Prevent damage from ransomware by automatically cutting access to resources when devices become infected
Download this Solution Brief Download PDF
CHALLENGES
Long after a device becomes infected, ransomware continues to damage and encrypt sensitive data due to a lack of human resources that can respond to infections quickly. Attackers continue to hijack sensitive data for ransom as they gain access to unauthorized resources without being noticed. With sensitive applications, services, and data scattered across SaaS, cloud infrastructure, and onsite environments causing an increase in attack surface area, it is becoming more challenging to protect valuable assets from breaches and data loss.
Meanwhile, providing remote users access to apps and data from secure devices is critical for reducing risk and meeting compliance, but it can be difficult to automatically take action and cut access to sensitive resources if a device becomes infected or does not meet compliance requirements. For example, security teams may have a lack of visibility and control to ensure the firewall is on, the disk is encrypted, and the device’s endpoint protection solution is configured correctly.
PAIN POINT
Infected Devices Damage Data
When devices are detected to be infected by CrowdStrike, access to sensitive applications and data must be terminated.
iboss SOLUTION
Automatically Cut Access When Infections Occur
The iboss Zero Trust SASE can automatically terminate access based on CrowdStrike incidents that have high-risk CrowdScores.
KEY BENEFITS
Automatically cut off access to sensitive enterprise resources when a device becomes infected or an incident risk is high based on the CrowdStrike CrowdScore incident rating
Apply CASB, malware defense, compliance policies, and DLP to every transaction to complement Falcon’s on-device protections
Automatically cut off or isolate access when the Falcon ZTA risk score indicates high risk
Automatically cut off or isolate access if a device does not have critical Falcon settings enabled
Get log events for every access to sensitive resources to detect data exfiltration attempts
SOLUTION
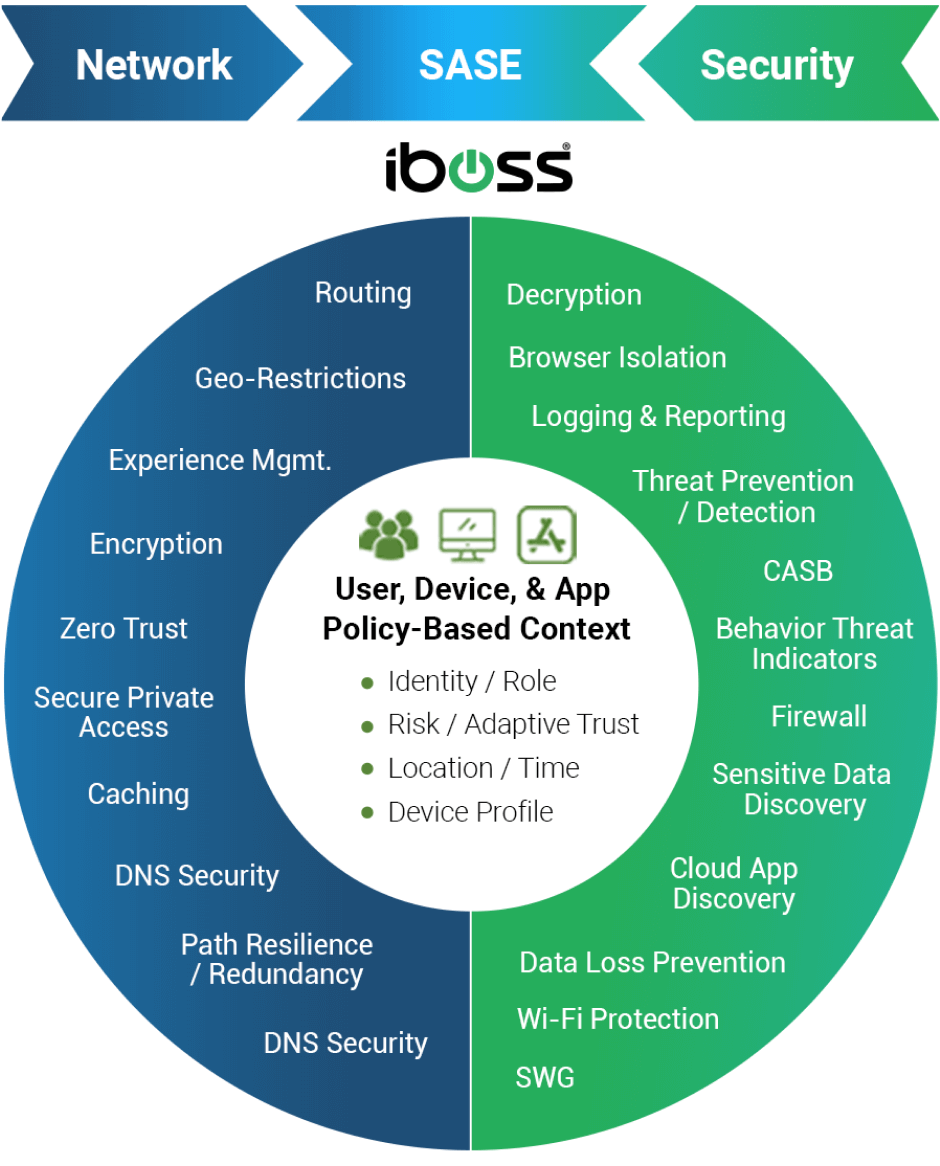
The iboss Zero Trust SASE has been integrated with the CrowdStrike Falcon® platform to deliver automatic actions including the ability to cut off access to sensitive resources when a device becomes infected or is high risk. The iboss Zero Trust SASE provides Zero Trust network access (ZTNA) and security service edge (SSE) capabilities to control access to enterprise resources while applying a cloud access security broker (CASB), malware defense, compliance policies, and data loss prevention (DLP), generating logs for every interaction between users, devices, and sensitive resources. The integration leverages the CrowdStrike Falcon Zero Trust Assessment (ZTA) risk score, which indicates device and user risk, including the likelihood of compromise, and the CrowdStrike CrowdScore®, which assigns scores to incidents according to the incident’s severity level.
