iboss
Replace Legacy VPN, Proxy Appliances, and
VDI with a Single SaaS Security Service
iboss Zero Trust
Secure Access Service Edge
The revolutionary cloud security platform that provides
the capabilities of VPN, Proxy appliances, and VDI
in a single SaaS offering.
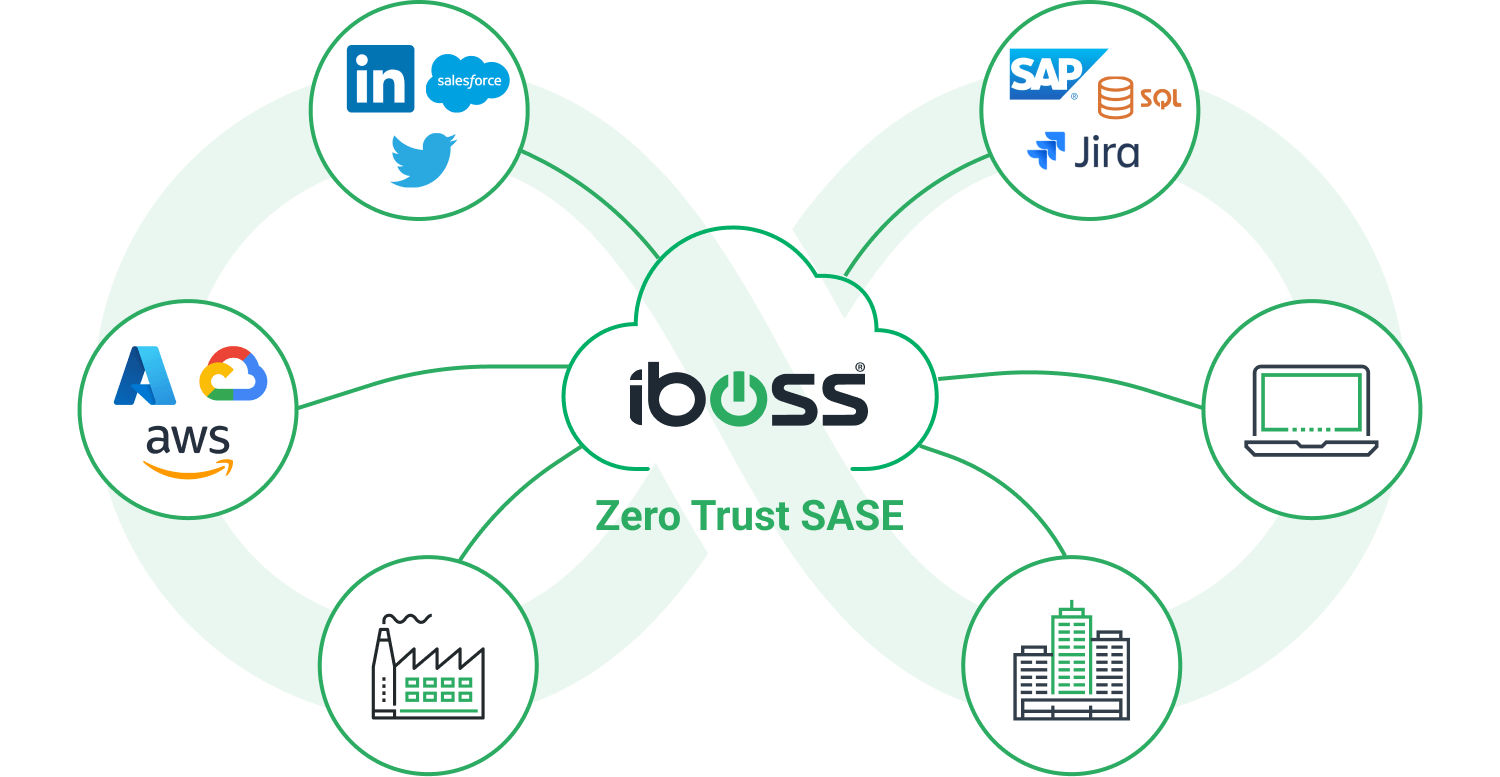
All users, data and services are connected through iboss
global cloud security service
The iboss Zero Trust SASE is a consolidated cloud security platform that replaces the capabilities of VPN, Proxy appliances, and VDI with next-gen ZTNA, Secure Access Service Edge, and Browser Isolation
By replacing legacy VPN with ZTNA, legacy proxy appliances with Secure Access Service Edge, and legacy VDI with Browser Isolation, the iboss Zero Trust SASE enables Network Administrators and Security Administrators to securely connect remote users to on-prem and cloud applications directly and securely with malware defense, compliance policies, Data Loss Prevention, CASB, and, logging applied to every transaction. The iboss Zero Trust SASE service can also deliver security functionality at scale and supports HTTPS decryption which allows for inspecting and applying security to data within encrypted connections. With the iboss Zero Trust SASE, Network Administrators and Security Administrators can reduce costs by eliminating the need for legacy VPN, proxy appliances, and VDI, as well as reduce the risk of breaches and data loss.
iboss Zero Trust SASE
Overview
Replace legacy VPNs with a Zero Trust Architecture that delivers improved security and the best end-user experience
Secure data with Zero Trust to avoid breaches and data loss, while providing a better user experience
Reduce risk of data loss and breaches with secure access to sensitive resources without granting access to the entire private network
Securely provide access to authorized resources from unmanaged devices without the high cost of traditional VDI solutions
Substantial cost savings with the latest cloud-based security technology
Always-on security, logging and visibility of all resource accesses
Seamless remote access with no end-user intervention, eliminating the need for users to manually switch on a VPN
Direct and secure connections with full visibility and logging for lightning-fast connections to Microsoft O365
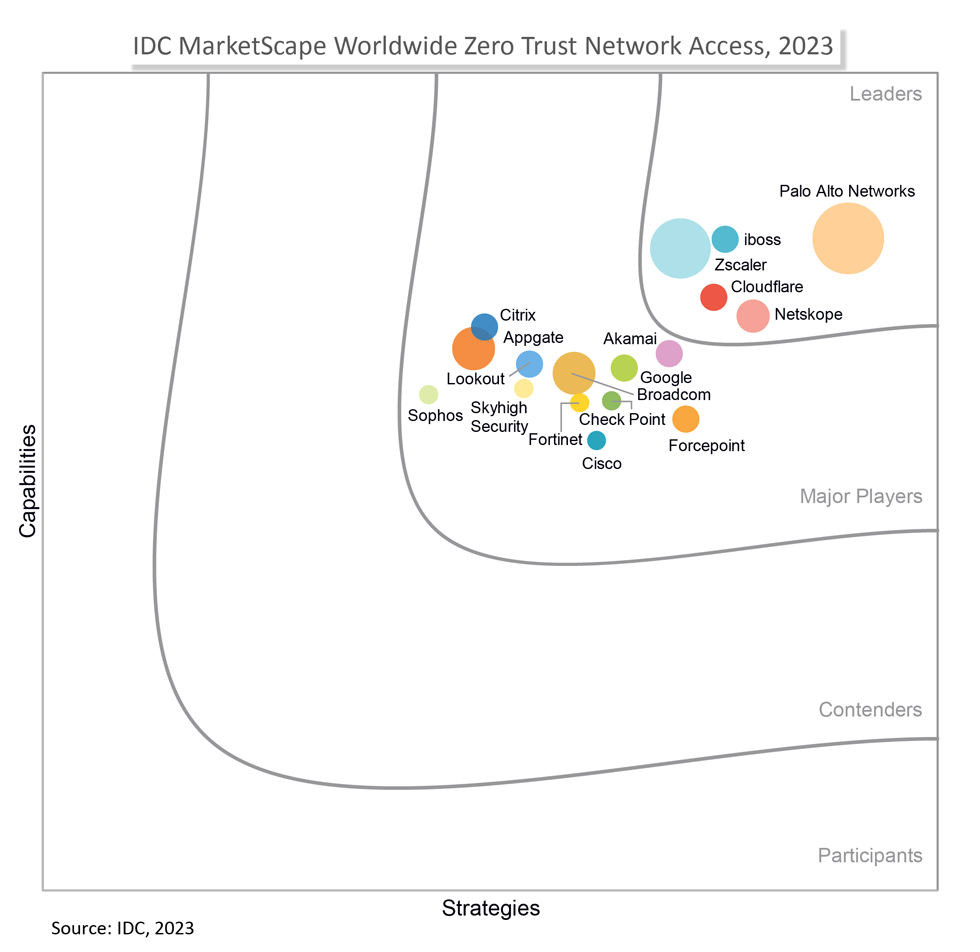
IDC MarketScape
names iboss a LEADER
iboss is recognized as a Leader in the IDC MarketScape for worldwide Zero Trust Network Access solutions.
Use Cases
Replace Legacy Proxy Appliances
Enable Secure App & Data Access for Remote Workers
Provide Application Access for BYOD, Contractors, and Third-Parties
Improve Connection Speeds to Microsoft O365 & Teams
Reduce or Eliminate Data Center Space
Challenge
Legacy network security proxy appliances are overloaded, causing latency and downtime due to increased traffic loads, struggle to keep up with HTTPS decryption, require costly renewals, and are approaching end-of-life hardware resulting in large hardware refresh projects.
