Easily Protect Mobile User Internet Access On the Road or At Home
The iboss cloud was designed for the cloud-first and mobile world. Regardless of whether users are onsite, on the road or at home, they are always connected to iboss cloud which means that they are always protected while accessing the Internet and cloud applications.
Protecting Users with iboss cloud Overview
The iboss cloud was designed to follow users, not buildings, to ensure access to the Internet is always secure regardless of user location. The iboss cloud lives in the cloud allowing users to be connected to Internet security at all times. This ensures compliance, malware defense and data loss prevention is applied to all Internet access at all times. Because of its modern containerized cloud design, the iboss cloud can secure mobile users instantly with the following benefits:
- As users move from working inside the organization to working on the road, the security policies being applied to Internet activity are identical, providing consistent security
- The user experience inside and outside of the organization’s physical perimeter are exactly the same, because they are protected by exactly the same platform and technology regardless of location
- Secure users from Internet malware and data loss while ensuring compliance inside and outside of the organization
- Automatically associate usernames and apply dynamic policies that are associated with directory services such as Active Directory of ADFS
- Visibility into cloud application and Internet use is available regardless of user location providing more insight and visibility which reduces risk
- Decrypt encrypted HTTPS traffic at scale to gain visibility into traffic payloads to prevent malware and data loss while enforcing compliance
- Advanced zoning capabilities allows administrators to create geo-location based zones based on user location for GDPR compliance
- A true SaaS platform, the iboss cloud scales infinitely as users consume more bandwidth without burdening IT as the complexities are completely abstracted from the organization
Challenges Related to Cloud Adoption and Mobility
SaaS cloud applications are changing everything, including the way people work and how organizations operate. Modern cloud applications require fast connections and large amounts of bandwidth. The way user Internet access is secured must change as well and move to the cloud. Using traditional approaches involving perimeter-based security appliances result in the following challenges:
- Security and proxy appliances can quickly become saturated, reducing network speeds and impacting user productivity
- Cloud applications can be accessed by users from anywhere. Backhauling or hairpinning user traffic while they are remote back through the organization’s network before going to the Internet results in a variety of unsustainable challenges:
- The amount of bandwidth running through the organization’s network will quickly increase due to additional mobile traffic resulting in substantial bandwidth costs
- The number of proxy appliances hosted at headquarters will drastically need to increase due to the extra load from mobile and remote users resulting in substantial costs
- The user experience will be poor as data traverses back to headquarters before heading to cloud applications causing extra hops and latency
- If using Office 365, this design principal goes against Microsoft’s recommendations which state that data should traverse directly from users to Office 365 in order for Microsoft to optimize connectivity
- IP login restrictions and Zero Trust become difficult to enforce if users are connected directly to the Internet while they are remote since their IP address does not originate from the organization’s network. This reduces an organization’s security posture
The iboss cloud is Designed for Mobility and the Cloud
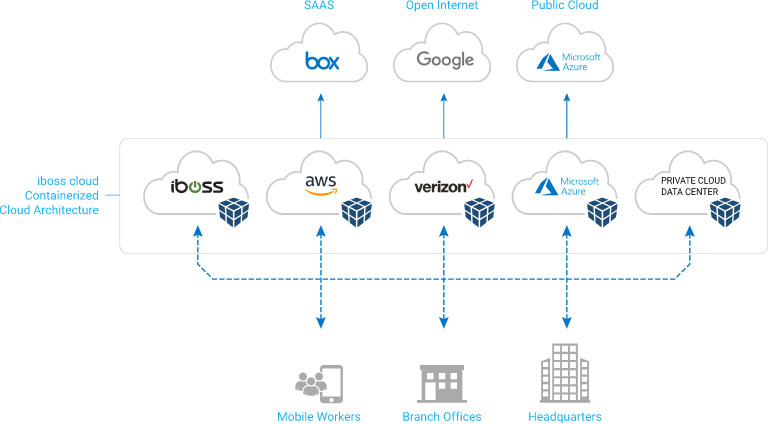
The iboss cloud runs in the cloud next to where the applications run ensuring fast connections for high user productivity. The iboss cloud is Internet security that follows users wherever they go and delivers immediate value through its native SaaS delivery model.
Consistent Security and User Experience Regardless of Location
The traditional network perimeter is gone and users are no longer bound by four walls. Users can work from anywhere with cloud applications being available wherever they go. The iboss cloud is designed for mobility and ensures users are always connected to iboss cloud before accessing the Internet. Because users are always connected to iboss cloud, data will be scanned for compliance, malware defense and data loss as they access cloud applications and resources on the Internet. This protects users and the organization from risk, malware infections and data loss by preventing unsafe data transfers automatically. This protection runs transparently to the user and the user experience is always consistent as they are always connected to the same cloud platform.