The iboss Zero Trust SASE integrates with both Falcon ZTA and CrowdScore to ensure that access to sensitive applications and data can be automatically terminated by iboss when scores reach critical levels. This automation requires no additional human intervention as iboss takes immediate action when CrowdStrike detects risk to protect applications and data from damage. iboss seamlessly allows you to control access to sensitive enterprise resources following the NIST 800-207 Zero Trust Architecture principles, leveraging continuous adaptive access trust algorithms that ingest signals from CrowdStrike to trigger automated actions such as cutting off user access to sensitive resources when a device becomes infected.
KEY CAPABILITIES
- Cut off access to sensitive resources when the CrowdScore indicates a high-risk incident without human intervention by allowing the iboss Zero Trust SASE to close the loop and take action automatically.
- Cut off or isolate access to sensitive resources when a policy leveraging the Falcon ZTA risk score is not met. The iboss Zero Trust SASE leverages its continuous adaptive access Trust Algorithm to take Falcon ZTA signals to add an additional pane of glass in front of those resources using iboss Browser Isolation.
In addition, with iboss’s native browser isolation capabilities, the iboss Zero Trust SASE can automatically add an additional layer of security in front of sensitive apps and data when required. For example, if the Falcon ZTA score indicates a high-risk user or device, the iboss Zero Trust SASE will automatically convert all resource accesses so that they can only be performed through a browser-isolated session. The Falcon ZTA signals are also incorporated into the iboss Zero Trust SASE continuous adaptive access Trust Algorithms, allowing security professionals to adapt access abilities, such as isolating or terminating access, to specific resources depending on which CrowdStrike Falcon capabilities are configured and enabled on a device. The iboss Zero Trust SASE also logs every transaction to every sensitive resource to give the security operation center (SOC) teams the ability to see command and control (C2) infection callbacks and detect potential exfiltration of data from protected applications.
BETTER TOGETHER
PAIN POINTS
Infected Devices Damage Data
When devices are detected to be infected by CrowdStrike, access to sensitive applications and data must be terminated.
Automatically Cut Access
When Infections Occur
The iboss Zero Trust SASE can automatically terminate access based on CrowdStrike incidents that have high-risk CrowdScores.
Non-Compliant Devices are High Risk
When devices are not compliant due to failed CrowdStrike Zero Trust Risk Score assessments, access to sensitive resources should be isolated behind a VDI-like pane-of-glass.
Use Browser Isolation to Separate Data
The iboss Zero Trust SASE includes Browser Isolation to separate non-compliant users from resources based on CrowdStrike Zero Trust Risk Score signals.
Need to Adapt Access Based on Risk
When users and devices access sensitive resources, CASB and DLP controls must be applied that are based on CrowdStrike incidents and Zero Trust Risk Score signals.
Adaptive Access, Security & Logging
The iboss Zero Trust SASE provides continuous adaptive access with a full security stack for access that includes CASB, malware defense, Data Loss Prevention and logging.