Solution
Replace Proxies with iboss Zero Trust SASE. The iboss Zero Trust Secure Access Service Edge can be quickly implemented to replace legacy proxies and reduce costs through predictable per-user licensing and infinite security at scale delivered in the cloud.
Benefit
Substantial immediate cost savings with a sustainable long-term security strategy that can handle any volume of users and network traffic for better security, visibility, improved productivity, and the best end-user experience.
Challenge
As more organizations shift to remote work, secure access to apps and data is a growing challenge. Without the right security measures, companies can give remote workers access to the entire enterprise network, leading to data loss and breaches.
Solution
The iboss Zero Trust Secure Access Service Edge provides secure access to sensitive resources without granting access to the entire private network. ZTNA runs in the background so users can connect to the resources they need without turning on a VPN, and it’s more secure as it allows remote workers to access only the applications they are authorized to use.
Benefit
iboss ZTNA helps organizations reduce the risk of data loss and breaches by ensuring remote users only have access to authorized applications and data.
Challenge
Enterprises need the ability to securely give contractors and third parties access to sensitive applications, data, and services without risking data loss due to access from unmanaged devices.
Solution
The iboss Zero Trust Secure Access Service Edge offers a secure solution that allows users to access the resources they need without compromising security. Built-in Browser Isolation technology keeps data safe by granting access to services, data and applications through a VDI-like pane of glass that prevents data from touching unmanaged and third-party devices. Browser Isolation is agentless and eliminates the need to install temporary VPNs on third-party devices.
Benefit
Securely provide access to sensitive resources from unmanaged BYOD, contractor and third-party devices without the high cost of traditional VDI solutions with iboss Zero Trust SASE’s Browser Isolation technology which substantially reduces risks, costs and complexity.
Challenge
Organizations using Microsoft O365 are facing performance issues due to forcing Microsoft O365 and Teams connections through slow VPNs and overloaded legacy proxy appliances hosted in a datacenter.
Solution
The iboss Zero Trust Secure Access Service Edge provides direct connections to Microsoft O365 and Teams without sending traffic through a VPN or backhauling traffic through the datacenter. The iboss Zero Trust SASE provides Microsoft Tenant Restrictions, logging and security in the cloud and at scale to support any number of users with ultra-fast and direct connections to Microsoft O365 and Teams.
Benefit
Direct and secure connections to Microsoft through the iboss Zero Trust SASE improves user productivity, improves the end-user experience, improves simplicity, and substantially reduces costs.
Challenge
Organizations need to reduce or eliminate data center space to eliminate costs but VPN concentrators, Proxy appliances, and VDI infrastructure are currently hosted within those facilities.
Solution
With iboss Zero Trust SASE, all of the capabilities provided by VPN, proxy security appliances and VDI infrastructure are transitioned to the cloud and converted to a cloud service. In addition to eliminating datacenter infrastructure, ZTNA, Secure Access Service Edge, and Browser Isolation provides better security and scalability than the legacy approach provided with on-premises infrastructure.
Benefit
Eliminate or reduce data center space while significantly reducing costs. The iboss Zero Trust SASE will provide security to all users, IoT, and OT at scale for improved security, performance, and lower costs.
Challenge
Legacy VPNs are overloaded and insecure while they provide access to sensitive resources for remote users.
Solution
The iboss Zero Trust Secure Access Service Edge provides a quick and easy replacement of legacy VPNs with a Zero Trust Architecture that provides access to only approved applications instead of the entire enterprise network. In addition, with security delivered in the cloud there is no need to backhaul SaaS traffic through the VPN which substantially increases connection speeds and productivity.
Benefit
Direct and secure connections to SaaS applications with controlled access to private applications and data improves security, improves productivity, improves the end-user experience, and substantially reduces costs.
Challenge
Finance, HR, and other departments need to open high volumes of emails with random attachments from unknown senders which are highly likely to be malware or ransomware
Solution
The iboss Zero Trust Secure Access Service Edge includes Browser Isolation which is 100% compatible with the Microsoft Outlook Web Client. HR, Finance, Support and other departments can access email through a browser-based isolated session which opens emails and attachments remotely and through a pane-of-glass so that the data contained within the email or attachments never touches sensitive computers and devices.
Benefit
Prevent malware and ransomware attacks and substantially reduce risk from risky email and attachments.
Challenge
Remote users need access to onsite applications, data, and services but need to turn on a VPN for access to be granted.
Solution
The iboss Zero Trust Secure Access Service Edge offers secure access to onsite resources with no end-user intervention, eliminating the need for users to manually switch on a VPN.
Benefit
The iboss Zero Trust SASE offers organizations enhanced security and a better user experience.
Challenge
Enterprise security teams need visibility and logging of all resource accesses to ensure compliance and prevent data loss.
Solution
The iboss Zero Trust Secure Access Service Edge provides always-on logging and visibility of all resource accesses, including access to SaaS and onsite applications and services. Only access to approved applications and data is granted, while providing per-request access decisions, continuous adaptive access, and logging for every interaction. This includes generating log events after login so that no interaction between a user and resource is missed.
Benefit
The iboss Zero Trust SASE substantially reduces risk by capturing each and every interaction between users and sensitive resources. Log events can also be forwarded to any external SIEM or SOC.
Challenge
Call center agents interact with sensitive third-party data and attachments through ServiceNow and Zendesk where risk of data leakage or infected attachments is high.
Solution
The iboss Zero Trust Secure Access Service Edge provides Browser Isolation which allows Call Center agents to work through a pane-of-glass via their web browser which keeps data isolated and off their machines. This ensures data remains compliant and secure by keeping the data remote. This also ensures unknown attachments are never opened locally to eliminate the risk of malware and ransomware infection.
Benefit
Reduce the risk of data loss and malware breaches while ensuring GDPR and other compliance is met while Call Center agents work with third-party data.
Replace Outdated VPNs
Provide Isolated Access to Email & Attachments
Provide Secure Remote Access Without VPN
Gain Continuous Visibility and Logging
Provide Call Center Agents Access To Risky Third-Party Data
Use Cases
Replace Legacy Proxy Appliances
Legacy network security proxy appliances are overloaded, causing latency and downtime due to increased traffic loads, struggle to keep up with HTTPS decryption, require costly renewals, and are approaching end-of-life hardware resulting in large hardware refresh projects.
Solution
Replace Proxies with iboss Zero Trust SASE. The iboss Zero Trust Secure Access Service Edge can be quickly implemented to replace legacy proxies and reduce costs through predictable per-user licensing and infinite security at scale delivered in the cloud.
Benefit
Substantial immediate cost savings with a sustainable long-term security strategy that can handle any volume of users and network traffic for better security, visibility, improved productivity, and the best end-user experience.
Enable Secure App & Data Access for Remote Workers
As more organizations shift to remote work, secure access to apps and data is a growing challenge. Without the right security measures, companies can give remote workers access to the entire enterprise network, leading to data loss and breaches.
Solution
The iboss Zero Trust Secure Access Service Edge provides secure access to sensitive resources without granting access to the entire private network. ZTNA runs in the background so users can connect to the resources they need without turning on a VPN, and it’s more secure as it allows remote workers to access only the applications they are authorized to use.
Benefit
iboss ZTNA helps organizations reduce the risk of data loss and breaches by ensuring remote users only have access to authorized applications and data.
Provide Application Access for BYOD, Contractors, and Third-Parties
Enterprises need the ability to securely give contractors and third parties access to sensitive applications, data, and services without risking data loss due to access from unmanaged devices.
Solution
The iboss Zero Trust Secure Access Service Edge offers a secure solution that allows users to access the resources they need without compromising security. Built-in Browser Isolation technology keeps data safe by granting access to services, data and applications through a VDI-like pane of glass that prevents data from touching unmanaged and third-party devices. Browser Isolation is agentless and eliminates the need to install temporary VPNs on third-party devices.
Benefit
Securely provide access to sensitive resources from unmanaged BYOD, contractor and third-party devices without the high cost of traditional VDI solutions with iboss Zero Trust SASE’s Browser Isolation technology which substantially reduces risks, costs and complexity.
Improve Connection Speeds to Microsoft O365 & Teams
Organizations using Microsoft O365 are facing performance issues due to forcing Microsoft O365 and Teams connections through slow VPNs and overloaded legacy proxy appliances hosted in a datacenter.
Solution
The iboss Zero Trust Secure Access Service Edge provides direct connections to Microsoft O365 and Teams without sending traffic through a VPN or backhauling traffic through the datacenter. The iboss Zero Trust SASE provides Microsoft Tenant Restrictions, logging and security in the cloud and at scale to support any number of users with ultra-fast and direct connections to Microsoft O365 and Teams.
Benefit
Direct and secure connections to Microsoft through the iboss Zero Trust SASE improves user productivity, improves the end-user experience, improves simplicity, and substantially reduces costs.
