Schools Face 50x More Attacks Than Financial Institutions
According to Microsoft Security Intelligence, from April 15 through May 15, over 80% of all cyber attacks targeted U.S. public schools as compared to only 1.5% of financial institutions. More than 5.7 million school devices encountered an attack within a 30-day span with criminals leveraging social engineering as the preferred approach.
Students and staff have increasingly accessed school resources remotely, with many of those resources stored in third-party cloud apps. This environment has exposed weaknesses in schools’ legacy cyber security architectures which were originally designed to secure students, staff, and school resources while they were on site. Cyber criminals have identified this weakness and unleashed a feeding frenzy. This impact is nothing less than astonishing. In 2020 alone, 77 ransomware attacks on U.S. schools impacted 1.3 million students, resulting in 531 days of downtime at a cost of $6.6 billion. Unfortunately, these attacks are only increasing.
Schools must modernize their cyber security architectures and implement new cloud-based technologies to protect students, staff, and resources regardless of how or where they are accessing the internet. If learners are to be prepared to compete in this global economy, we must implement cybersecurity strategies to meet new challenges facing the U.S. school system.
Regardless of the amount of cybersecurity training, people make mistakes and often expose networks to cyberattacks. School networks are never fully inoculated. There is good news: As districts must comply with the Children’s Internet Protection Act (CIPA), most schools have budgets to invest in effective solutions. However, most technology vendors that support school networks focus on filtering website access or provide parent portals to track what websites students visited while at school. Amidst all the noise, no current K-12 content filtering solution can claim to be third-party validated or deliver services to the most highly regulated verticals such as healthcare, banking, or critical infrastructure, in alignment with critical infrastructure sectors (Critical Infrastructure Sectors | CISA).
While many of these services and products are well intended, they often provide a false sense of confidence that filtering student content and offering parents access is good enough. Per the Microsoft report and noted in this graph, attacks across the global Education infrastructure are growing at a rapid pace:
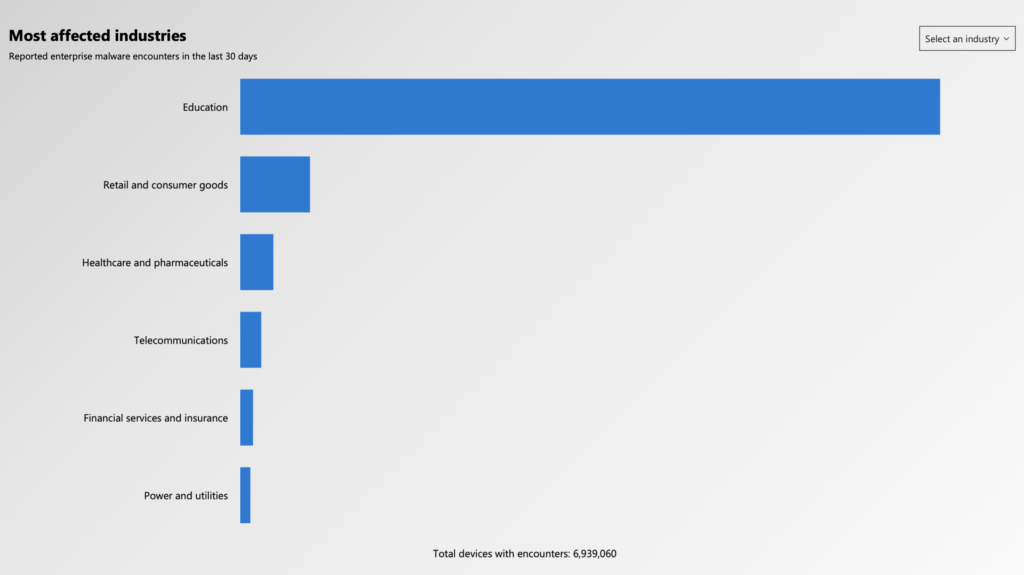 Source: Microsoft Security Intelligence – https://www.microsoft.com/en-us/wdsi/threats
Source: Microsoft Security Intelligence – https://www.microsoft.com/en-us/wdsi/threats
Within the U.S., the K12 SIX report highlights the rise in domestics K-12 attacks as seen below:
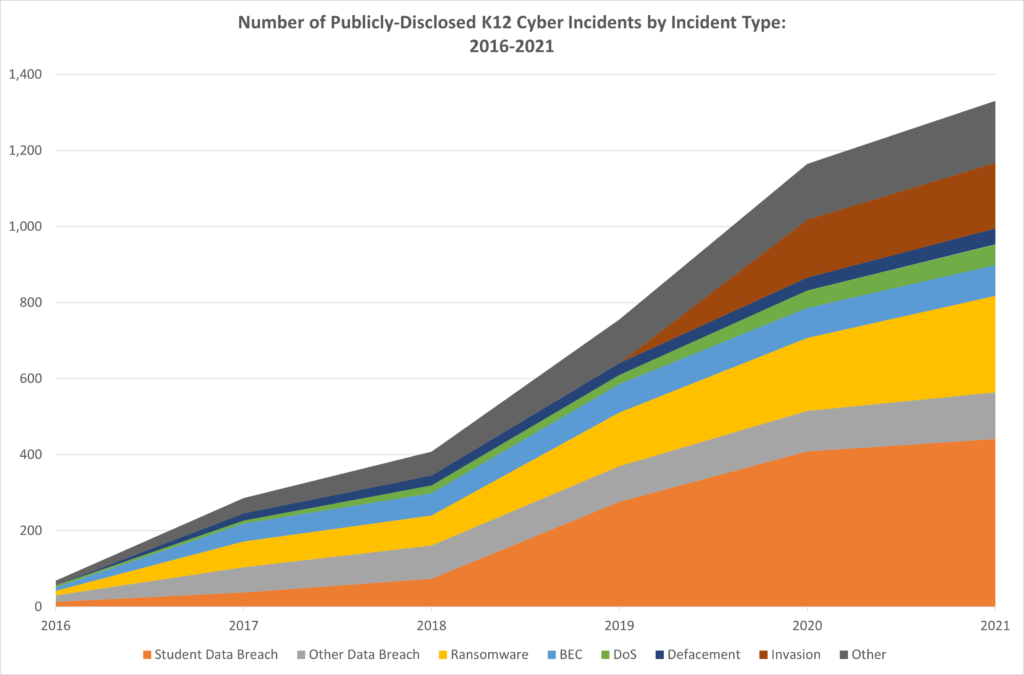 Source: K12 SIX report: The State of K-12 Cybersecurity: Year in Review
Source: K12 SIX report: The State of K-12 Cybersecurity: Year in Review
Determining if a district has the right content filtering/cybersecurity platform to address growing risks is not difficult. Those who serve as General Counsel, Chief Business Officer, IT Director, or Chief Information Officer should ask their IT teams if their content filtering products meet industry, compliance and certifications standards. Ask if your content filtering cloud service maintains its own global cloud cybersecurity Zero Trust infrastructure (the preferred posture) or if it is renting bandwidth through third-party cloud services – which introduces significant risk, as evidenced by the escalating number of school district breaches emanating from those third parties. Inquire if the product is compliant to SOC 1 auditing, which is conducted for products that handle/protect financial information and sensitive data. Most, if not all, K-12 content filtering services can’t support anything beyond filtering student content and providing parent controls. This is a tricky proposition for school leaders, especially Chief Academic Officers, as many parents gather data without direct interaction with the school/teachers.
