users in this group gain an additional layer of protection for their web browsing activities and prevent against data loss
Coming Soon!
We have yet another release in development as we plan on continuous delivery of new functionality. Here are some highlights of what is to come:.
YouTube Library
- With general restrictions in place for YouTube, specific channels can still be permitted for use. A Library of approved YouTube channels defining what users can access is easily created through iboss Management Console.
GeoLocation Access Restrictions
- Block list by GeoLocation: Restrict access based on where a user is connecting from for additional security and compliance purposes.
SD-WAN
- Simplified GRE Tunnel Deployments: Enter your networking parameters, select your router vendor, and download the configuration template for your router making it even easier to integrate with SD-WAN.
PAC Enhancements
- PAC Subzone: Define on a more granular basis when and how to proxy devices to the gateway so you can apply web security policies and threat control features.