Reduce or Eliminate Data Center Space
Organizations need to reduce or eliminate data center space to eliminate costs but VPN concentrators, Proxy appliances, and VDI infrastructure are currently hosted within those facilities.
Solution
With iboss Zero Trust SASE, all of the capabilities provided by VPN, proxy security appliances and VDI infrastructure are transitioned to the cloud and converted to a cloud service. In addition to eliminating datacenter infrastructure, ZTNA, Secure Access Service Edge, and Browser Isolation provides better security and scalability than the legacy approach provided with on-premises infrastructure.
Benefit
Eliminate or reduce data center space while significantly reducing costs. The iboss Zero Trust SASE will provide security to all users, IoT, and OT at scale for improved security, performance, and lower costs.
Replace Outdated VPNs
Legacy VPNs are overloaded and insecure while they provide access to sensitive resources for remote users.
Solution
The iboss Zero Trust Secure Access Service Edge provides a quick and easy replacement of legacy VPNs with a Zero Trust Architecture that provides access to only approved applications instead of the entire enterprise network. In addition, with security delivered in the cloud there is no need to backhaul SaaS traffic through the VPN which substantially increases connection speeds and productivity.
Benefit
Direct and secure connections to SaaS applications with controlled access to private applications and data improves security, improves productivity, improves the end-user experience, and substantially reduces costs.
Provide Isolated Access to Email & Attachments
Finance, HR, and other departments need to open high volumes of emails with random attachments from unknown senders which are highly likely to be malware or ransomware
Solution
The iboss Zero Trust Secure Access Service Edge includes Browser Isolation which is 100% compatible with the Microsoft Outlook Web Client. HR, Finance, Support and other departments can access email through a browser-based isolated session which opens emails and attachments remotely and through a pane-of-glass so that the data contained within the email or attachments never touches sensitive computers and devices.
Benefit
Prevent malware and ransomware attacks and substantially reduce risk from risky email and attachments.
Provide Secure Remote Access Without VPN
Remote users need access to onsite applications, data, and services but need to turn on a VPN for access to be granted.
Solution
The iboss Zero Trust Secure Access Service Edge offers secure access to onsite resources with no end-user intervention, eliminating the need for users to manually switch on a VPN.
Benefit
The iboss Zero Trust SASE offers organizations enhanced security and a better user experience.
Gain Continuous Visibility and Logging
Enterprise security teams need visibility and logging of all resource accesses to ensure compliance and prevent data loss.
Solution
The iboss Zero Trust Secure Access Service Edge provides always-on logging and visibility of all resource accesses, including access to SaaS and onsite applications and services. Only access to approved applications and data is granted, while providing per-request access decisions, continuous adaptive access, and logging for every interaction. This includes generating log events after login so that no interaction between a user and resource is missed.
Benefit
The iboss Zero Trust SASE substantially reduces risk by capturing each and every interaction between users and sensitive resources. Log events can also be forwarded to any external SIEM or SOC.
Provide Call Center Agents Access To Risky Third-Party Data
Call center agents interact with sensitive third-party data and attachments through ServiceNow and Zendesk where risk of data leakage or infected attachments is high.
Solution
The iboss Zero Trust Secure Access Service Edge provides Browser Isolation which allows Call Center agents to work through a pane-of-glass via their web browser which keeps data isolated and off their machines. This ensures data remains compliant and secure by keeping the data remote. This also ensures unknown attachments are never opened locally to eliminate the risk of malware and ransomware infection.
Benefit
Reduce the risk of data loss and malware breaches while ensuring GDPR and other compliance is met while Call Center agents work with third-party data.
Trusted by Organizations Worldwide
ADP
Verizon
Comcast
GPC
ABB
Eastman Chemical
SMUD
FIS
Christus Health
Citrix
Trusted by Organizations Worldwide
ADP
Verizon
Comcast
GPC
ABB
Eastman Chemical
SMUD
FIS
Christus Health

“Easy To Use and Manage, Specifically For Our Complex Network. Really enjoy the functionality and features within iboss. This tool gives us a lot of visibility and we have found it to be very easy to manage policies and our complex network, easily.”

“Excellent partners, willing to provide expertise to maximize our investment, which continued as we moved from sales to operations. A SaaS platform is a significant change for us. iboss helped answer critical decisions based on their experience.”

“iboss truly enhanced our journey to the cloud. The implementation and configuration was seamless; any issue was promptly resolved through our dedicated implementation relationships.”

“We transitioned from another cloud gateway to iboss because of its capabilities and hybrid ‘local cloud’ platform. Overall, it was a seamless transition and has been very successful with far more functionality. The iboss staff are very engaged.”

“The iboss Cloud Platform was light years ahead of what we were using in terms of security functionality. The price factor was also important. When it came to iboss versus the other solutions we considered, iboss was a lot more affordable.”
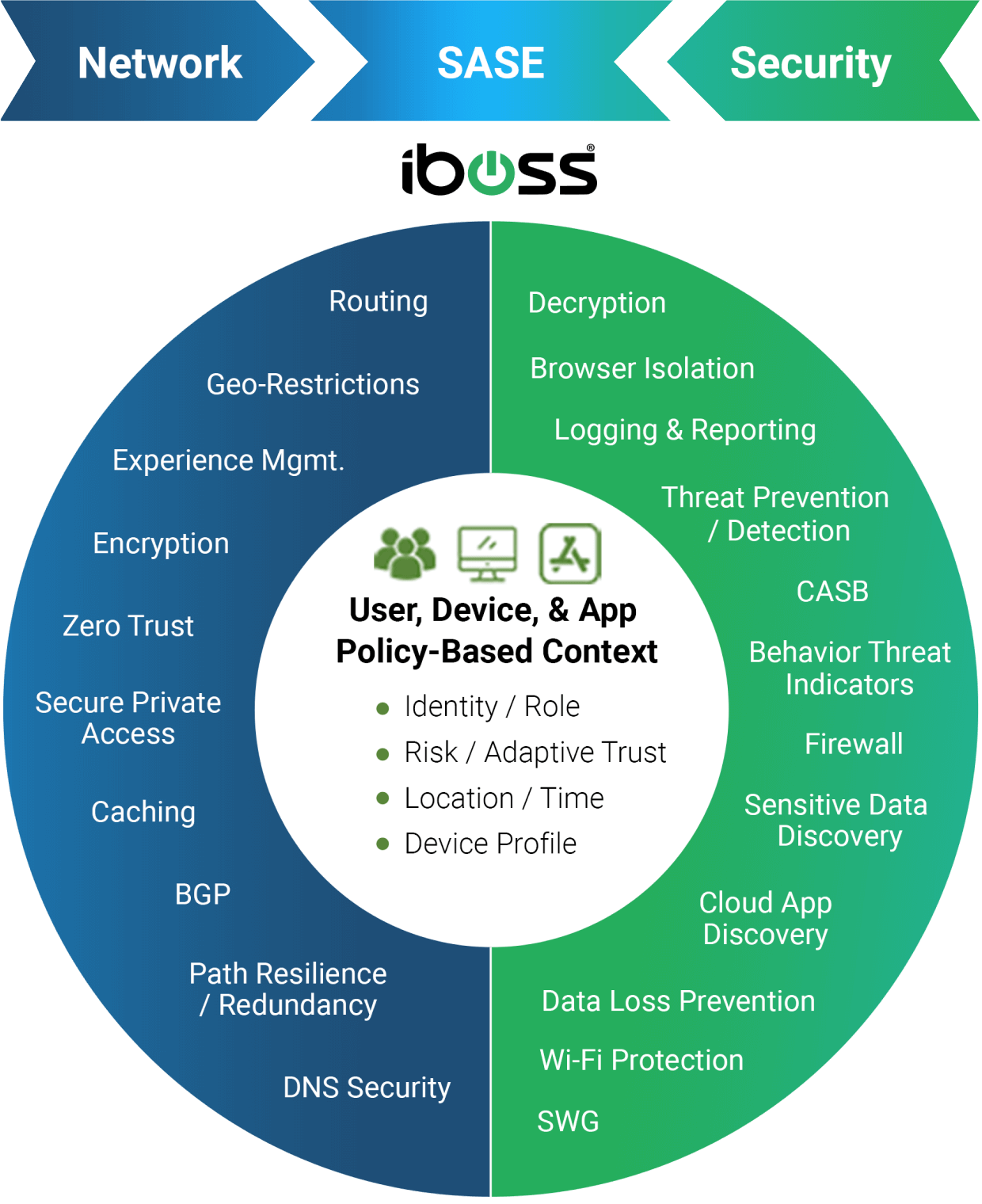
Key Capabilities
Replace legacy proxies
Replace legacy proxies with a cloud-based solution for reduced costs and infinite security at scale.
Secure access to resources
Secure access to sensitive resources without granting access to the entire private network.
Reduce the risk of data loss
Reduce the risk of data loss and breaches with secure access to only authorized applications and data.
Access to resources from unmanaged devices
Securely provide access to authorized resources from unmanaged devices without high cost of VDI solutions.
Transition VPN, Proxy, and VDI
Reduce or eliminate data center space and transition VPN, Proxy, and VDI appliances to the cloud.