USE CASES/BUSINESS VALUE
| Use Case/Challenges | Solution Description | Benefits |
|---|---|---|
| Automatically cut off access to enterprise resources when CrowdStrike Falcon flags a device as infected or compromised. | Leveraging the CrowdScore, the iboss Zero Trust SASE can automatically cut off access to resources when a CrowdStrike Falcon incident reaches a critical level. | Reduce the time between infection and response to minimize the risk of damaging data and applications when a device becomes infected, and reduce overhead for SOCs through automated response actions such as removing access. |
| Automatically cut off or isolate access to enterprise resources when a device is not compliant or becomes high risk based on the Falcon ZTA rating. | Integration with CrowdStrike Falcon enables the iboss Zero Trust SASE to take action when the Falcon ZTA score indicates high risk; actions can include automatically cutting off access to sensitive resources or adding a pane of glass in front of resources using Browser Isolation. | Reduce the risk of breaches, data loss, and attacks due to high-risk users and devices by automatically and quickly changing access abilities to sensitive enterprise-owned applications, data, and services. Easily isolate sessions to prevent the downloading of data from applications when a user or device is deemed risky. |
| Automatically re-enable access to enterprise resources when CrowdStrike Falcon incidents are cleared without adding steps or overhead to the SOC. | The iboss Zero Trust SASE automatically clears incidents triggered by CrowdStrike Falcon when those incidents are cleared within the Falcon dashboard, restoring access to enterprise-owned resources automatically. | Automatically grant or deny access to enterprise-owned applications, data, and services while using existing incident workflows created around the CrowdStrike Falcon dashboards. |
| Add a pane of glass to separate users and devices from sensitive resources when users or devices are non-compliant and fail asset posture checks. | The iboss Zero Trust SASE incorporates Falcon ZTA signals and into the iboss continuous adaptive access Trust Algorithms so that if any CrowdStrike Falcon configuration or posture check fails, access to sensitive resources can be cut off or isolated by the iboss Zero Trust SASE. | Ensure that only compliant users and devices can access sensitive resources to meet compliance requirements for device settings such as having the firewall on, the disk encrypted, or the CrowdStrike Falcon agent actively running on the device. |
| Continuously log for visibility of every user, device, and resource interaction. | The iboss Zero Trust SASE acts as a gatekeeper to all enterprise resources and generates log events for every transaction to applications, data, and services. | Detect data exfiltration attempts and infected device callbacks while users and devices interact with enterprise resources, reducing risk from breaches and data loss. |