Based on the data, moving school districts to an enterprise-grade Zero Trust cloud solution can provide true confidence to safely operate in a digital learning environment. The National Institute of Standards and Technology (NIST) has produced a cybersecurity framework in which all U.S. Federal agencies must comply. The NIST Special Publication 800-207 defines Zero Trust as a set of cybersecurity principles used when planning and implementing an enterprise architecture. These doctrines apply to endpoints, services, and data flows. Because K-12 operates enterprise networks, this framework is essential. Getting started is easier than you might think. The new NIST planning guide for 800-207 can serve as a helpful framework. Additionally, if you are considering positioning your school district for Zero Trust, we recommend you embrace a solution that supports thousands of school districts, including the largest in the nation. iboss is that solution which offers all schools the ability to embrace a Zero Trust SSE for K-12.
Below are a few key reasons why all U.S. school districts should consider embracing the NIST Zero Trust framework:
- Zero Trust Provides Increased Layers of Cybersecurity: Cyber attacks on the Education sector are on the rise. Due to a lack of security, criminals can find their way past school district perimeter defenses. Zero Trust cybersecurity frameworks suggest a multilayered strategy, allowing IT to protect resources rather than perimeters. Zero Trust enables IT to monitor abnormal behavior within school network information systems. Once abnormal behavior is spotted, user access can be immediately controlled.
- Zero Trust Secures Data Accessed from Anywhere: Teachers and students, now more than ever, rely on public networks to facilitate homework, attend class and monitor grading. Perimeter security, including firewalls and content filters, will not protect a district’s data from bad actors. It’s a matter of time before public internet access is exploited; ZTA protects against this inevitability.
- Zero Trust Prepares Districts for Emergencies: When emergencies arise, Zero Trust cybersecurity is the only method that ensures districts are prepared. As is the case with COVID-19, districts using a Zero Trust strategy don’t need to worry as much about access from public and/or unsecured networks. Zero Trust provides the security, visibility, and control needed, regardless from where users log in or what device they are using.
Finally, providing students and district personnel the ability to share and engage personal and sensitive data through third-party cloud vendors, though often necessary, is risky at best. However, directing that traffic through a content filtering service renting cloud capacity from a third-party cloud provider is simply asking for trouble. Unlike all K-12 content filtering providers, only iboss provides its education customers with a Zero Trust SSE/Secure Cloud Gateway built from cloud work units, or containerized nodes. These nodes are dedicated to processing data for a single student or district employee.
Moving away from traditional outdated content filtering services and products over to a Zero Trust disposition could be the difference between having networks held hostage during testing, impacting bond and insurance ratings, or creating public embarrassment. This can be avoided by evaluating your current readiness, and if it does not meet some of the enterprise standards covered in this article, we recommend you reconsider.
For more information about iboss Zero Trust SASE for K-12 and the entire Education sector, please visit iboss’ site for Education.
Blog post authored by Richard Quinones, Senior Vice President, Public Sector at iboss.