Quickly replace legacy VPNs
Quickly replace legacy VPNs for improved security and better end user experience – Improved end-user experience and increased productivity when leveraging Microsoft O365.
Automatic secure access
Secure access with no end-user intervention, eliminating the need for manual VPN activation.
Always-on security
Always-on security, logging and visibility of all resource accesses, including SaaS and onsite applications and services.
Secure Connections Everywhere
Direct and secure connections from wherever employees work with full visibility and logging, allowing for lightning-fast access to Microsoft O365 for improved productivity.
Zero Trust Architecture
Zero Trust Architecture based on the NIST 800-207 for better security and compliance.
Replace Legacy Technology With a Consolidated Cloud Security Platform
ZTNA
Virtual private network was used to connect users to onsite applications, services and data.
LEARN MORESASE
Appliances & Proxies
Was used to apply security for malware defense and data loss to users connecting to the Internet from the office.
LEARN MOREBROWSER
ISOLATION
Virtual Desktop Infrastructure was used to connect users to high-risk applications through a “pane of glass” so that data from those applications could not touch end user devices
LEARN MOREOld Way
VPN
New Way
ZTNA
- Users must know to turn VPN on when remote to access onsite resources
- Only connections to office are encrypted by VPN
- DNS queries from devices to resolve domain names are sent to the local network unencrypted
- Only data running through the office via VPN is secured for breaches and data loss
- Users have access to all office resources when VPN is enabled
ZTNA
With the iboss Zero Trust SASE, you can replace legacy VPNs with ZTNA, which provides a more secure way to connect remote users to onsite resources. Unlike VPNs, ZTNA only allows users access to the specific resources they are authorized to access, which reduces the risk of breaches and data loss.
- Users are always connected to iboss Zero Trust SASE and never “enable” a VPN. They are always connected to onsite resources
- All traffic from the device is encrypted, including connections to the office and the public Internet
- DNS queries from devices are always encrypted and sent to the iboss Zero Trust SASE
- ALL data is sent through the iboss Zero Trust SASE and secured for breaches and data loss regardless of user location
- Users only have access to specific applications which is provided automatically
Old Way
Proxy
New Way
SASE
- Only inspect and secure connections with malware defense, compliance policies and data loss prevention for users in office
- Only generates log events for traffic from onsite users and devices
- Require VPNs to backhaul traffic from remote users to apply security with on-prem security proxies
- Appliances overloaded when SSL decryption is enabled to inspect content within HTTPS connections
- Require hardware refreshes every 3-5 years which is expensive and time consuming
SASE
The iboss Zero Trust SASE can replace legacy proxy appliances with Secure Access Service Edge, which provides direct connections to all applications and services, without appliances. This eliminates the worry of overloaded appliances, which can occur due to the increased load from video conferencing, Microsoft O365, and other services.
- Secures all connections with malware defense, compliance policies and data loss prevention for users anywhere as users are always connected to iboss Zero Trust SASE
- Generates log events for users and devices located anywhere as users are always connected to iboss Zero Trust SASE
- Traffic from remote users goes directly to destination without sending the traffic through the office as users are connected directly through iboss Zero Trust SASE
- Can decrypt an infinite amount of HTTPS traffic within the iboss Zero Trust SASE
- Security and capabilities always up to date as iboss Zero Trust SASE is a cloud service eliminating hardware refreshes
Old Way
VDI
New Way
BROWSER ISOLATION
- Requires expensive VDI infrastructure to provide access to applications through a “pane of glass” for high-risk apps
- Must deploy VDI to high-cost regions to support call centers needing access to highly sensitive applications
- VDI must be connected to proxy appliances to apply security policies to connections
- VDI must be connected to proxies for logging of connections and transactions
- VDI has limited abilities for controlling uploads and downloads as well as other in-app policies
BROWSER ISOLATION
Browser Isolation provides a VDI-like interface that separates high-risk data from risky users and devices. It is delivered through the end user’s browser, instantly, without infrastructure, from the iboss Zero Trust SASE service. It gets the benefits of ZTNA, allowing those users to connect to private resources. It also gets the benefits of the security service which includes malware defense, compliance policies, CASB, and logging.
- iboss Zero Trust SASE provides a pane of glass using Browser Isolation which runs within the iboss Zero Trust SASE
- Browser Isolation is available everywhere globally without the need to deploy VDI infrastructure in high-cost regions
- Browser Isolation runs connections through the Secure Access Service Edge policies and security automatically
- Browser Isolated connections run through the iboss Zero Trust SASE which automatically generates log events for all transactions
- Browser Isolation provides policy and security controls that include CASB as well as file upload and download controls
Replace Legacy Technology With a Consolidated Cloud Security Platform
ZTNA
Virtual private network was used to connect users to onsite applications, services and data.
LEARN MOREWith the iboss Zero Trust SASE, you can replace legacy VPNs with ZTNA, which provides a more secure way to connect remote users to onsite resources. Unlike VPNs, ZTNA only allows users access to the specific resources they are authorized to access, which reduces the risk of breaches and data loss.
Old Way
VPN
New Way
ZTNA
- Users must know to turn VPN on when remote to access onsite resources
- Users are always connected to iboss Zero Trust SASE and never “enable” a VPN. They are always connected to onsite resources
- Only connections to office are encrypted by VPN
- All traffic from the device is encrypted, including connections to the office and the public Internet
- DNS queries from devices to resolve domain names are sent to the local network unencrypted
- DNS queries from devices are always encrypted and sent to the iboss Zero Trust SASE
- Only data running through the office via VPN is secured for breaches and data loss
- ALL data is sent through the iboss Zero Trust SASE and secured for breaches and data loss regardless of user location
- Users have access to all office resources when VPN is enabled
- Users only have access to specific applications which is provided automatically
SECURE ACCESS SERVICE EDGE
Was used to apply security for malware defense and data loss to users connecting to the Internet from the office.
LEARN MOREThe iboss Zero Trust SASE can replace legacy proxy appliances with Security Service Edge, which provides direct connections to all applications and services, without appliances. This eliminates the worry of overloaded appliances, which can occur due to the increased load from video conferencing, Microsoft O365, and other services.
Old Way
PROXY
New Way
SASE
- Only inspect and secure connections with malware defense, compliance policies and data loss prevention for users in office
- Secures all connections with malware defense, compliance policies and data loss prevention for users anywhere as users are always connected to iboss Zero Trust SASE
- Only generates log events for traffic from onsite users and devices
- Generates log events for users and devices located anywhere as users are always connected to iboss Zero Trust SASE
- Require VPNs to backhaul traffic from remote users to apply security with on-prem security proxies
- Traffic from remote users goes directly to destination without sending the traffic through the office as users are connected directly through iboss Zero Trust SASE
- Appliances overloaded when SSL decryption is enabled to inspect content within HTTPS connections
- Can decrypt an infinite amount of HTTPS traffic within the iboss Zero Trust SASE
- Require hardware refreshes every 3-5 years which is expensive and time consuming
- Security and capabilities always up to date as iboss Zero Trust SASE is a cloud service eliminating hardware refreshes
BROWSER
ISOLATION
Virtual Desktop Infrastructure was used to connect users to high-risk applications through a “pane of glass” so that data from those applications could not touch end user devices
LEARN MOREBrowser Isolation provides a VDI-like interface that separates high-risk data from risky users and devices. It is delivered through the end user’s browser, instantly, without infrastructure, from the iboss Zero Trust SASE service. It gets the benefits of ZTNA, allowing those users to connect to private resources. It also gets the benefits of the security service which includes malware defense, compliance policies, CASB, and logging.