Automatically Associate Username and Dynamic Internet Security Policies
The intelligent iboss cloud connectors ensure data is always flowing through the iboss cloud regardless of user location. They automatically associate the logged in username with a device so that detailed log events are associated to the user. The connectors also map a dynamic security policy to the user by leveraging the user’s groups and Organizational Units (OUs) from directory services such as Active Directory and ADFS. There is no need to open firewall ports or expose Directory Services to get this feature. The iboss cloud connectors obtain this information from the verified credentials used on the device itself.
Gain Visibility and Control Into Cloud Application and Internet Use
In a traditional scenario, Internet security and visibility is strong when users are within the organization’s four walls. As soon as a user leaves the organization’s perimeter, security and visibility become obscure or non-existent. Using VPNs to backhaul traffic to on-prem security appliances only slows down user connections to cloud applications reducing productivity and increasing frustration. In addition, this requires the VPN to be running at all times which is typically not feasible. The iboss cloud provides visibility and control for cloud application use inside and outside of the organization seamlessly. Detailed logging, including username and detailed full URLs, are always captured whether the user is inside of the organization or on the road. This information is provided to IT staff and administrators through the single pane of glass iboss cloud admin console. Best of all, it eliminates hairpinning data through hosted appliances reducing costs and increasing speeds for most productivity.
Decrypt and Inspect HTTPS Traffic at Massive Scale
The iboss cloud can selectively decrypt HTTPS traffic for visibility, control and protection of encrypted traffic. It can do this selectively by user, group, domain, category as well as a variety of other criteria. Decryption is performed in the cloud, so scale is never a problem. Horizontal scaling allows an infinite amount of data to be processed as bandwidth increases and encryption key sizes become larger. Since users are always connected to the cloud, this includes visibility while users are on the road to ensure consistent protection at all times.
Create Geo-Based Zones for Data Sovereignty and GDPR
The iboss cloud has advanced zoning capabilities that allows administrators to create zones which are used to secure users as they move from place to place. The zones contain the containerized cloud gateway capacity that scans data within the zones and can store reporting event logs within the zones as well. The mapping of user data to zones is automatic and can be configured by country or region. This ensures compliance is being met while ensuring security at all times.
Eliminate Sending Unnecessary Internet Traffic Through Private Network Connections
When traffic is headed toward cloud applications such as Office 365, unnecessarily sending that traffic through private connections to centrally hosted security appliances is not only costly, but reduces user productivity substantially as Internet connections from branch offices are choked. Leveraging iboss cloud allows traffic to flow through the most optimized path directly to the Internet. This reduces load on MPLS links and valuable network resources, including firewalls and routers. It also extends the useful life of existing network appliances which will not need to reach their maximum throughput capabilities due to the offloaded direct to Internet traffic. This results in substantial savings and reduced IT labor costs.
True Cloud SaaS Platform
The iboss cloud abstracts everything needed to deliver the advanced security capabilities of the platform. This includes dealing with securing mobile users as they consume more bandwidth and move from place to place. IT administrators can focus on creating the security policies and working with reports instead of worrying about managing infrastructure or the headaches involved with securing users as they leave the traditional network perimeter.
How It Works
Getting started with iboss cloud is fast and easy. To get started:
- Get an active iboss cloud account
- Connect users to iboss cloud using an iboss cloud connector. Connectors are available for virtually all Operating Systems including Windows, Mac, iOS and Chromebooks
- Configure policies including compliance, malware defense and data loss
- The iboss cloud platform handles the rest and protects users regardless of location
Feature Highlights
Admin Controlled Geo-Zones
The iboss cloud includes admin controlled zones that can ensure data for users is scanned within specific regions and countries as well as logging events are stored within particular locations. This is a powerful feature for compliance and GDPR as well as for meeting other geo-based organizational needs. The iboss cloud allows for an unlimited amount of zones to be defined. Typically a zone will leverage the user’s source IP to match the user to a defined zone and use the zone information to route data from users to the iboss cloud appropriately.
Pricing
| Cloud Mobile User Security | Contact Us |
|
Cloud mobile security capabilities and features are included with every iboss cloud subscription at no additional cost. |
For more information about pricing and packaging, please visit https://www.iboss.com/pricing.
