The iboss SASE Cloud Platform is a patented, cloud-delivered security gateway purpose built on a containerized architecture. This approach consolidates security technologies (SWG, CASB, DLP, IPS, Malware Defense, Firewall) into a single unified platform, eliminating appliances in the security stack and reducing the need for VPN while securing any device, regardless of location.
Now let’s go through the setup and configuration steps required to configure the recently announced Reverse Proxy feature available on the iboss Cloud Platform.
The Reverse Proxy functionality further extends the iboss platform for cloud infrastructure security by protecting internal servers and assets by controlling access through a reverse proxy. The reverse proxy allows unmanage devices to access resources over HTTPS using a standard web browser and without the need to have an agent present. In this case, the iboss cloud gateways act as the reverse proxy server with a visible IP address and proxy listening ports. This visible IP address and proxy port allows the user on the unmanaged device to access the protected resources through the iboss cloud.
To setup secure access using the Reverse Proxy feature on the iboss cloud navigate to the Network<<Reverse Proxy Tab as shown in Figure 1 to start the configuration.
Figure 1: Network<<Reverse Proxy Tab.
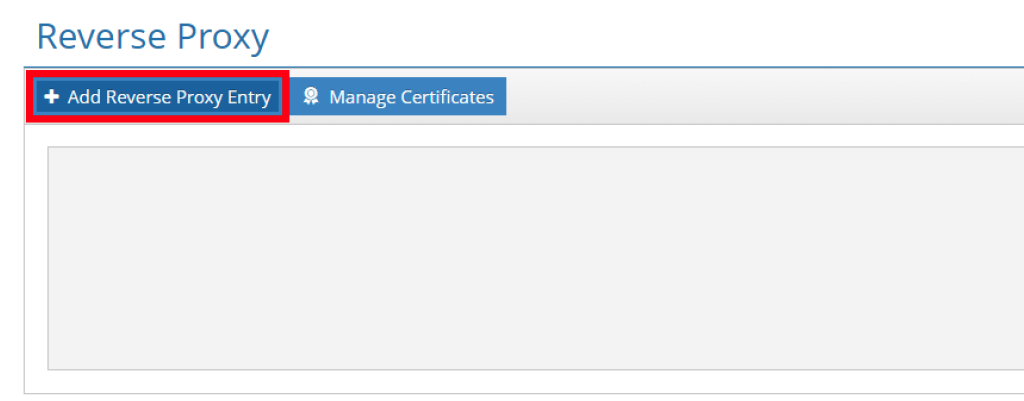
Once you select the Add Reverse Proxy button this will allow you to configure the Reverse Proxy Entry as shown in Figure 2.
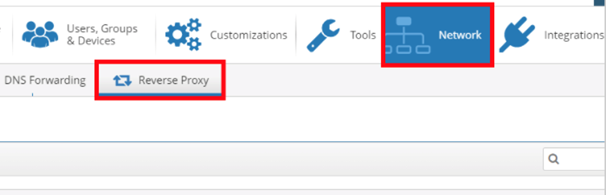
Figure 2: Add Reverse Proxy Entry
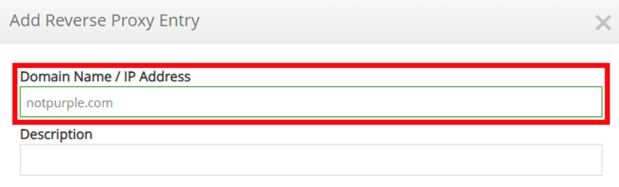
First you will configure the Fully Qualified Domain Name (FQDN) or IP address used as the public entry point for the Reverse Proxy as shown in Figure 3. Optionally you can configure a description for the entry.
Figure 3: Add Domain Name/ IP address Field
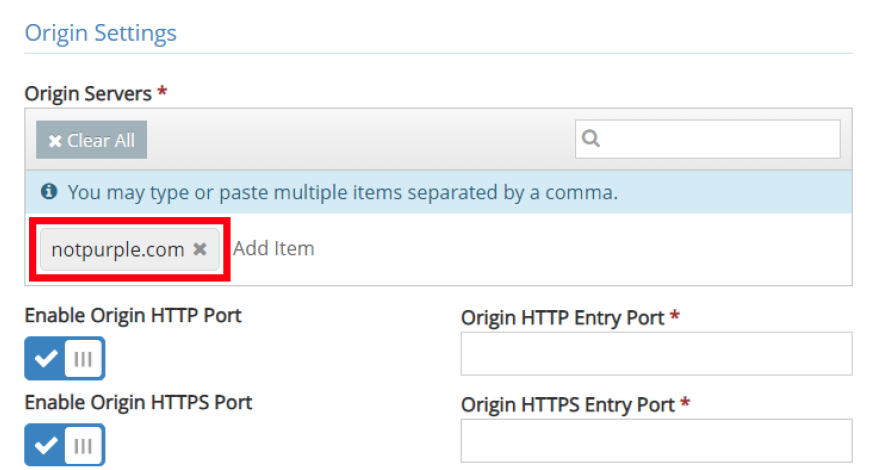
Next you will configure the Origin Servers list. This will determine the pool of servers used for the reverse proxy configuration and will redirect to one of the listed servers when a request is matched. Additionally, you can set the Origin Server Entry ports for HTTP and HTTPS as shown in Figure 4.
Figure 4: Origin Server Settings
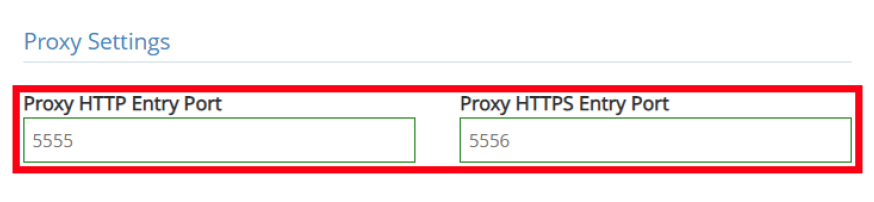
The Proxy Entry Ports for HTTP and HTTPS allow you to configure the desired proxy listening ports for incoming requests to the Reverse Proxy configuration, as shown in Figure 5. These will be the intended port destinations from the unmanaged device to the iboss cloud.
Figure 5: Proxy HTTP/HTTPS Entry Port Settings
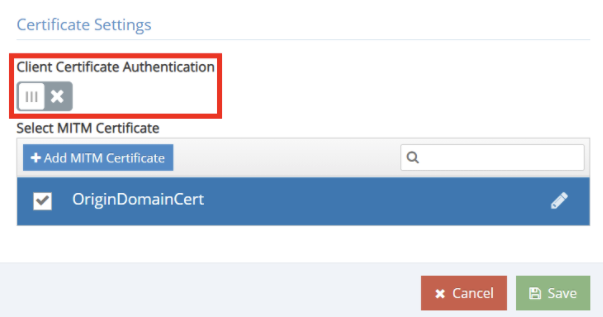
Additionally, a client-side certificate can be used for authorization for access to the Origin Servers. This can be done by enabling Client Certificate Authentication and then selecting the SSL Certificate to be used for the Entry as show in Figure 6. Importing Certificates to be used for the Reserve Proxy Entries can be done from the Reverse Proxy<<Manage Certificates tab. Our recommendation is to implement a user-based authentication method on the Origin Server, which can properly interface with the reverse proxy entry.
Figure 6: Client Certificate Settings
For more information on the iboss Cloud Platform, visit: www.iboss.com/sase.