Old Way
VDI
New Way
BROWSER ISOLATION
- Requires expensive VDI infrastructure to provide access to applications through a “pane of glass” for high-risk apps
- iboss Zero Trust SASE provides a pane of glass using Browser Isolation which runs within the iboss Zero Trust SASE
- Must deploy VDI to high-cost regions to support call centers needing access to highly sensitive applications
- Browser Isolation is available everywhere globally without the need to deploy VDI infrastructure in high-cost regions
- VDI must be connected to proxy appliances to apply security policies to connections
- Browser Isolation runs connections through the Secure Access Service Edge policies and security automatically
- VDI must be connected to proxies for logging of connections and transactions
- Browser Isolated connections run through the iboss Zero Trust SASE which automatically generates log events for all transactions
- VDI has limited abilities for controlling uploads and downloads as well as other in-app policies
- Browser Isolation provides policy and security controls that include CASB as well as file upload and download controls
Replace Blue Coat with iboss
The Best Broadcom Blue Coat Replacement
Combine iboss With Any Identity Provider
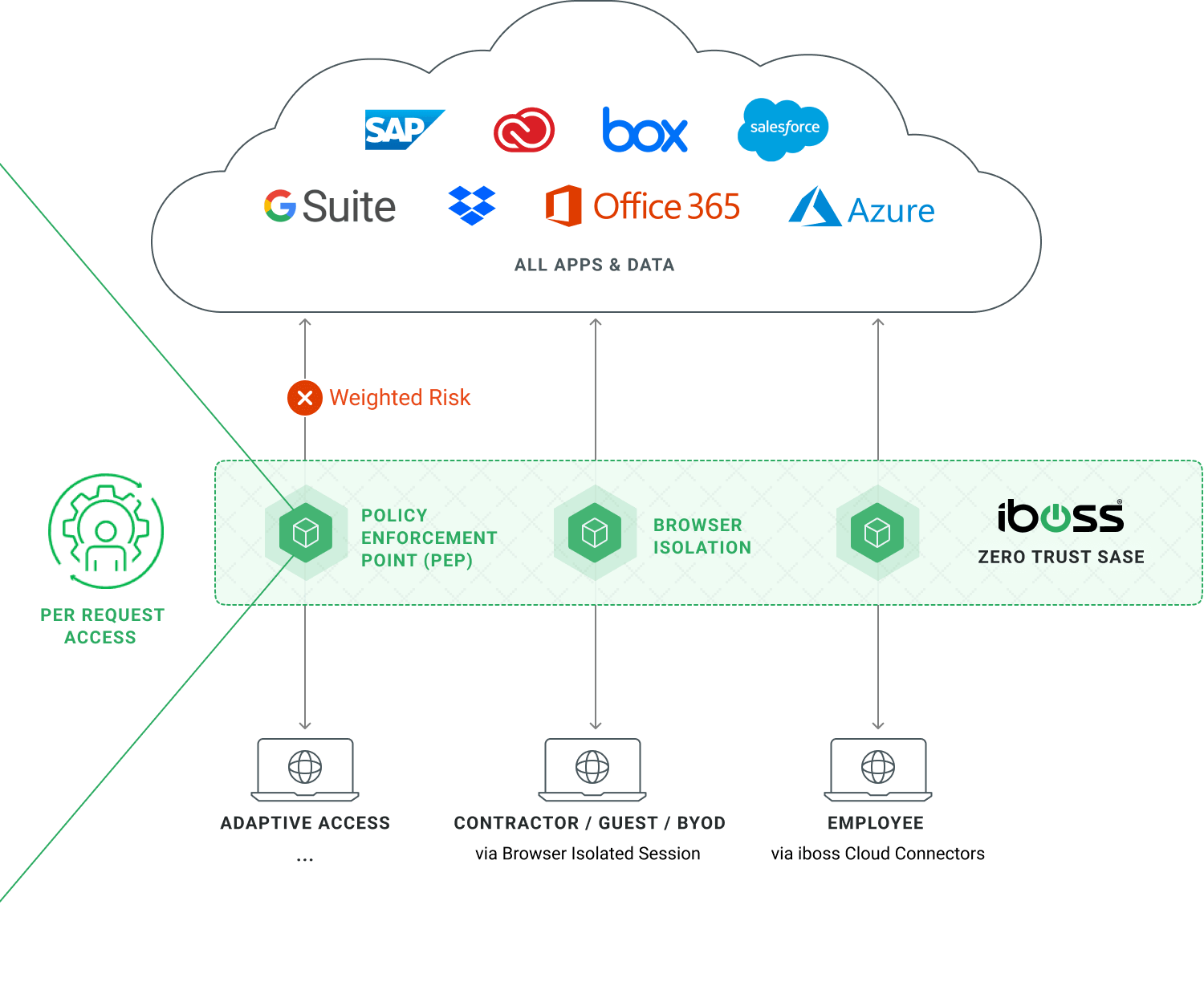
Extend Conditional Adaptive Access Beyond Login so That it Applies Continuously for Every Request
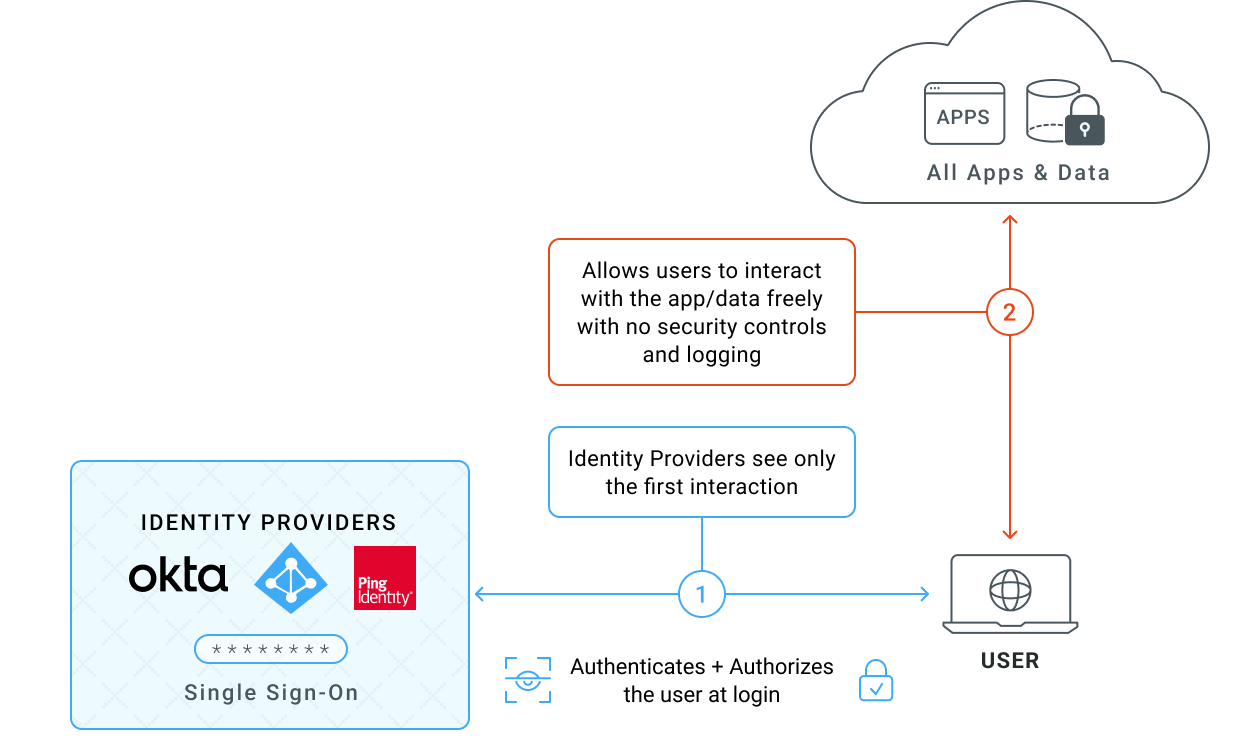
WITHOUT IBOSS
Identity Providers only authenticate and authorize when a user logs in. In addition, adaptive access decisions only occur during the login process as users interact with the IdP. This leaves the vast number of interactions between users and applications completely unprotected and results in security teams being blind to the most important interactions that occur after login.
For example, if a user has their session stolen, that session can be used by an attacker to interact freely with the protected application and data because there are no additional checks that occur after login. If a device becomes infected with ransomware, the data is vulnerable to being crypto-locked freely as there is no way to cutoff access immediately after infection. If data hijacking occurs, there is no way to prevent or see it because users have free interaction with data, applications and services after login.