| Apply CASB, malware defense, compliance policies, and DLP to every network transaction to complement on-device protection from CrowdStrike. | The iboss Zero Trust SASE inspects all transactions, including looking inside HTTPS connections, to apply security controls, and prevent breaches. | Reduce risk of breaches and data loss by ensuring sensitive data remains within trusted and approved applications. Ensure that data can only be transferred to enterprise-owned devices and those devices running the CrowdStrike Falcon agent. |
TECHNICAL SOLUTION
The iboss Zero Trust SASE connects with the CrowdStrike Falcon platform to deliver a seamless integration for user, asset, and resource protection. The iboss Zero Trust SASE connects to the Falcon platform using APIs to allow information to be exchanged related to the Falcon ZTA risk scores and CrowdStrike CrowdScore incident levels.
The iboss Zero Trust SASE directly aligns with the NIST 800-207 Zero Trust Architecture which allows it to ingest signals from external sources, such as CrowdStrike, and take action based on the inputs received
This is accomplished using iboss’s continuous adaptive access Trust Algorithm that matches that of the NIST 800-207 that can leverage signals generated from iboss in addition to those from other sources, such as CrowdStrike. These inputs are interpreted for each and every request to protected resources and an action is taken such as blocking or isolating access to the sensitive application or data. This results in real-time protection by ensuring that infected or non-compliant devices cannot access applications, data or services as the iboss Zero Trust SASE automatically handles adaptively changing access decisions