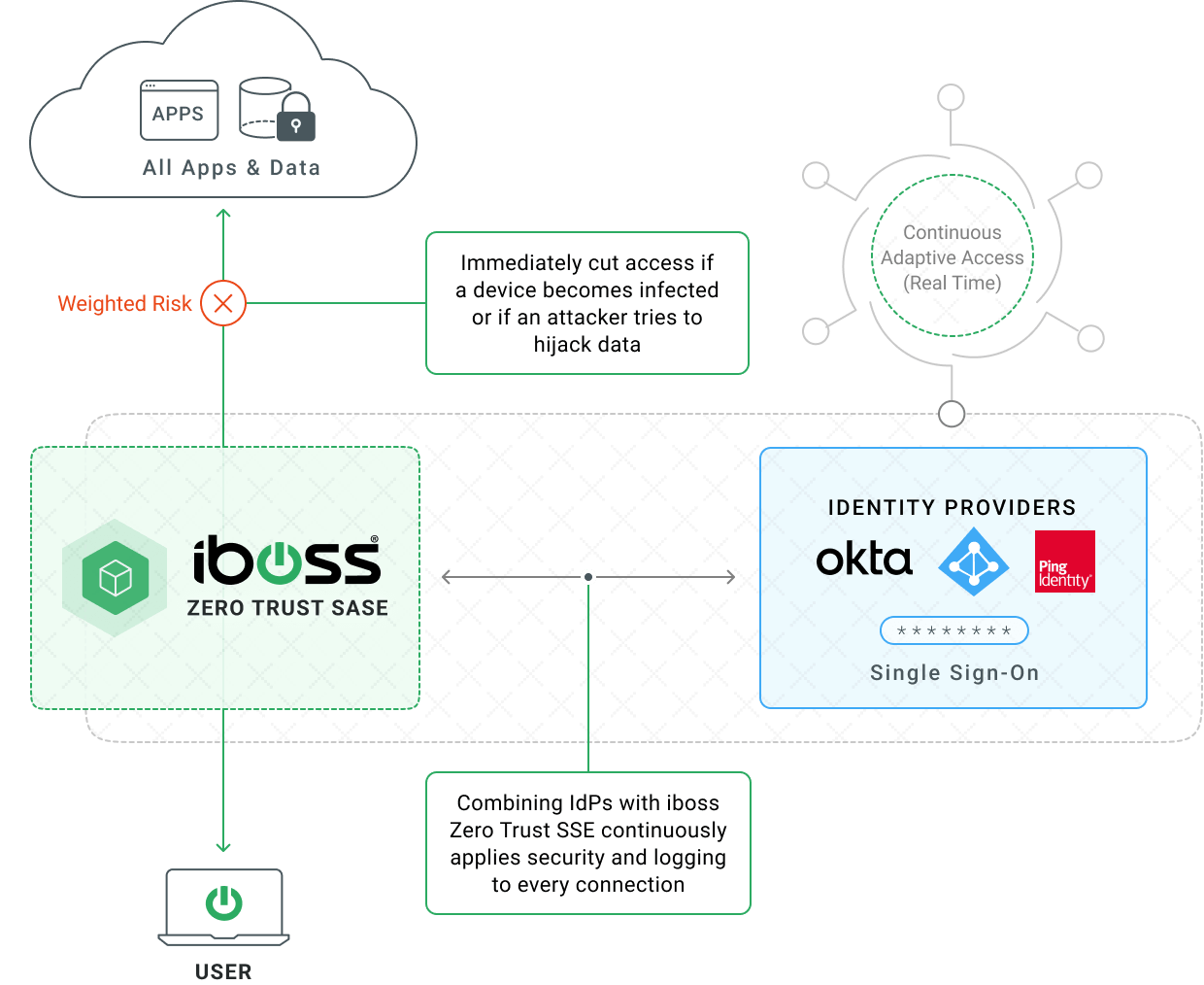
WITH IBOSS
By combining an Identity Provider with the iboss Zero Trust SASE, adaptive access is extended so that every single interaction between a user and an application is inspected and runs through adaptive access decisions. This is because there is no way for the user to interact with data, applications and services without traversing the iboss Zero Trust SASE which is able to apply adaptive access decisions continuously and in real-time.
For example, if a user session is stolen and an attacker attempts to use that session in a remote region, the iboss Zero Trust SASE will prevent access even though the session might still be valid because it can determine that the login location does not match the access location. If a device becomes infected with ransomware, the iboss Zero Trust SASE can cut access to all sensitive applications and data immediately, without waiting for the login session to expire. If data hijacking is attempted, the iboss Zero Trust SASE can cut access immediately as iboss is able to see and control all data transfers in real-time and apply continuous adaptive access and controls after login.
iboss’ Zero Trust Secure Access Service Edge
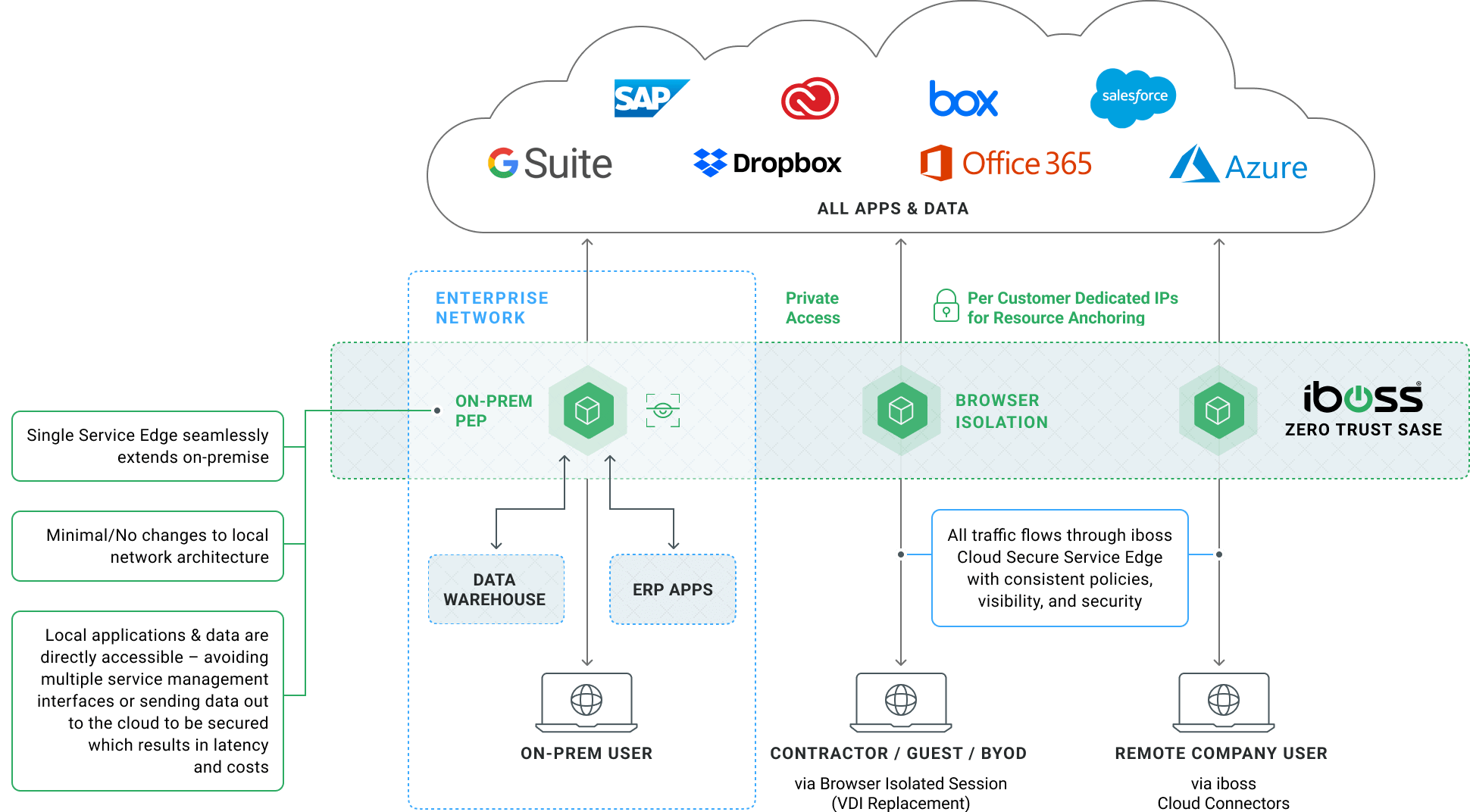
A Single Unified Edge – Eliminating VPNs, VDIs, & Legacy On-Prem Proxies
A Single Unified Edge – Eliminating VPNs, VDIs, & Legacy On-Prem Proxies
The iboss Zero Trust SASE provides a secure and easy way to connect remote users to on-prem and cloud applications. The platform uses ZTNA to provide secure access to remote users, only allowing users access to the specific resources they are authorized to access. This is more secure than a VPN, which allows remote users access to the entire enterprise network, which could lead to an increased risk of breaches and data loss.
The iboss Zero Trust SASE also replaces legacy proxy appliances with Secure Access Service Edge, which provides direct connections to all applications and services, without appliances. This eliminates the worry of overloaded appliances due to the increased load from video conferencing and other services.
The iboss Zero Trust SASE eliminates and improves on the capabilities provided by VDI by providing isolated access to sensitive resources through a pane-of-glass delivered through the end-user’s browser. And because it’s part of a unified platform, Browser Isolation benefits from the capabilities of ZTNA and Secure Access Service Edge to provide access to private applications while applying security and logging to every request automatically.
Continuous Adaptive Access: Essential for Zero Trust
Ensures EVERY interaction between a user and data is authorized
to immediately cut access when a device gets infected
or a high risk user is detected
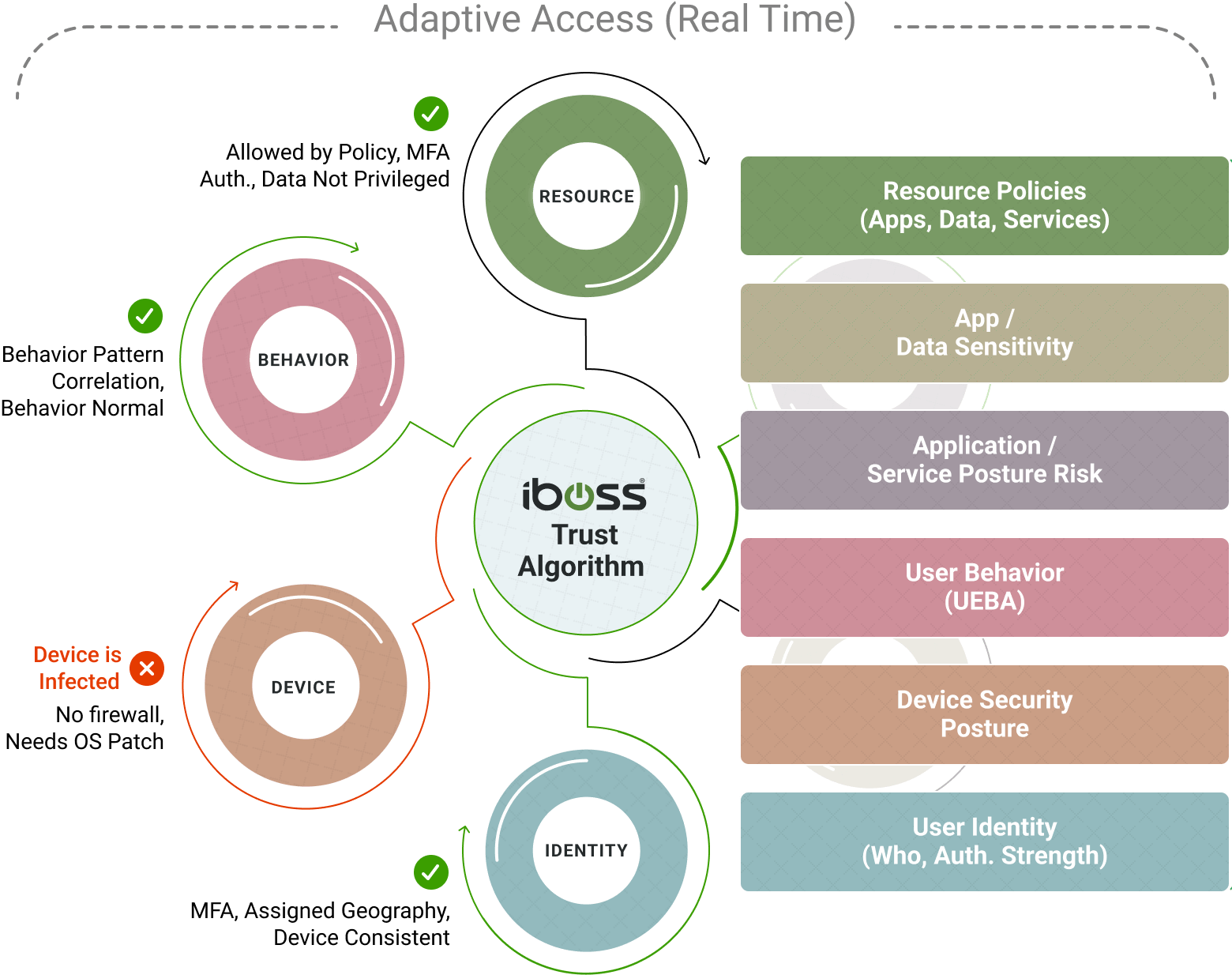
Continuous Adaptive Access: Essential for Zero Trust
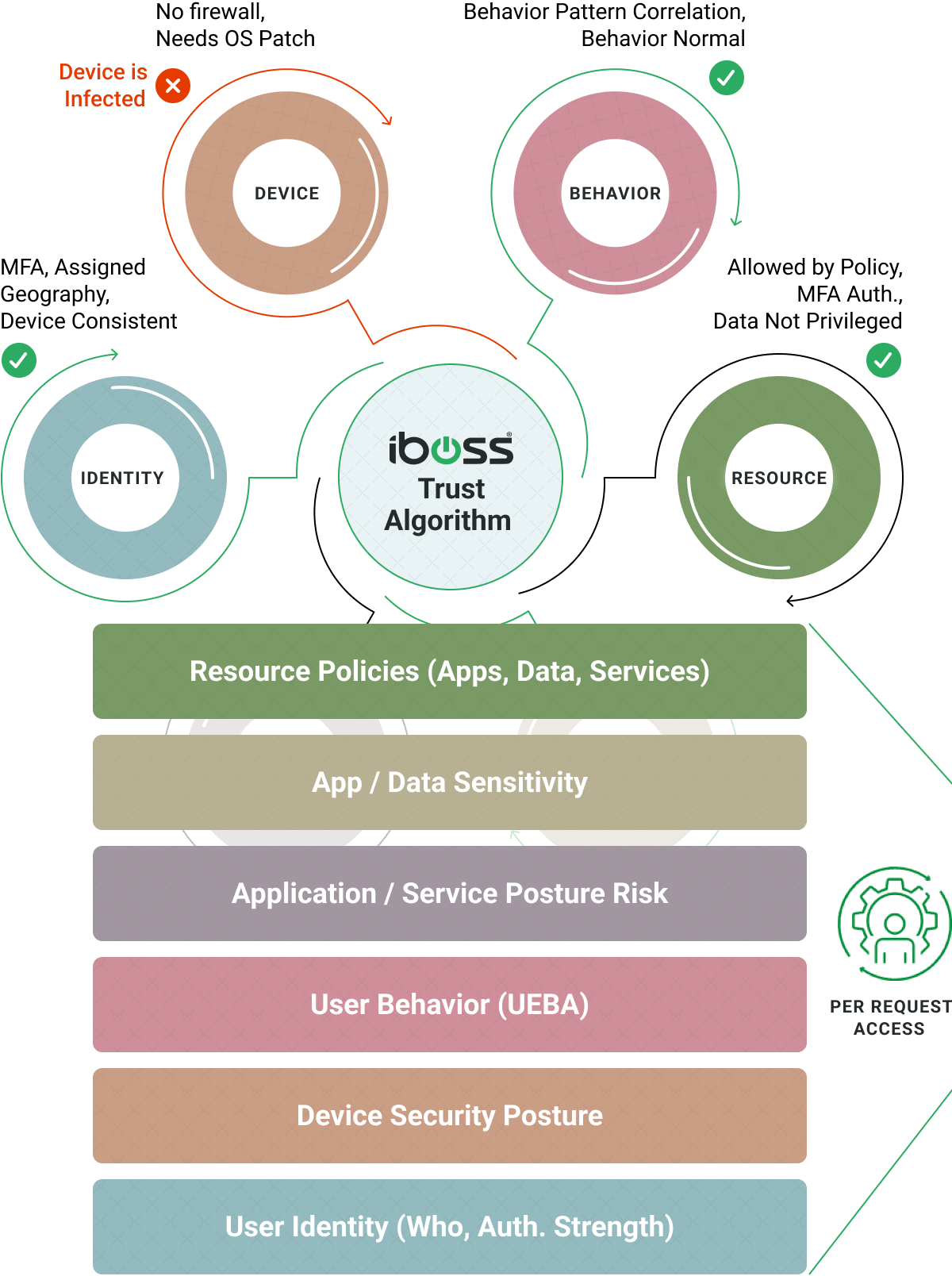
Ensures EVERY interaction between a user and data is authorized to immediately cut access when a device gets infected or a high risk user is detected
The NIST 800-207 Zero Trust Architecture Publication outlines Trust Algorithms which are needed to increase decision confidence when the Zero Trust service grants or denies access to a protected resource. The iboss platform provides criteria-based and score-based algorithms to ensure the Policy Enforcement Points make adaptive and intelligent decisions when granting or denying access to protected resources.