NIST SP 800-207
Zero Trust Architecture
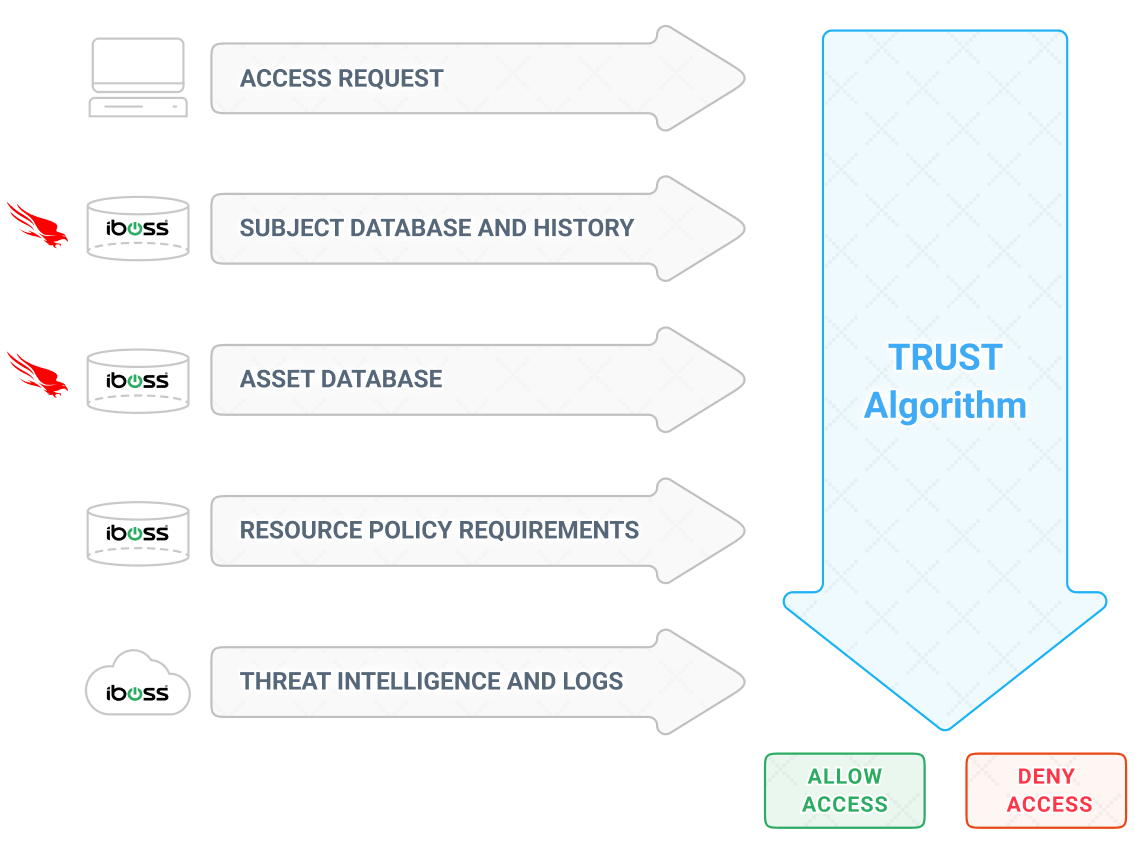
Trust Algorithm Input
Continuous Adaptive Access: CrowdStrike Integration
Integrates CrowdStrike Signals to Cut Access to Sensitive Resources Automatically
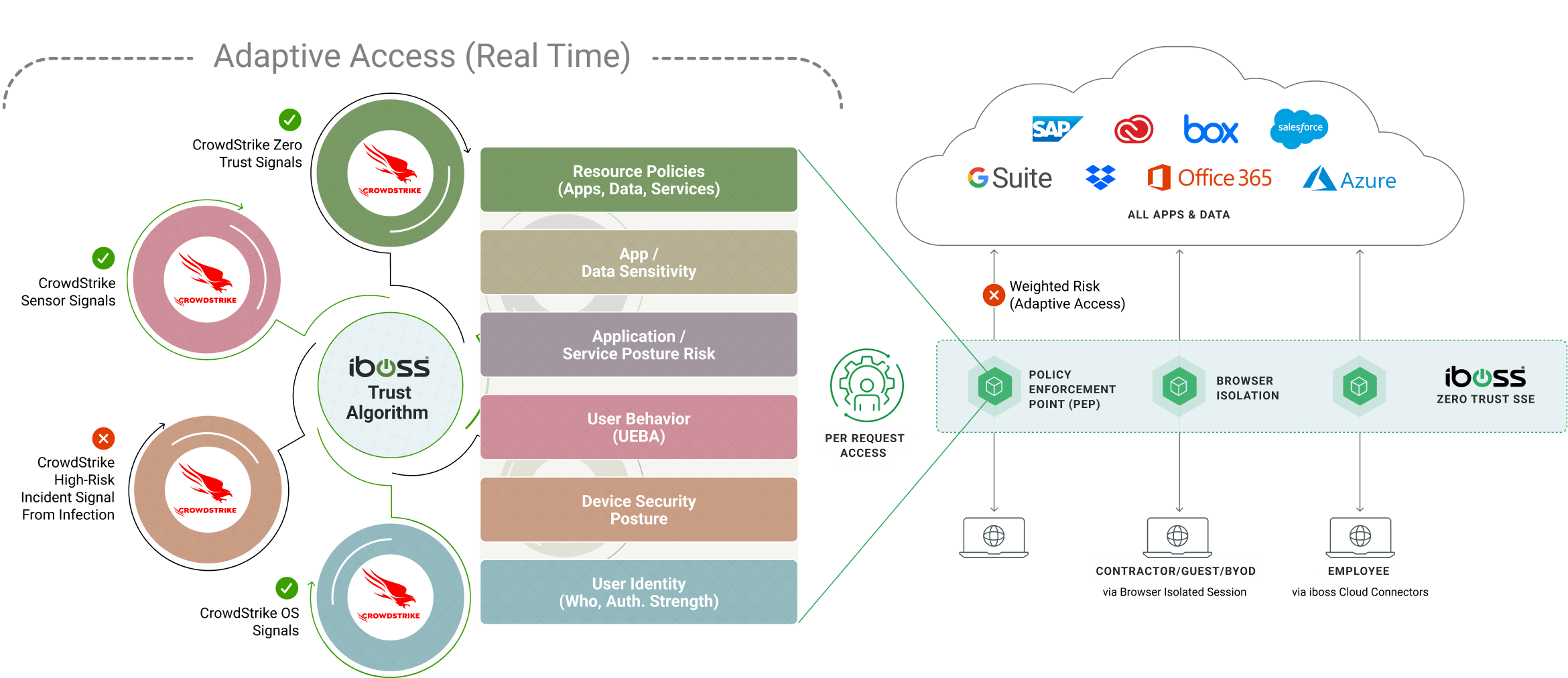
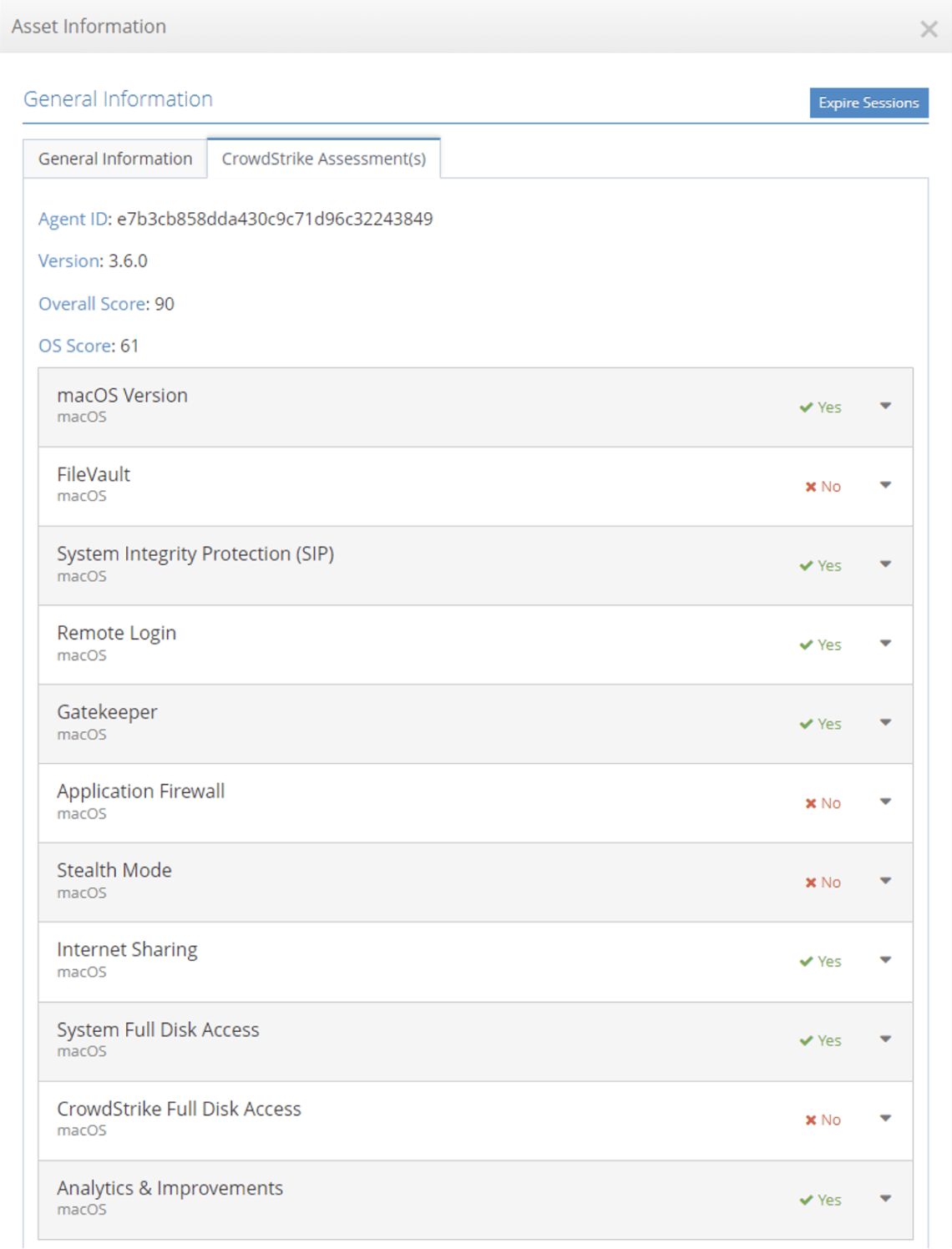
The iboss Zero Trust SASE provides an asset, user, and resource database to track all sensitive resources within the organization. Asset information within the iboss Zero Trust SASE is enriched with Falcon ZTA signals and device posture checks.
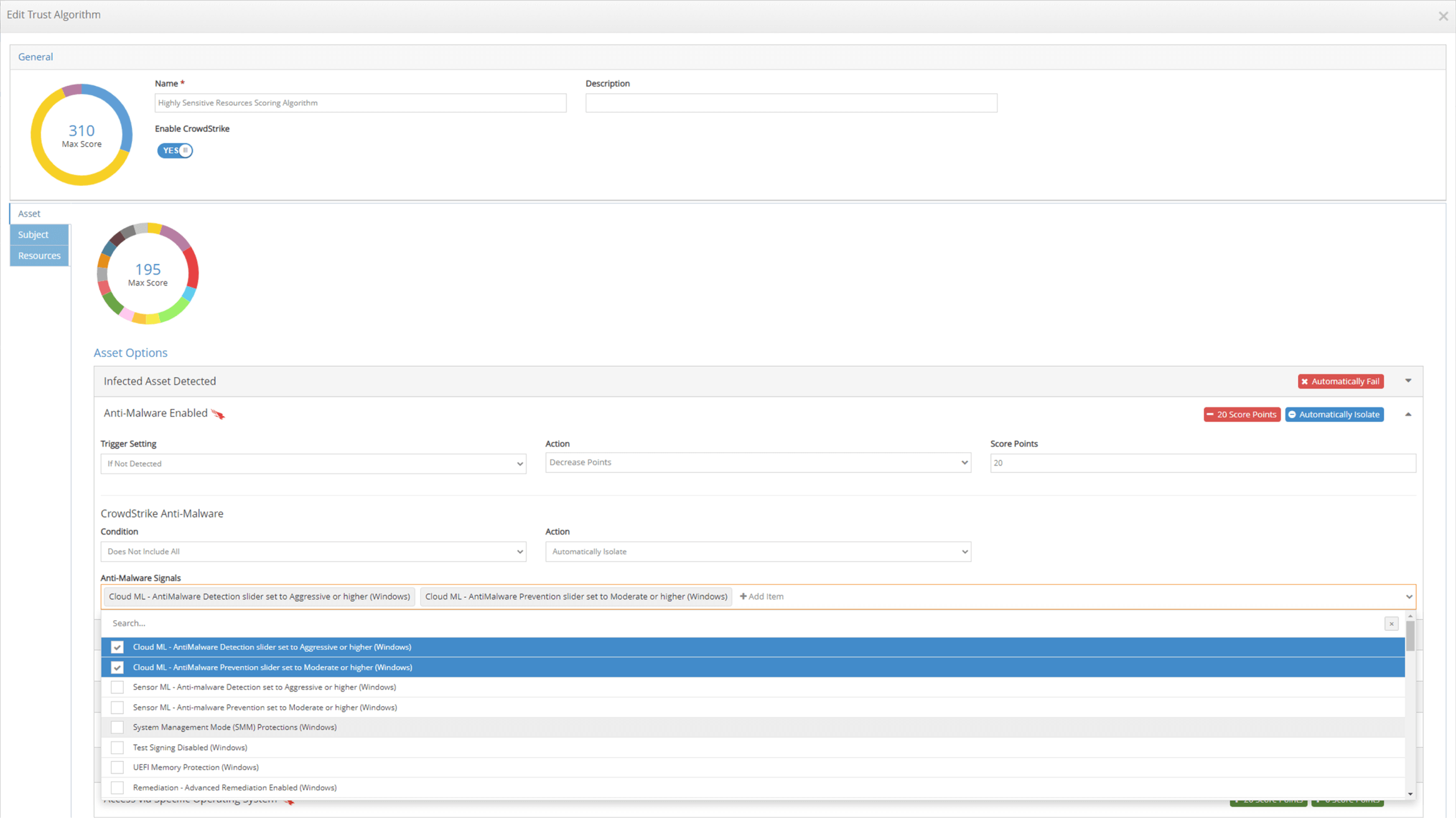
Falcon ZTA signals have been tied to the iboss Zero Trust SASE continuous adaptive access Trust Algorithms, which can take actions, such as cutting off or isolating access, based on CrowdStrike Falcon assessments.
When CrowdStrike Falcon identifies an incident, the iboss Zero Trust SASE can automatically cut off access to sensitive resources by leveraging the resources database, which contains all enterprise-owned resources.
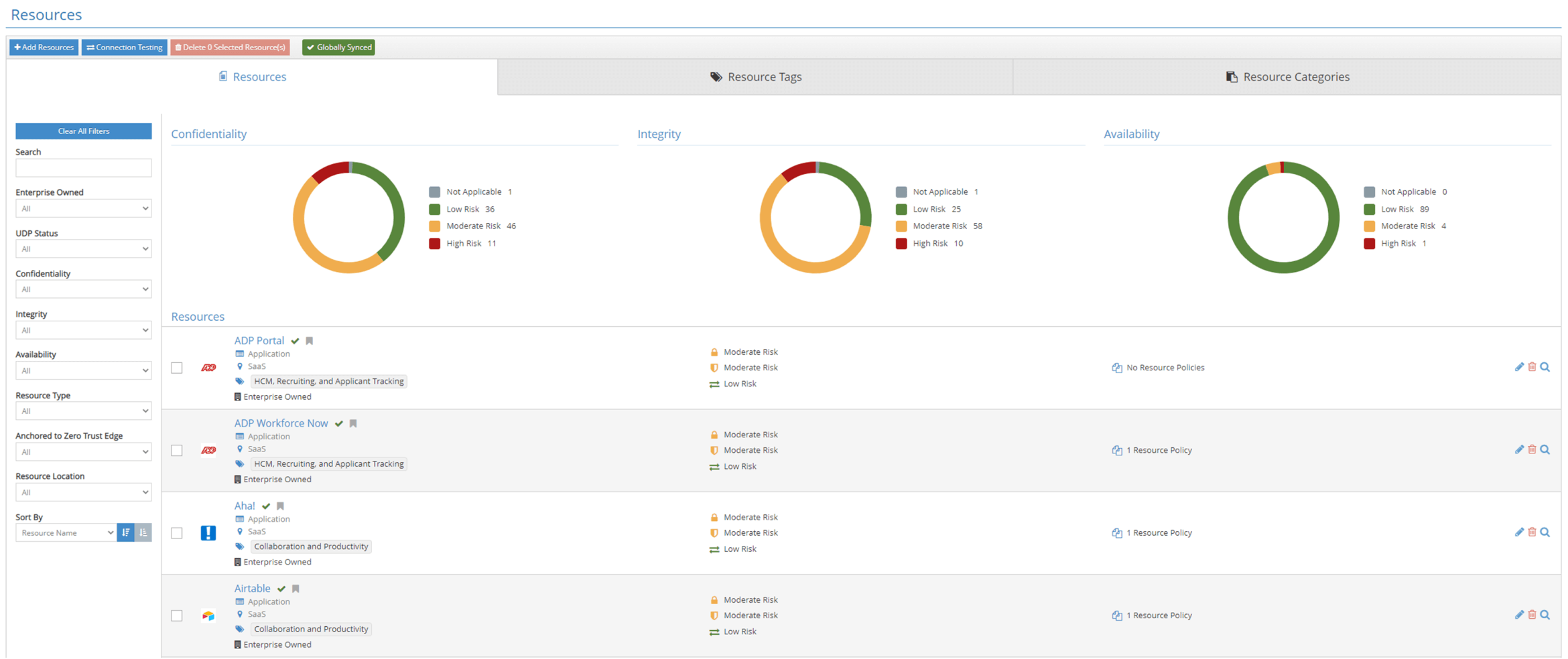
A CrowdStrike Falcon incident that reaches a high-risk CrowdScore level will automatically open iboss incidents, which tie back to the Falcon platform. These incidents will automatically cut off access to enterprise-owned sensitive resources without human intervention, reducing the exposure to damage from ransomware and attackers. The incident CrowdScore level can be configured to trigger an automatic action by iboss.