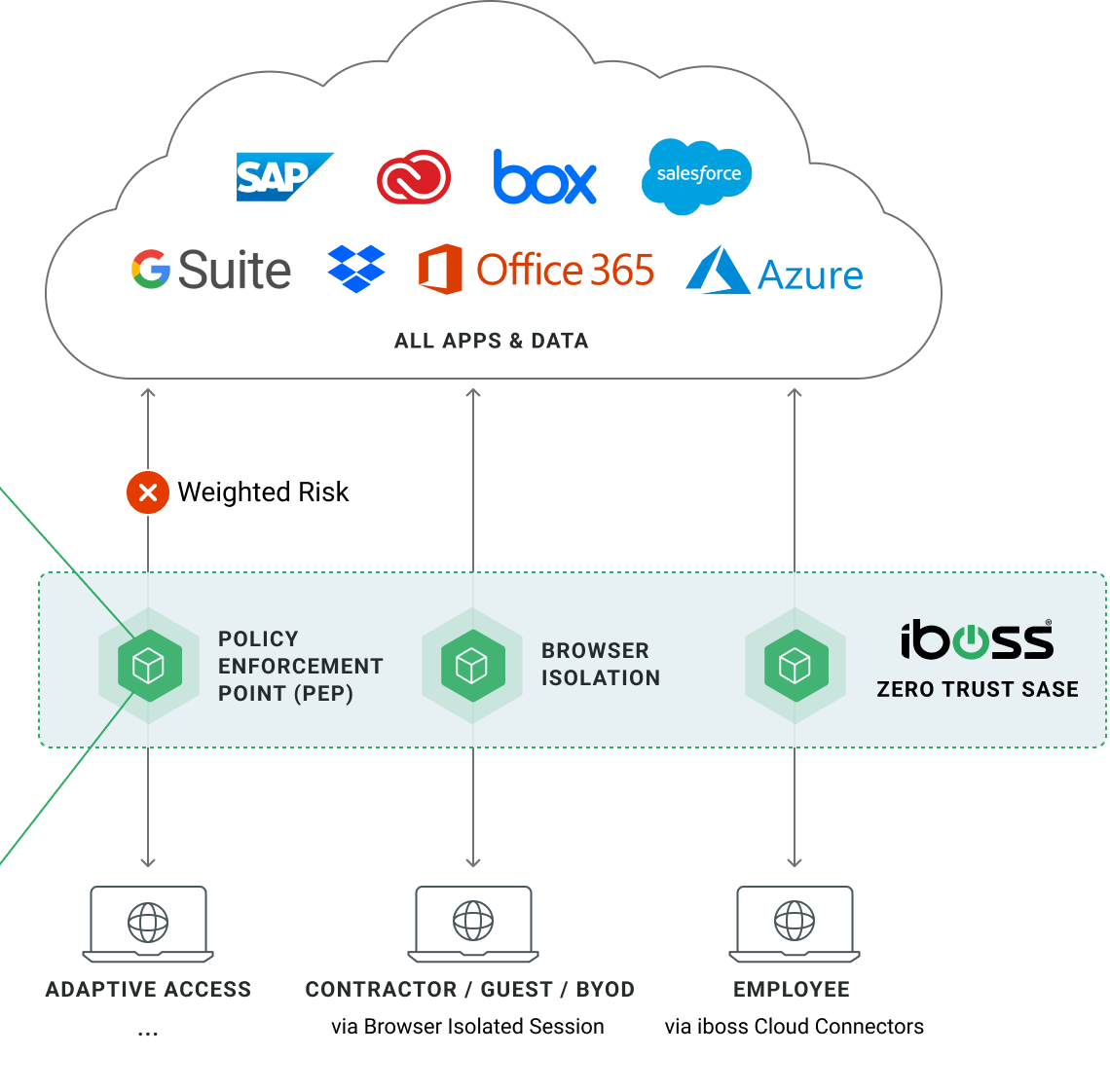
Provide Contractors, 3rd Parties & BYOD Secure Access to Resources with Browser Isolation
Provide Contractors, 3rd Parties & BYOD Secure Access to Resources with Browser Isolation
Zero Trust Browser Isolation prevents sensitive data leaks to unmanaged devices and protects users from threats when accessing high-risk data and applications
The iboss Zero Trust SASE also includes Browser Isolation, which provides a VDI-like interface that separates high-risk data from risky users and devices. It is delivered through the end user’s browser, instantly, without infrastructure, from the iboss Zero Trust SASE service. It also gets the benefits of ZTNA and the security service, which includes malware defense, compliance policies, CASB, and logging.
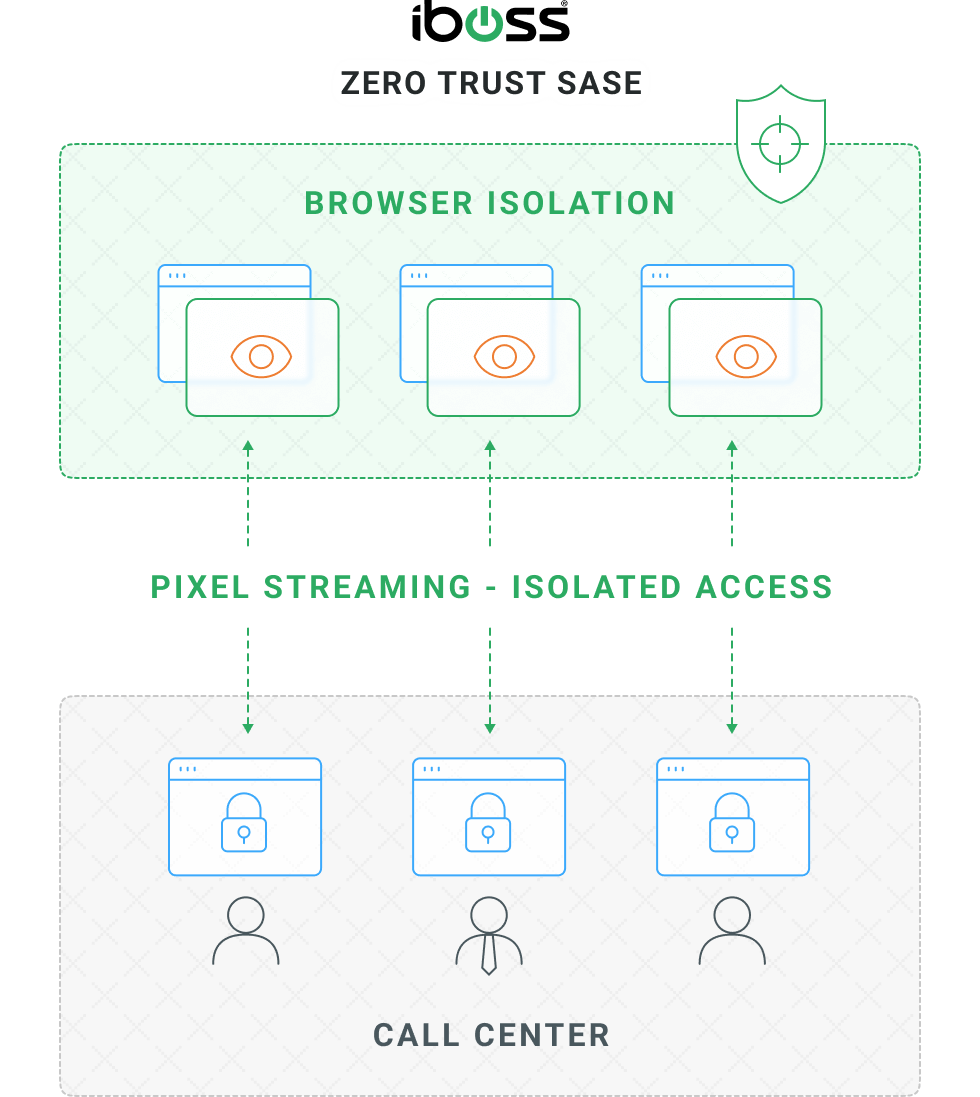
The iboss Zero Trust SASE Combines Zero Trust + Secure Access Service Edge
iboss Provides Connectivity and Advanced Security Capabilities for Compliance, Malware Defense and Data Loss Prevention
Ultimately, the iboss Zero Trust SASE provides a secure connection to remote users, an increased level of security, and cost savings by consolidating security point products into a single SaaS security service.
Pricing
Solution Packages to support your Journey to a Zero Trust Architecture
Simple per User Subscription Pricing
Delivering Lower Costs and Better Results.
The iboss Cloud Platform gives you unprecendented business value and a better return on investment, faster than most. The numbers speak for themselves.
Return on Investment
Get a 275% return on your investment across three years.
Lower Operations Cost
iboss lowers your three-year cost of operations by 37%, on average.
More Efficient Teams
Increasingly efficient IT security teams means more time to focus.
Reduced Security Risk
Lower the risk of security events by bridging your NetOps & SecOps.
More Control and Capability. Less Complexity.
Secure connectivity from anywhere, delivered directly in the cloud. We are the leading Zero Trust SASE Platform connecting users to any app, from anywhere.
Awards & Recognition
iboss has been awarded Gold for Employer of the Year- Cybersecurity Products or Services by the Globee Business Awards
iboss’ Paul Martini has been awarded Cybersecurity Company CEO of the Year by the Cybersecurity Breakthrough Awards
iboss has been awarded Gold for Security Solution for Large Enterprise Innovation by the Globee Golden Bridge Awards
iboss has been awarded Gold for Security Solution for Government Innovation by the Globee Golden Bridge Awards
iboss CEO, Paul Martini has been awarded Gold for CEO of the Year – Cybersecurity Products or Services by the Globee Leadership Awards
iboss has been awarded Best Zero Trust Solution by Cyber Defense Magazine Global InfoSec Awards
Unrivaled Global Cloud Security Edge
A containerized architecture built for infinite scalability. iboss created and operates one of the largest global cloud network security fabrics on earth. A scalable global service ensures zero trust network security and peace of mind, regardless of where users work.
150B+ Transactions Daily
The iboss Cloud Platform secures 150B+ transactions per day.
4B+ Threats Prevented Daily
On average, we are preventing over 4B+ security threats per day.
100+ Global POPs
One of the largest SASE platforms with over 100+ Points of Presence.
150+ Countries Connected
Places access closer to users giving faster secure connections anywhere.
Solution Briefs
Replace legacy VPN, Proxy, and VDI with ZTNA, Secure Access Service Edge, and Browser Isolation with a Single Platform
VIEW SOLUTION BRIEFThe iboss Zero Trust SASE replaces VPN with ZTNA to improve security and reduce costs
VIEW SOLUTION BRIEFThe iboss Zero Trust SASE replaces onsite proxy appliances to improve security and reduce costs
VIEW SOLUTION BRIEFThe iboss Zero Trust SASE replaces VDI with Browser Isolation to improve security and reduce costs
VIEW SOLUTION BRIEFContact Us
Contact Us
If you’d like to speak to a sales representative, please take a moment to complete the form and an iboss representative will contact you shortly.
To speak with an iboss representative now, please call:
North America:
+1-877-742-6832 ext. 1
UK & Ireland:
Non UK International:
+1-858-568-7051 ext. 1
LATAM:
+1- 877-742-6832 ext. 7424