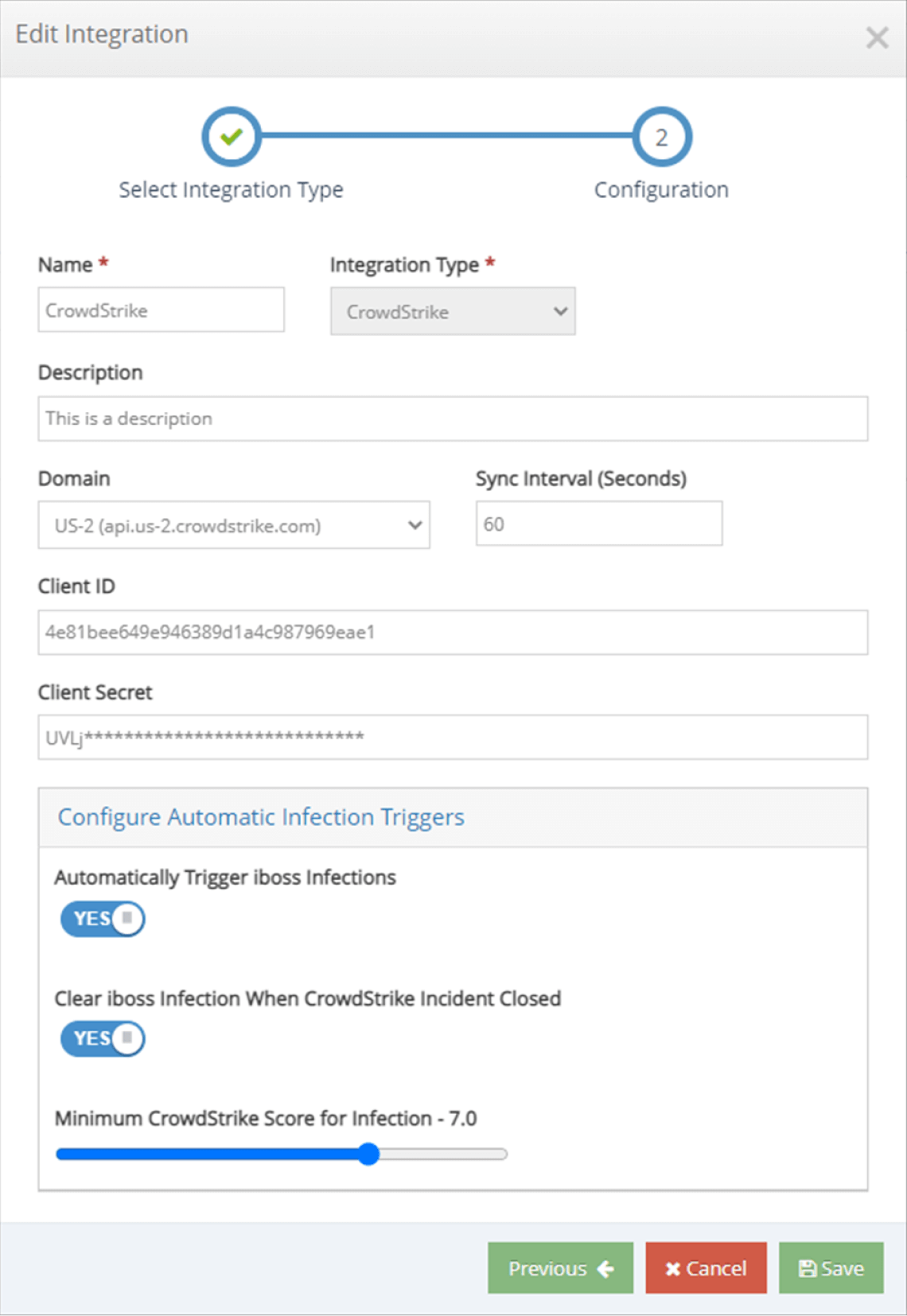
Once the CrowdScore level is reached, an active incident will be created in iboss, immediately cutting off access to sensitive resources.
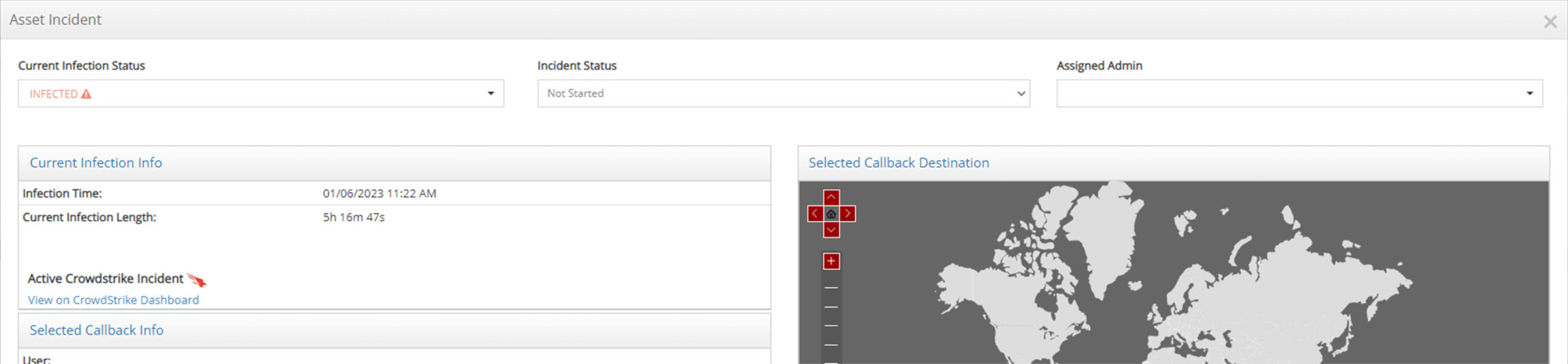
When an incident is closed within the Falcon platform, the associated iboss Zero Trust SASE incident is also closed, automatically restoring access to resources.
A Complete Platform:
ZTNA + Security Service Edge
Providing both Connectivity and Advanced SaaS Security Services
The iboss Zero Trust SASE provides extensive network and security capabilities that completely replace VPN, Proxies, and VDI with ZTNA, Security Service Edge, and Browser Isolation. This increases security, improves the end-user experience, consolidates technology, and substantially reduces costs.
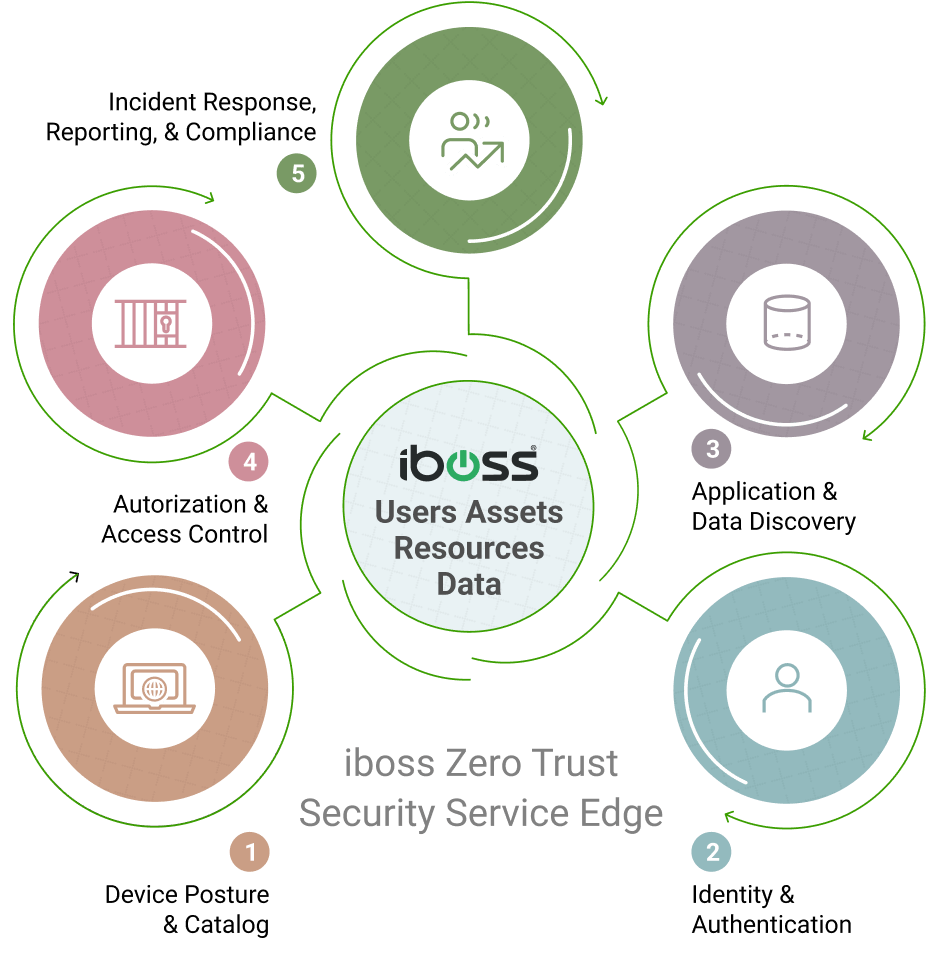
iboss SASE Benefits & Use Cases
Replaces legacy VPN, proxy appliances and Virtual Desktop Infrastructure (VDI) with a single service
Enhances security with inspection of all content including files, data, and cloud application traffic
Connects users to applications in the office automatically
Eliminates proxy and security appliance bloat and renewal costs
Eliminates costly proxy appliance mgmt. overhead
Reduces complexity, cost & operational overhead related to managing network security infrastructure
Connects call center agents, contractors and guests through a pane of glass to prevent data loss
Increased effectiveness of network & security staff
Allows centralized security policies to protect all transactions and sensitive cloud data
Download this Solution Brief Download PDF
